Fake DDoS services set up to trap cybercriminals
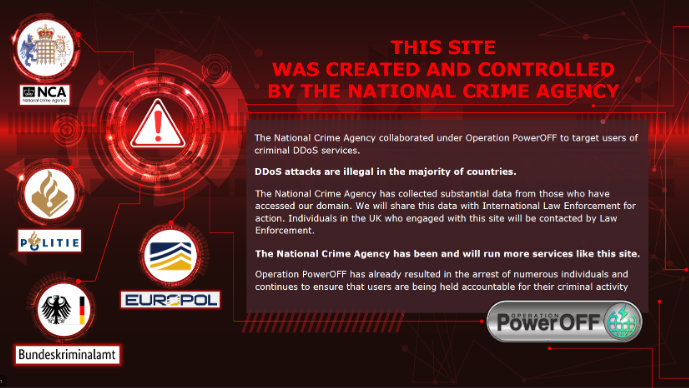
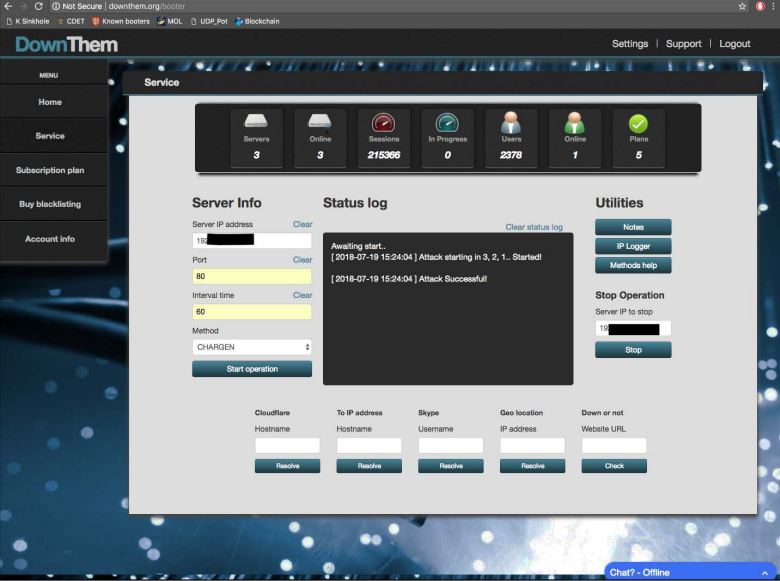
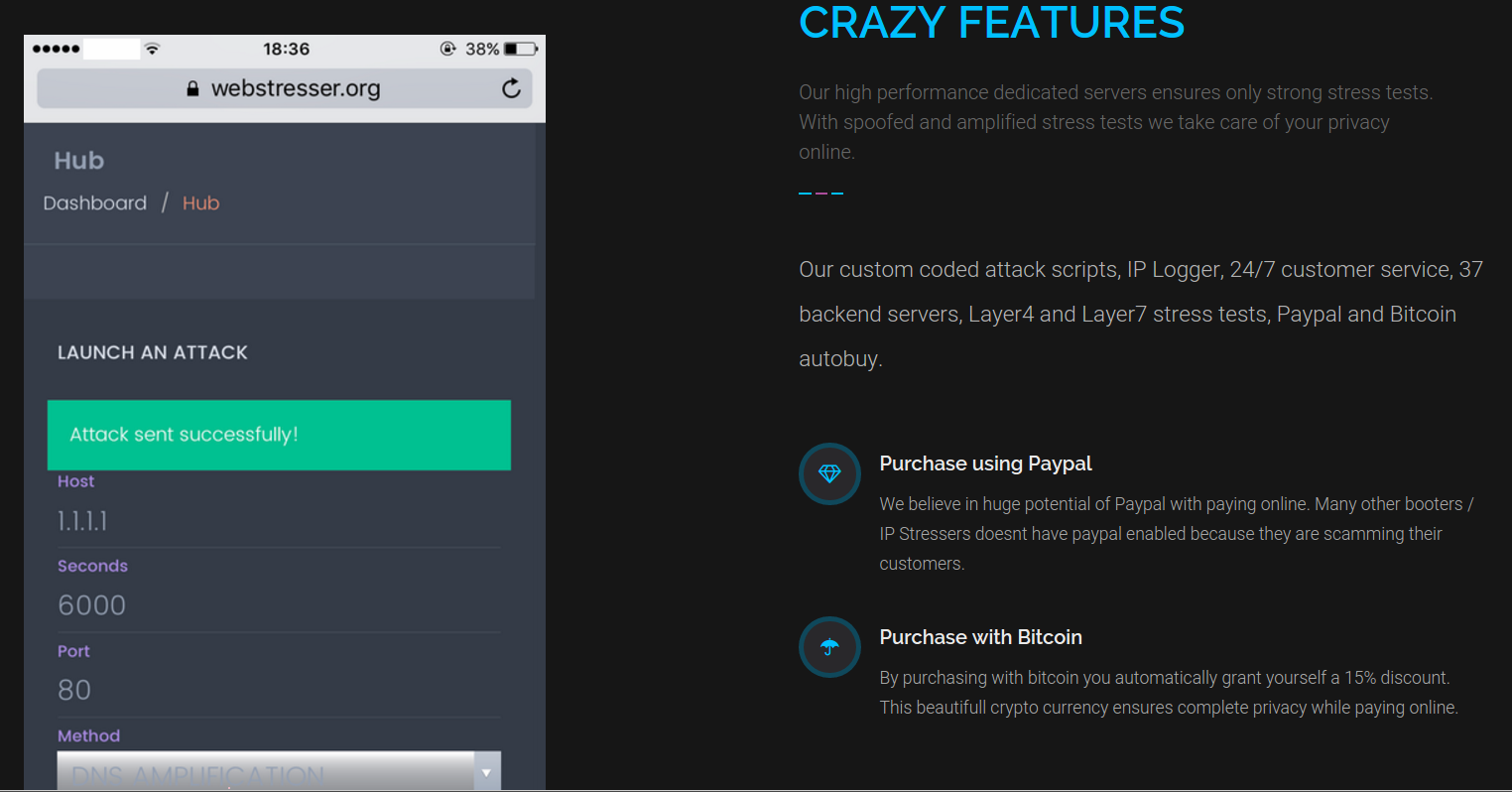
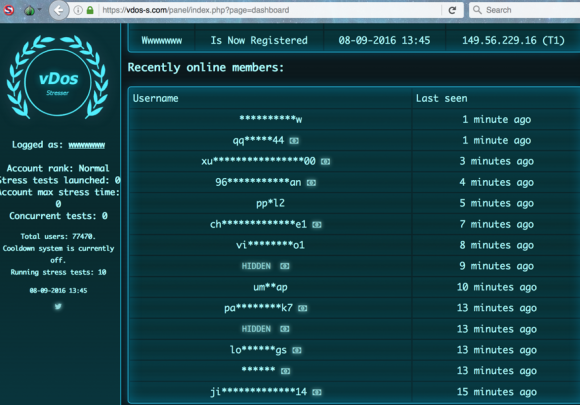
Categories: News Tags: NCA Tags: national crime agency Tags: DDoS Tags: distributed denial of service Tags: booter Tags: underground The British National Crime Agency has been setting up fake DDoS services to teach people a lesson in what not to do online. |
The post Fake DDoS services set up to trap cybercriminals appeared first on Malwarebytes Labs.
Read more