Jetzt für alle: Per API-Analysetool die SophosLabs-Expertise anzapfen
Credit to Author: Jörg Schindler| Date: Wed, 04 Dec 2019 08:16:44 +0000
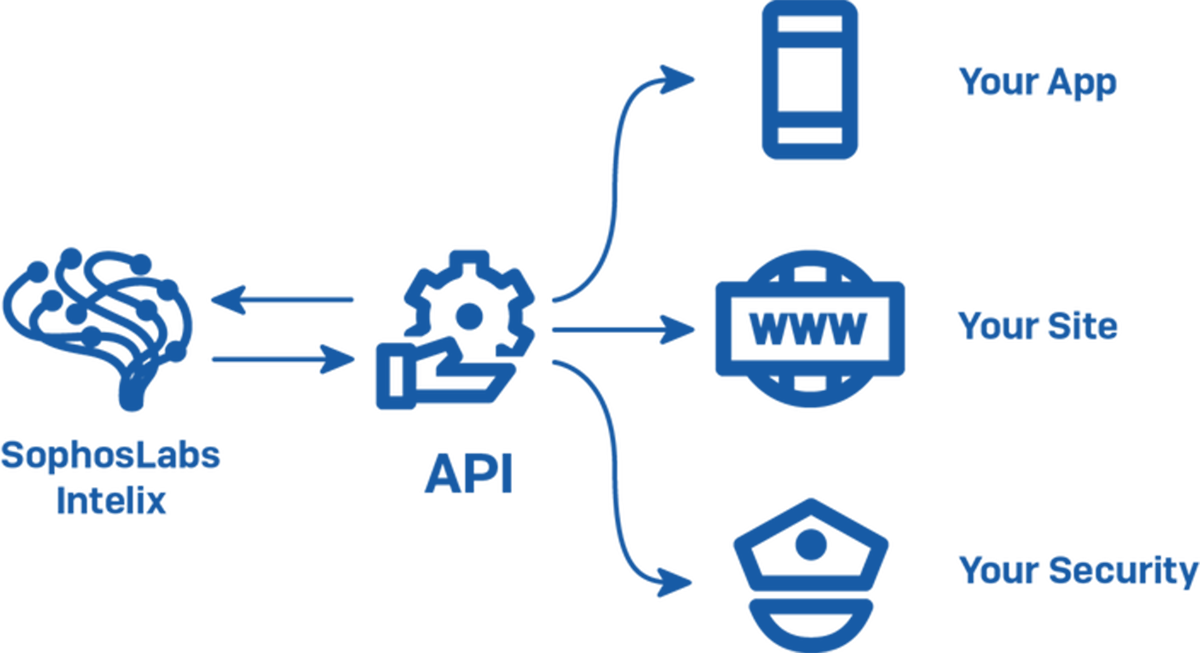
Heute einmal eine Interessante Sache in eigener Sache: Sophos hat diese Woche den Start von SophosLabs Intelix bekannt gegeben. Die Cloud-basierte Threat-Intelligence– und Analyseplattform ermöglicht es Anwendern, sicherere Anwendungen zu entwerfen. Programmierer haben via APIs Zugriff auf die Intelix Plattform, um mit aktuellem Cyber-Bedrohungs-Know-how Dateien, URLs und IP-Adressen zu bewerten. Auf der Plattform aktualisiert und […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/OEe6Goz7ts0″ height=”1″ width=”1″ alt=””/>
Read more




