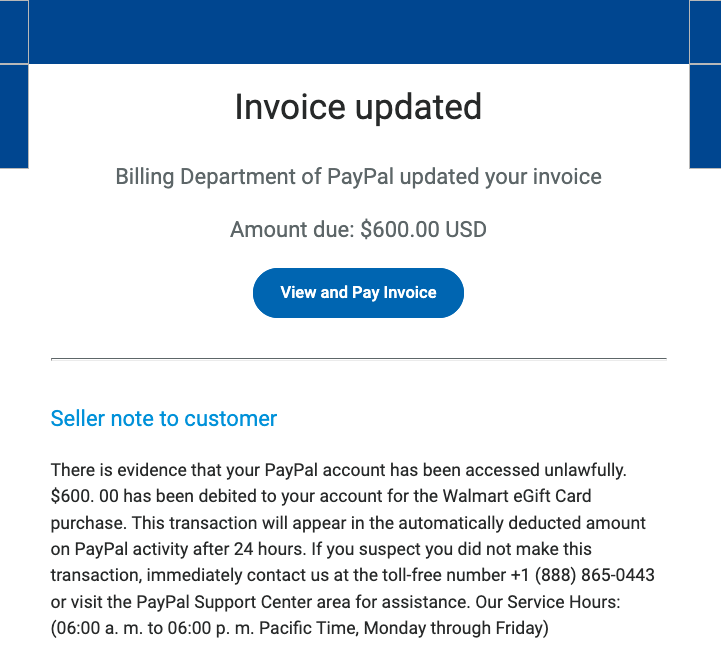
Watch out for this triple threat PayPal phish
Categories: News Tags: PayPal Tags: scam Tags: phish Tags: phishing Tags: fraud Tags: email Tags: telephone Tags: call Tags: send money Tags: notification We take a look at a PayPal phish which comes complete with multiple ways to pull the wool over your eyes. |
The post Watch out for this triple threat PayPal phish appeared first on Malwarebytes Labs.
Read more