Mirai Co-Author Gets 6 Months Confinement, $8.6M in Fines for Rutgers Attacks

Credit to Author: BrianKrebs| Date: Fri, 26 Oct 2018 20:36:21 +0000
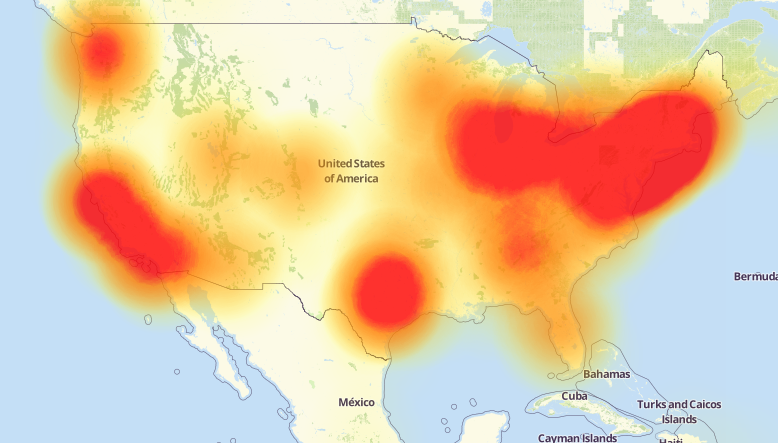
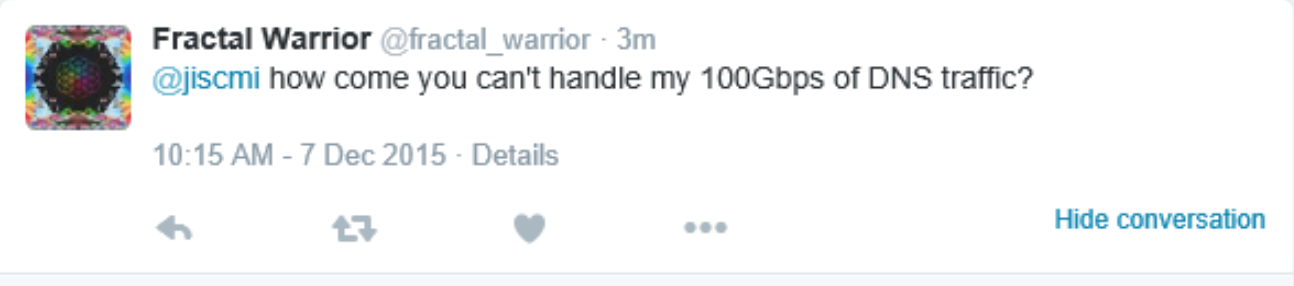
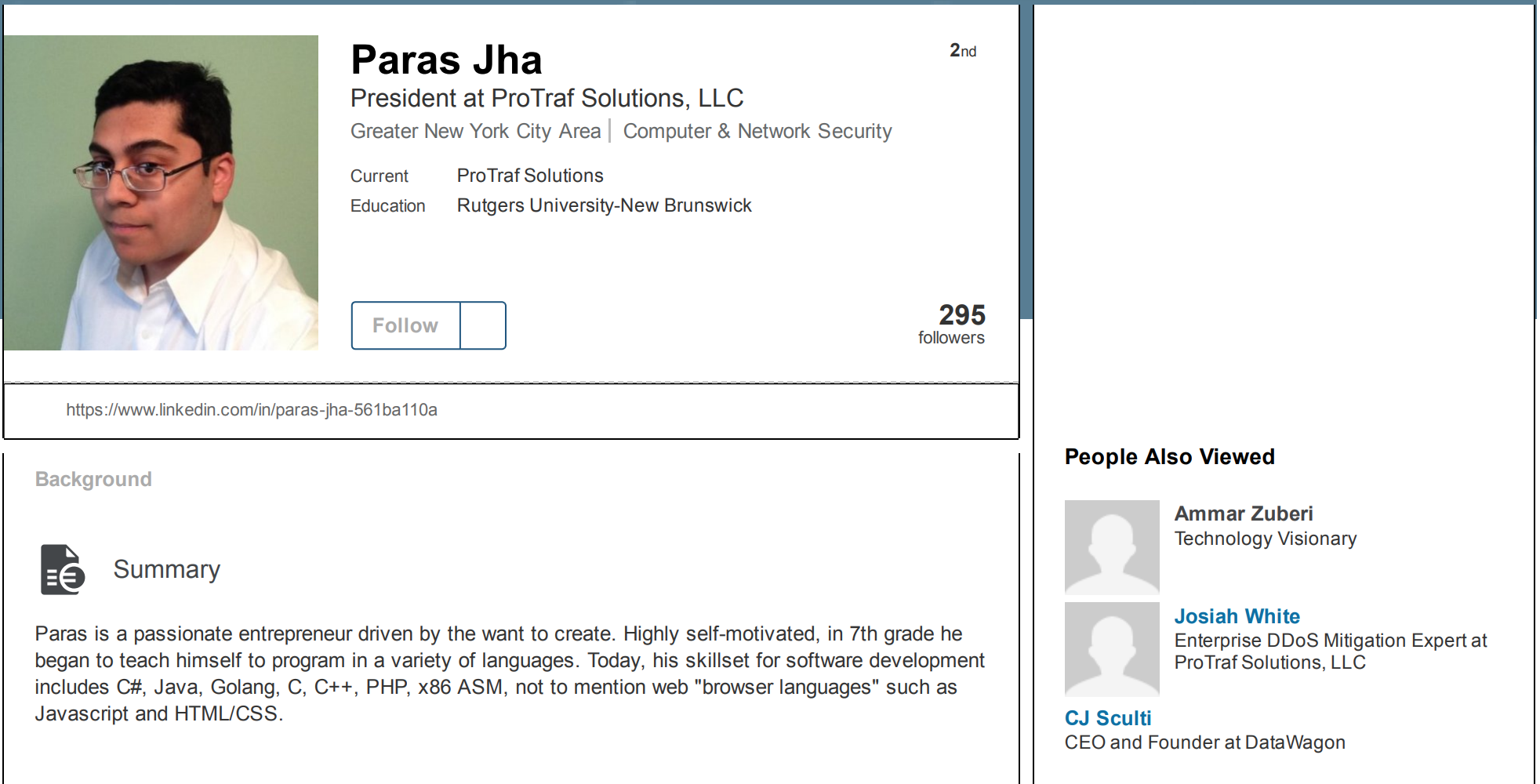
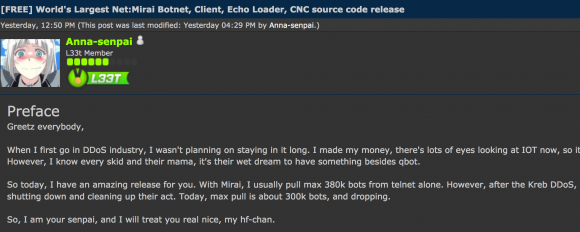
The convicted co-author of the highly disruptive Mirai botnet malware strain has been sentenced to 2,500 hours of community service, six months home confinement, and ordered to pay $8.6 million in restitution for repeatedly using Mirai to take down Internet services at Rutgers University, his former alma mater.
Read more