How I learned to stop worrying and love ‘grey hat’ tools
Credit to Author: Tad Heppner| Date: Tue, 25 Feb 2020 13:45:19 +0000
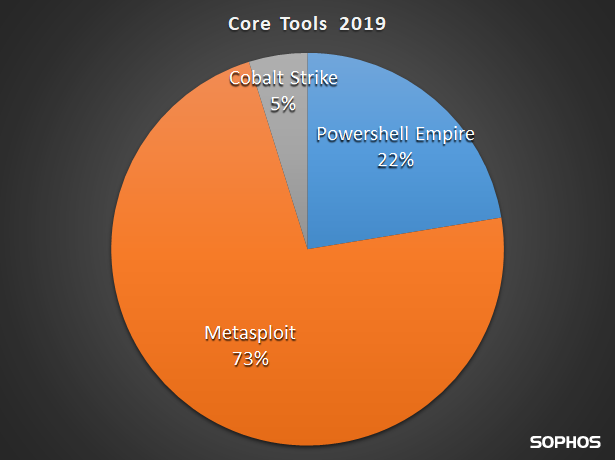
A comprehensive security solution needs a sense of subtlety: not all machine code lends itself to be classified easily as malicious. As with most things in life, there’s a grey area in malware detection that includes hacking tools, poorly designed or easily exploitable applications, or borderline adware that provides little benefit to the unfortunate user […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/TR1pieWZO1k” height=”1″ width=”1″ alt=””/>
Read more