.US Harbors Prolific Malicious Link Shortening Service
Credit to Author: BrianKrebs| Date: Tue, 31 Oct 2023 13:26:55 +0000
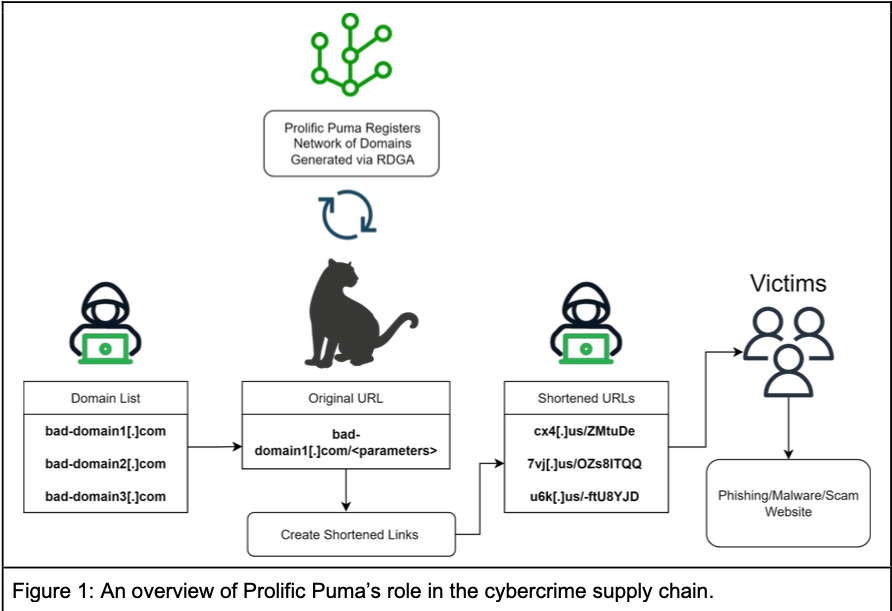
The top-level domain for the United States — .US — is home to thousands of newly-registered domains tied to a malicious link shortening service that facilitates malware and phishing scams, new research suggests. The findings come close on the heels of a report that identified .US domains as among the most prevalent in phishing attacks over the past year.
Read more