How hackers have improved their BEC attack methods
Credit to Author: Trend Micro| Date: Wed, 30 Aug 2017 17:56:22 +0000
 Let’s take a closer look into BEC threats and how hackers have improved this attack method.
Let’s take a closer look into BEC threats and how hackers have improved this attack method.
RSS Reader for Computer Security Articles
Credit to Author: Trend Micro| Date: Wed, 30 Aug 2017 17:56:22 +0000
 Let’s take a closer look into BEC threats and how hackers have improved this attack method.
Let’s take a closer look into BEC threats and how hackers have improved this attack method.
Credit to Author: Employee Voices| Date: Fri, 25 Aug 2017 12:10:09 +0000
Written by Guest Blogger, Neena Sharma Have you ever wondered what is the true purpose of human life? This is one question each of us might have thought about at… Read more »
The post Realize your True Potential at Schneider Electric appeared first on Schneider Electric Blog.
Read More
Credit to Author: Editor| Date: Wed, 30 Aug 2017 17:03:40 +0000
The Sophos Central Dashboard lets you manage sub-estates and share licenses <img alt=”” border=”0″ src=”https://pixel.wp.com/b.gif?host=news.sophos.com&blog=834173&post=42426&subd=sophos&ref=&feed=1″ width=”1″ height=”1″ /><img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/-6zxa39uKRo” height=”1″ width=”1″ alt=””/>
Read More
Credit to Author: Sam Gustin| Date: Wed, 30 Aug 2017 17:41:43 +0000
“This is not the Soviet Union: Americans deserve a meaningful choice in their local news,” a lawmaker said of the proposed Sinclair-Tribune merger.
Read More
Credit to Author: Jordan Pearson| Date: Wed, 30 Aug 2017 17:13:38 +0000
“This is probably the best phishing scam I’ve ever seen.”
Read More
Credit to Author: Emanuel Maiberg| Date: Wed, 30 Aug 2017 16:52:56 +0000
The esports industry has never been bigger, but Africa is being left behind.
Read More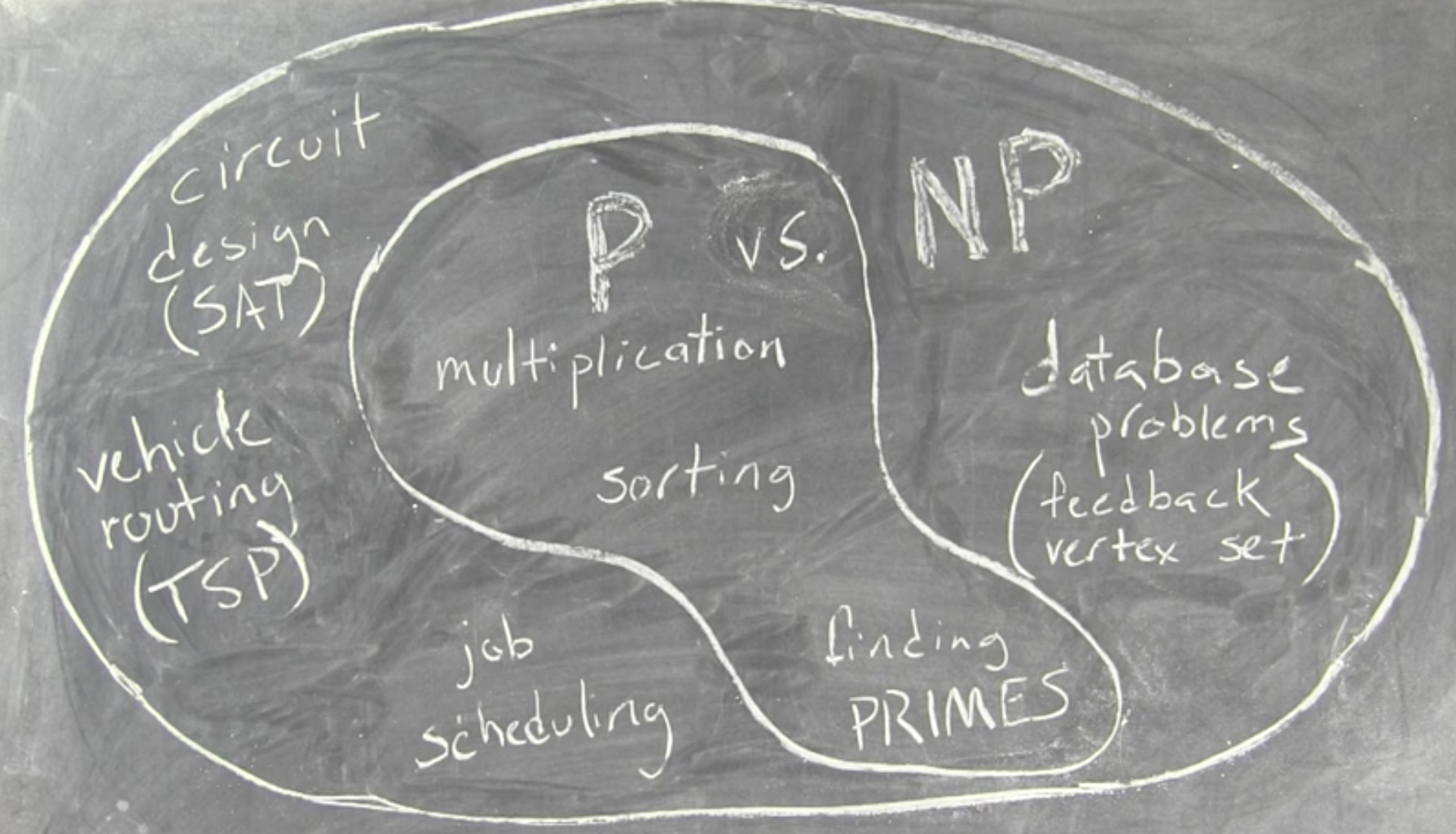
Credit to Author: Daniel Mützel| Date: Wed, 30 Aug 2017 16:03:11 +0000
Norbert Blum’s solve for the infamous ‘P vs NP’ problem “passes many filters of seriousness,” but does it hold up?
Read More