Schools in Alabama warn parents about Blue Whale ‘suicide game’ app
Credit to Author: Darlene Storm| Date: Wed, 10 May 2017 10:44:00 -0700
A “suicide game” presented in an app sounds like an urban legend or something from a horror flick, but unfortunately the “Blue Whale Challenge” is real. In fact, police and school districts have issued warnings about the app and even Instagram serves up a warning after searching for the #bluewhalechallenge.
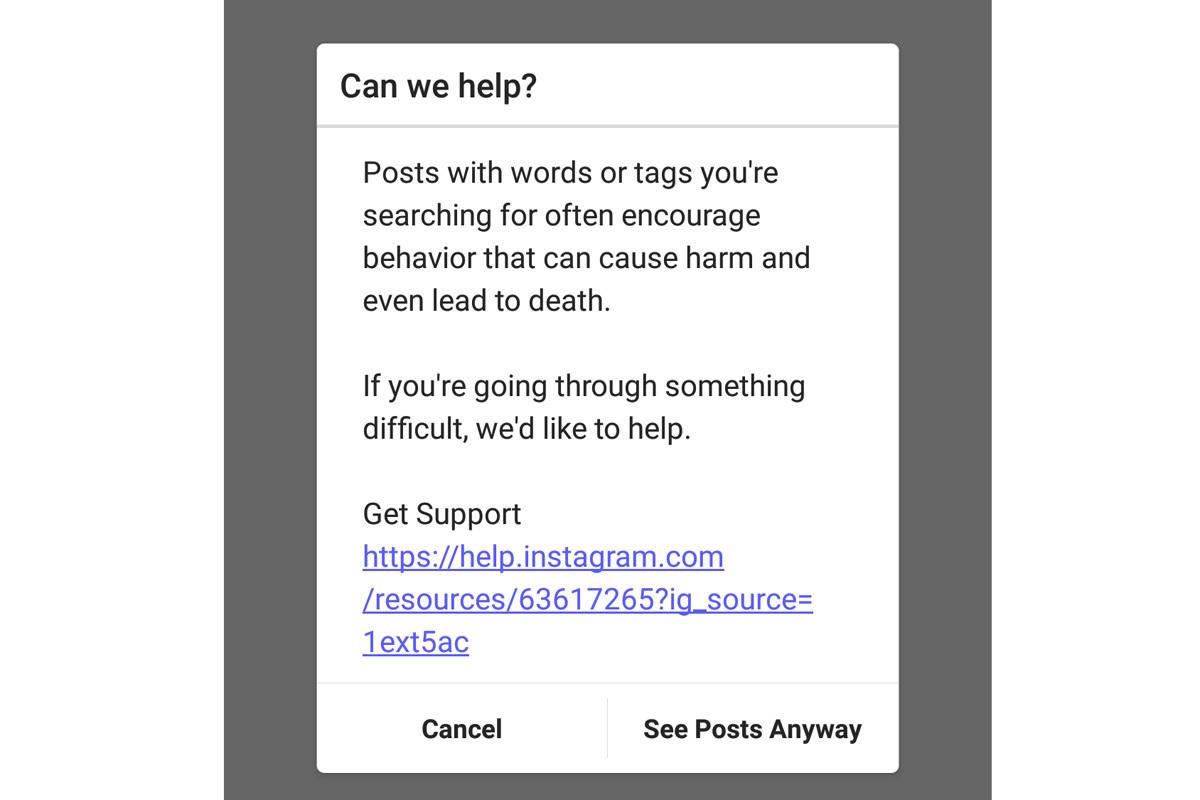 IDG
IDGVulnerable young people are the targets for Blue Whale. Once the app is downloaded onto a phone, it reportedly hacks the phone and harvests the user’s information. In the Blue Whale Challenge, a group administrator – also referenced as a mentor or master – gives a young person a task to complete each day for 50 days. If a person balks at the daily task, then the personal information which was stolen is used as a form of blackmail as in do this or else your private information will be released or your family threatened. The task on the last day is to commit suicide. This is supposedly winning the game.
To read this article in full or to leave a comment, please click here



 When we talk about healthcare breaches, people usually remember the big-name incidents: Anthem, Premera, Banner Health, and so on. Yet in reality there’s a huge number of smaller providers who are in the hackers’ sights and maybe don’t have the resources or expertise to adequately defend themselves. With ransomware threatening to shut down systems and…
When we talk about healthcare breaches, people usually remember the big-name incidents: Anthem, Premera, Banner Health, and so on. Yet in reality there’s a huge number of smaller providers who are in the hackers’ sights and maybe don’t have the resources or expertise to adequately defend themselves. With ransomware threatening to shut down systems and…
 The Randstad Group is currently in the process of consolidating and centralizing its IT infrastructure across 30 IT departments, and will be providing service to more than 40 operating countries across four continents. To ensure the new infrastructure will have optimal security the company selected Trend Micro as its cloud security solution partner for the…
The Randstad Group is currently in the process of consolidating and centralizing its IT infrastructure across 30 IT departments, and will be providing service to more than 40 operating countries across four continents. To ensure the new infrastructure will have optimal security the company selected Trend Micro as its cloud security solution partner for the…