Inside an Epic Hotel Room Hacking Spree

Credit to Author: Andy Greenberg| Date: Tue, 29 Aug 2017 11:00:00 +0000
A vulnerability in hotel keycard locks was a security disaster—and a huge opportunity for one burglar.
Read MoreRSS Reader for Computer Security Articles

Credit to Author: Andy Greenberg| Date: Tue, 29 Aug 2017 11:00:00 +0000
A vulnerability in hotel keycard locks was a security disaster—and a huge opportunity for one burglar.
Read More
Credit to Author: Bill Hogan| Date: Tue, 29 Aug 2017 07:00:00 +0000
Threat intelligence is a necessary part of threat detection, yet is often ignored. Learn why financial institutions must focus on building their architecture for automated threat intelligence.
Read More
Credit to Author: Matthew Gault| Date: Mon, 28 Aug 2017 21:11:30 +0000
All profits from the book will go to the Council on American-Islamic Relations.
Read More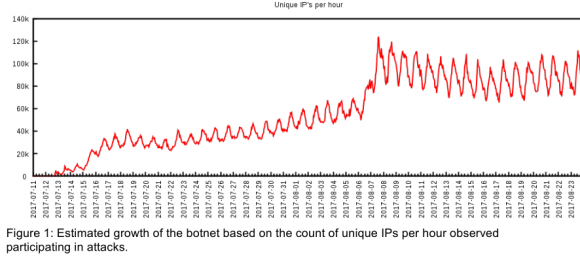
Credit to Author: BrianKrebs| Date: Mon, 28 Aug 2017 14:06:08 +0000
A half dozen technology and security companies — some of them competitors — issued the exact same press release today. This unusual level of cross-industry collaboration caps a successful effort to dismantle ‘WireX,’ an extraordinary new crime machine comprising tens of thousands of hacked Android mobile devices that was used this month to launch a series of massive cyber attacks. Experts involved in the takedown warn that WireX marks the emergence of a new class of attack tools that are more challenging to defend against and thus require broader industry cooperation to defeat.
Read More
Credit to Author: BrianKrebs| Date: Mon, 28 Aug 2017 02:46:42 +0000
More online services than ever now offer two-step authentication — requiring customers to complete a login using their phone or other mobile device after supplying a username and password. But with so many services relying on your mobile for that second factor, there has never been more riding on the security of your mobile account. Below are some tips to ensure your mobile device (or, more specifically, your mobile carrier) isn’t the weakest link in your security chain.
Read MoreCredit to Author: Keith Chambers| Date: Mon, 28 Aug 2017 19:45:22 +0000
Pharmaceutical companies in the market today need to comply with a huge array of regulations –in most regions, manufacturers must follow Good Manufacturing Practice (GMP), as well as Good Documentation… Read more »
The post Three Ways to Improve Regulatory Compliance in Pharmaceutical Manufacturing appeared first on Schneider Electric Blog.
Read MoreCredit to Author: David Clement| Date: Mon, 28 Aug 2017 19:00:33 +0000
 On August 28th at VMworld 2017 in Las Vegas, VMware announced initial availability for their unique offering called ‘VMware Cloud on AWS’ allowing customers to run VMware workloads on the AWS cloud. This means customers can take advantage of agile cloud infrastructure all the while maintaining their familiar VMware tools, skill sets and architecture framework…
On August 28th at VMworld 2017 in Las Vegas, VMware announced initial availability for their unique offering called ‘VMware Cloud on AWS’ allowing customers to run VMware workloads on the AWS cloud. This means customers can take advantage of agile cloud infrastructure all the while maintaining their familiar VMware tools, skill sets and architecture framework…

Credit to Author: Zack Thoutt| Date: Mon, 28 Aug 2017 19:41:58 +0000
A programmer taught an artificial intelligence how to write the next entry in George R.R. Martin’s A Song of Ice and Fire series.
Read More