How ephemeral metadata may cause real problems
Credit to Author: Igor Kuksov| Date: Fri, 10 Mar 2017 14:00:25 +0000
The most dangerous data leaks are the ones people don’t even know about.
Read MoreRSS Reader for Computer Security Articles
Credit to Author: Igor Kuksov| Date: Fri, 10 Mar 2017 14:00:25 +0000
The most dangerous data leaks are the ones people don’t even know about.
Read More
Credit to Author: Lucas Mearian| Date: Fri, 10 Mar 2017 03:01:00 -0800
The revelation through Wikileaks that the CIA has explored hacking vehicle computer control systems should concern consumers, particularly as more and more cars and trucks roll off assembly lines with autonomous features.
“I think it’s a legitimate concern considering all of the computers being added to cars,” said Kit Walsh, a staff attorney with the privacy group Electronic Frontier Foundation (EFF). “There’s no reason the CIA or other intelligence agencies or bad actors couldn’t use those vulnerabilities to hurt people.
To read this article in full or to leave a comment, please click here

Credit to Author: Michael Kan| Date: Thu, 09 Mar 2017 19:06:00 -0800
WikiLeaks plans to share details about what it says are CIA hacking tools with the tech companies so that software fixes can be developed.
But will software companies want it?
The information WikiLeaks plans to share comes from 8,700-plus documents it says were stolen from an internal CIA server. If the data is classified — and it almost certainly is — possessing it would be a crime.
That was underlined on Thursday by White House press secretary Sean Spicer, who advised tech vendors to consider the legal consequences of receiving documents from WikiLeaks.
To read this article in full or to leave a comment, please click here

Credit to Author: Michael Kan| Date: Thu, 09 Mar 2017 19:06:00 -0800
WikiLeaks plans to share details about what it says are CIA hacking tools with the tech companies so that software fixes can be developed.
But will software companies want it?
The information WikiLeaks plans to share comes from 8,700-plus documents it says were stolen from an internal CIA server. If the data is classified — and it almost certainly is — possessing it would be a crime.
That was underlined on Thursday by White House press secretary Sean Spicer, who advised tech vendors to consider the legal consequences of receiving documents from WikiLeaks.
To read this article in full or to leave a comment, please click here

Credit to Author: Lucian Constantin| Date: Thu, 09 Mar 2017 13:32:00 -0800
Intel Security has released a tool that allows users to check if their computer’s low-level system firmware has been modified and contains unauthorized code.
The release comes after CIA documents leaked Tuesday revealed that the agency has developed EFI (Extensible Firmware Interface) rootkits for Apple’s Macbooks. A rootkit is a malicious program that runs with high privileges — typically in the kernel — and hides the existence of other malicious components and activities.
The documents from CIA’s Embedded Development Branch (EDB) mention an OS X “implant” called DerStarke that includes a kernel code injection module dubbed Bokor and an EFI persistence module called DarkMatter.
To read this article in full or to leave a comment, please click here
Credit to Author: noam| Date: Thu, 09 Mar 2017 08:34:23 +0000
Vulnerability Summary The following advisory describes an arbitrary file content disclosure vulnerability found in GoAhead web server. The GoAhead web server is present on multiple embedded devices, from IP Cameras to Printers and other embedded devices. The vulnerability allows a remote unauthenticated attacker to disclose the content of the file being accessed. As most embedded … Continue reading SSD Advisory – Over 100K IoT Cameras Vulnerable to Source Disclosure
Read MoreCredit to Author: Lily Hay Newman| Date: Thu, 09 Mar 2017 17:34:40 +0000

The big question is if and when Julian Assange follows through on his latest blockbuster promise. The post Psst, Silicon Valley. WikiLeaks Wants to Help You Fight the CIA appeared first on WIRED.
Read More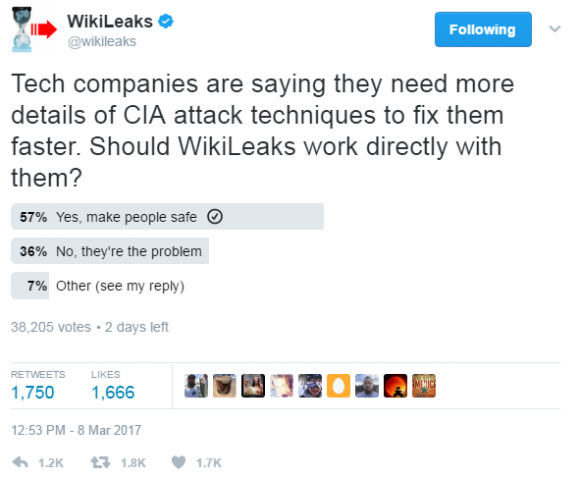
Credit to Author: BrianKrebs| Date: Thu, 09 Mar 2017 18:10:30 +0000
When WikiLeaks on Tuesday dumped thousands of files documenting hacking tools used by the U.S. Central Intelligence Agency, many feared WikiLeaks would soon publish a trove of so-called “zero days,” the actual computer code that the CIA uses to exploit previously unknown flaws in a range of software and hardware products used by consumers and businesses. But on Thursday, WikiLeaks editor-in-chief Julian Assange promised that his organization would work with hardware and software vendors to fix the security weaknesses prior to releasing additional details about the flaws.
Read More