Women’s EuroArabian expedition arrives at the North Pole
Credit to Author: Sarah Pike| Date: Thu, 03 May 2018 08:52:24 +0000
The team, led by veteran polar explorer Felicity Aston, met with Eugene Kaspersky on arrival at the North Pole.
Read MoreRSS Reader for Computer Security Articles
Credit to Author: Sarah Pike| Date: Thu, 03 May 2018 08:52:24 +0000
The team, led by veteran polar explorer Felicity Aston, met with Eugene Kaspersky on arrival at the North Pole.
Read MoreCredit to Author: Greg Young| Date: Thu, 03 May 2018 14:00:46 +0000

with contributing author, William J. Malik, CISA | VP, Infrastructure Strategies The date for General Data Protection Regulation (GDPR) compliance is three months away, yet many organizations, especially those outside Europe, remain unprepared. It turns out that the experiences from other privacy compliance regulations are less helpful than assumed, but the best lessons learned may be…
The post What HIPAA and Other Compliance Teaches Us About the Reality of GDPR appeared first on .
Read More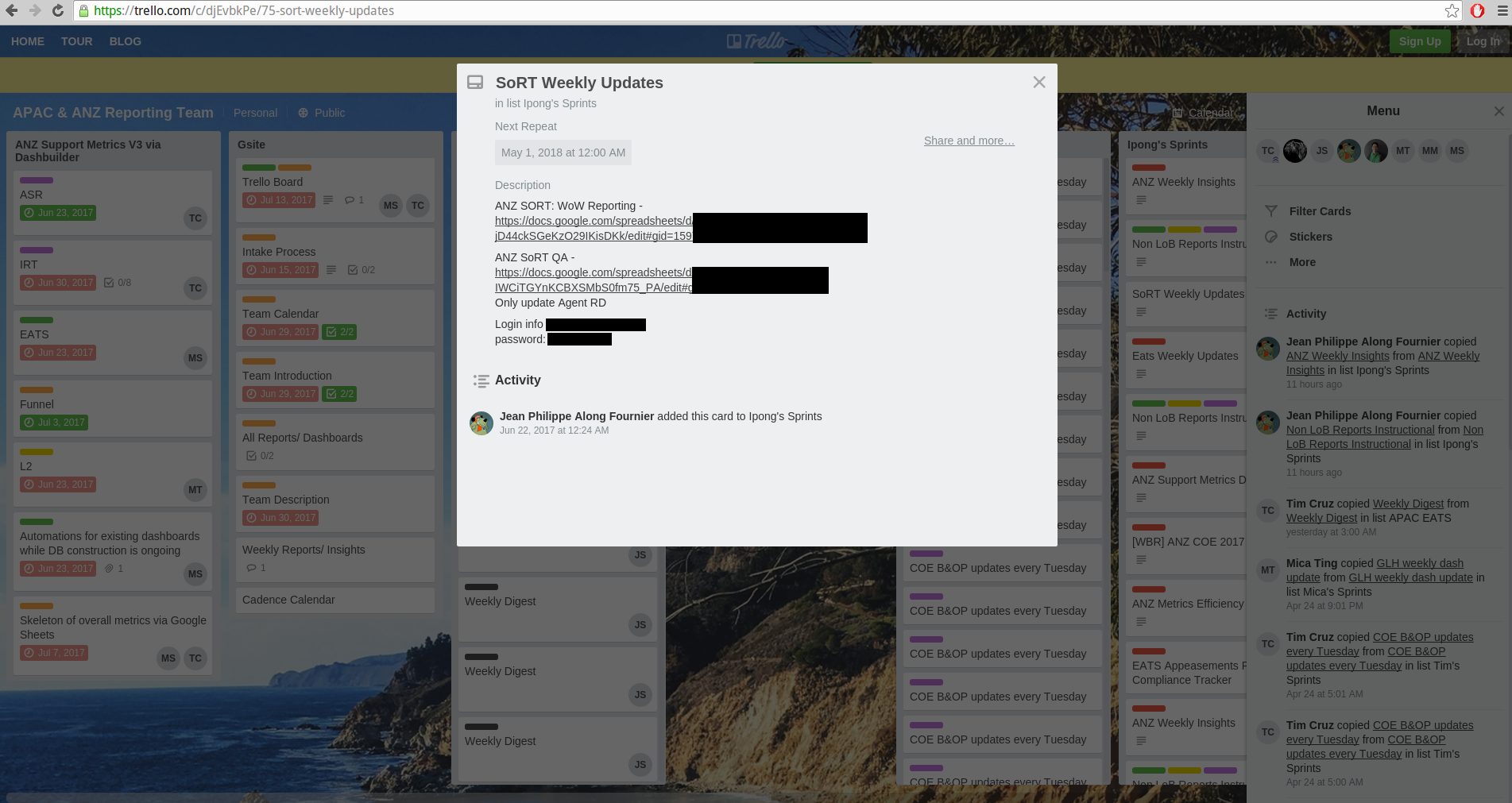
Credit to Author: BrianKrebs| Date: Wed, 02 May 2018 19:26:47 +0000
Storing passwords in plaintext online is never a good idea, but it’s remarkable how many companies have employees who are doing just that using online collaboration tools like Trello.com. Last week, KrebsOnSecurity notified a host of companies that employees were using Trello to share passwords for sensitive internal resources. Among those put at risk by such activity included an insurance firm, a state government agency and ride-hailing service Uber.com.
Read MoreCredit to Author: Steve Neville| Date: Wed, 02 May 2018 18:35:20 +0000

As we’ve discussed over the last 7 weeks in our video case study series, the General Data Protection Regulation (GDPR) impacts many different areas of our company, including our employees, customers, and partners. The GDPR also mandates the use of state-of-the-art security, which, as a leader in security solutions, means that our products are being…
The post State-of-the-art Security: The role of technology in the journey to GDPR compliance appeared first on .
Read MoreCredit to Author: Trend Micro| Date: Wed, 02 May 2018 18:10:06 +0000

In addition to legitimate uses and mining, cybercriminals have also taken advantage of cryptocurrency, and this use is shaping the current threat environment.
The post How cryptocurrency is shaping today’s threat environment appeared first on .
Read MoreCredit to Author: Robert Bunger| Date: Wed, 02 May 2018 17:42:17 +0000
With a 17% attendance increase at the 2018 Open Compute Summit last month, the increasing market interest in all things open compute came through loud and clear. Previously, the unique… Read more »
The post How to Prepare Your Colocation with Open Compute Solutions appeared first on Schneider Electric Blog.
Read MoreCredit to Author: Jeremy Kivi| Date: Wed, 02 May 2018 04:30:04 +0000
Across multiple industries, companies are looking to drive efficiency and profitability; in many cases, part of this strategy is tied to leveraging digital transformation. Over the last few months I… Read more »
The post Summarizing an Asset Reliability Strategy for Midstream Pipeline Operators appeared first on Schneider Electric Blog.
Read More
Credit to Author: Issie Lapowsky| Date: Wed, 02 May 2018 18:21:15 +0000
The troubled data firm, which improperly accessed the data of up to 87 million Facebook users, has ceased operations.
Read More