LifeLock Bug Exposed Millions of Customer Email Addresses
Credit to Author: BrianKrebs| Date: Wed, 25 Jul 2018 22:20:46 +0000
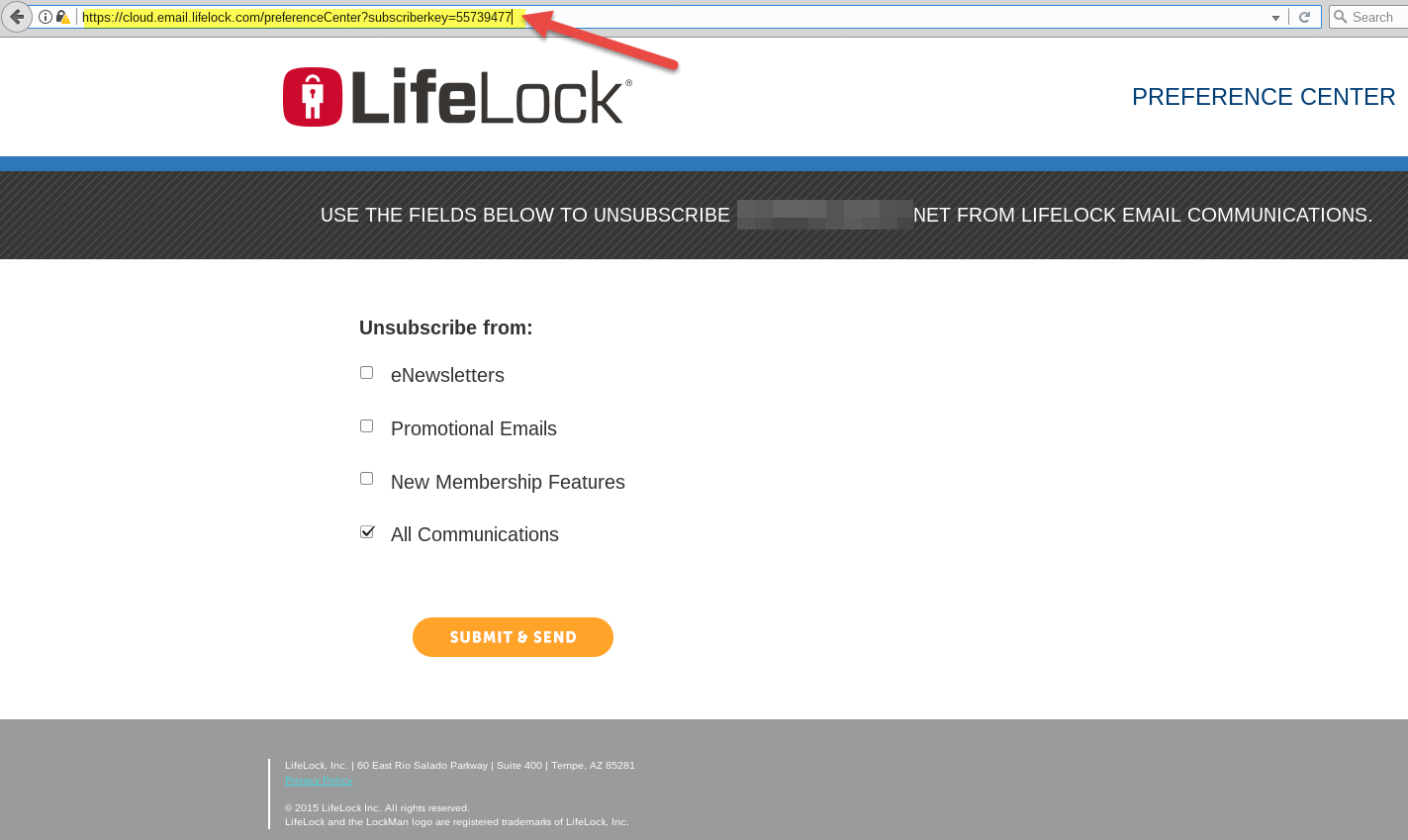
Identity theft protection firm LifeLock — a company that’s built a name for itself based on the promise of helping consumers protect their identities online — may have actually exposed customers to additional attacks from ID thieves and phishers. The company just fixed a vulnerability on its Web site that allowed anyone with a Web browser to index email addresses associated with millions of customer accounts, or to unsubscribe users from all communications from the company. The upshot of this weakness is that cyber criminals could harvest the data and use it in targeted phishing campaigns that spoof LifeLock’s brand. Of course, phishers could spam the entire world looking for LifeLock customers without the aid of this flaw, but nevertheless the design of the company’s site suggests that whoever put it together lacked a basic understanding of Web site authentication and security. The upshot of this weakness is that cyber criminals could harvest the data and use it in targeted phishing campaigns that spoof LifeLock’s brand. Of course, phishers could spam the entire world looking for LifeLock customers without the aid of this flaw, but nevertheless the design of the company’s site suggests that whoever put it together it lacked a basic understanding of authentication and security.
Read More