Rapid Response: The Squirrelwaffle Incident Guide

Credit to Author: Tilly Travers| Date: Tue, 15 Feb 2022 13:00:10 +0000
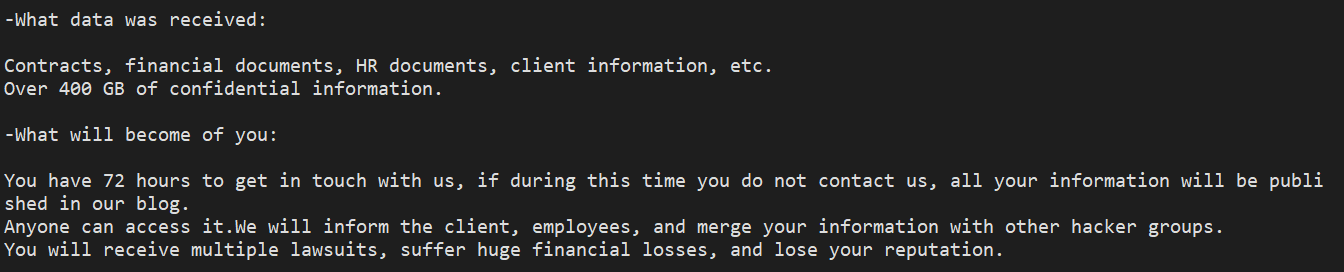
Squirrelwaffle is a malicious dropper or loader used to deliver other malware onto target systems. This guide shows Security Operations Centers (SOCs) and Incident Response Teams how to detect and respond to the presence of Squirrelwaffle on the network
Read more