What businesses should know about our partners
Credit to Author: Nikolay Pankov| Date: Tue, 29 Jan 2019 13:51:30 +0000
Our new partner program: What customers should know about Kaspersky United.
Read MoreRSS Reader for Computer Security Articles
Credit to Author: Nikolay Pankov| Date: Tue, 29 Jan 2019 13:51:30 +0000
Our new partner program: What customers should know about Kaspersky United.
Read MoreCredit to Author: Trend Micro| Date: Tue, 29 Jan 2019 14:00:23 +0000

Maintaining protection over an enterprise’s critical data, systems and assets is a continual uphill battle. Not only are chances good that the business’s digital footprint is growing through new applications, but hackers are also constantly bolstering their capabilities to silently breach platforms and maintain a presence under the radar of the IT team. In the…
The post Informing Your Security Posture: How Cybercriminals Blend into the Background appeared first on .
Read More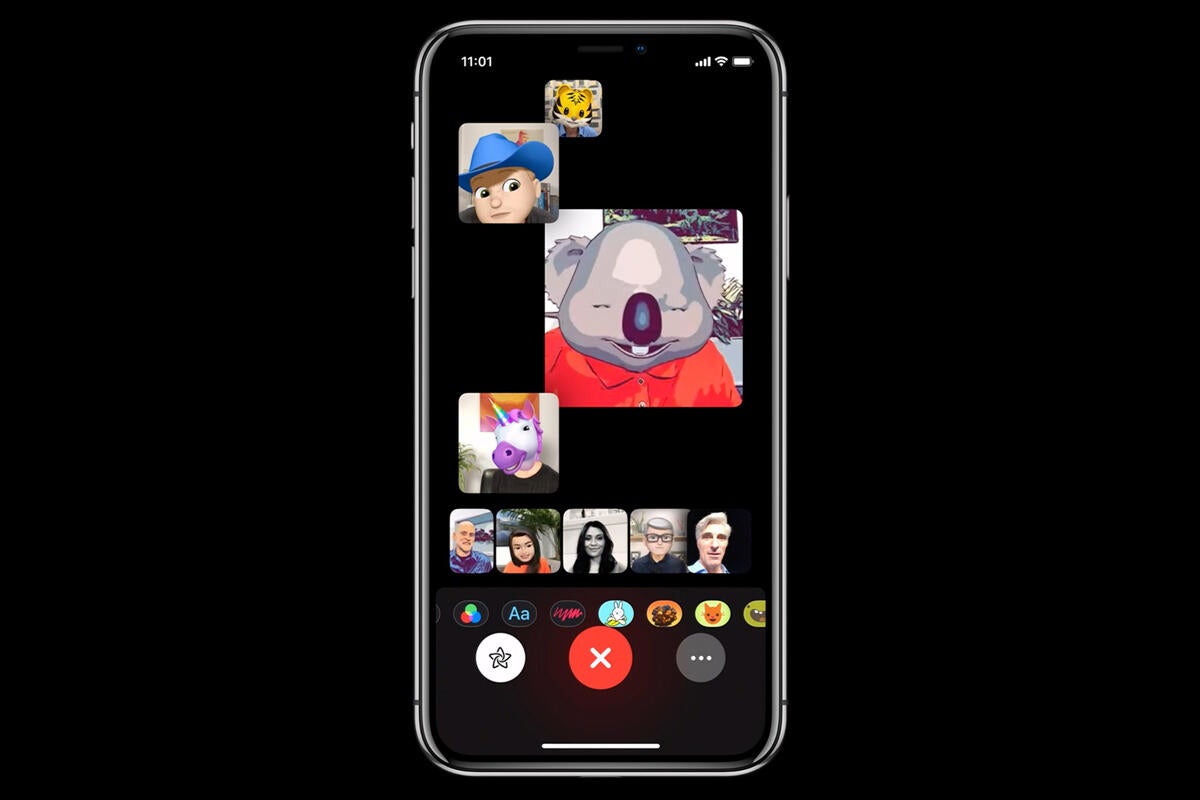
Credit to Author: Jonny Evans| Date: Tue, 29 Jan 2019 05:30:00 -0800
Apple has disabled Group FaceTime following discovery of a flaw that could potentially let people hear audio from other people’s devices without permission. What’s going on and what can you do about it?
A 9to5Mac report based on a video published to Twitter by @BmManski revealed that this flaw lets a user listen to audio captured using another person’s device before they accept or reject the call requesting a FaceTime chat. The problem only affects iOS devices running iOS 12.1 or later (pending an update).
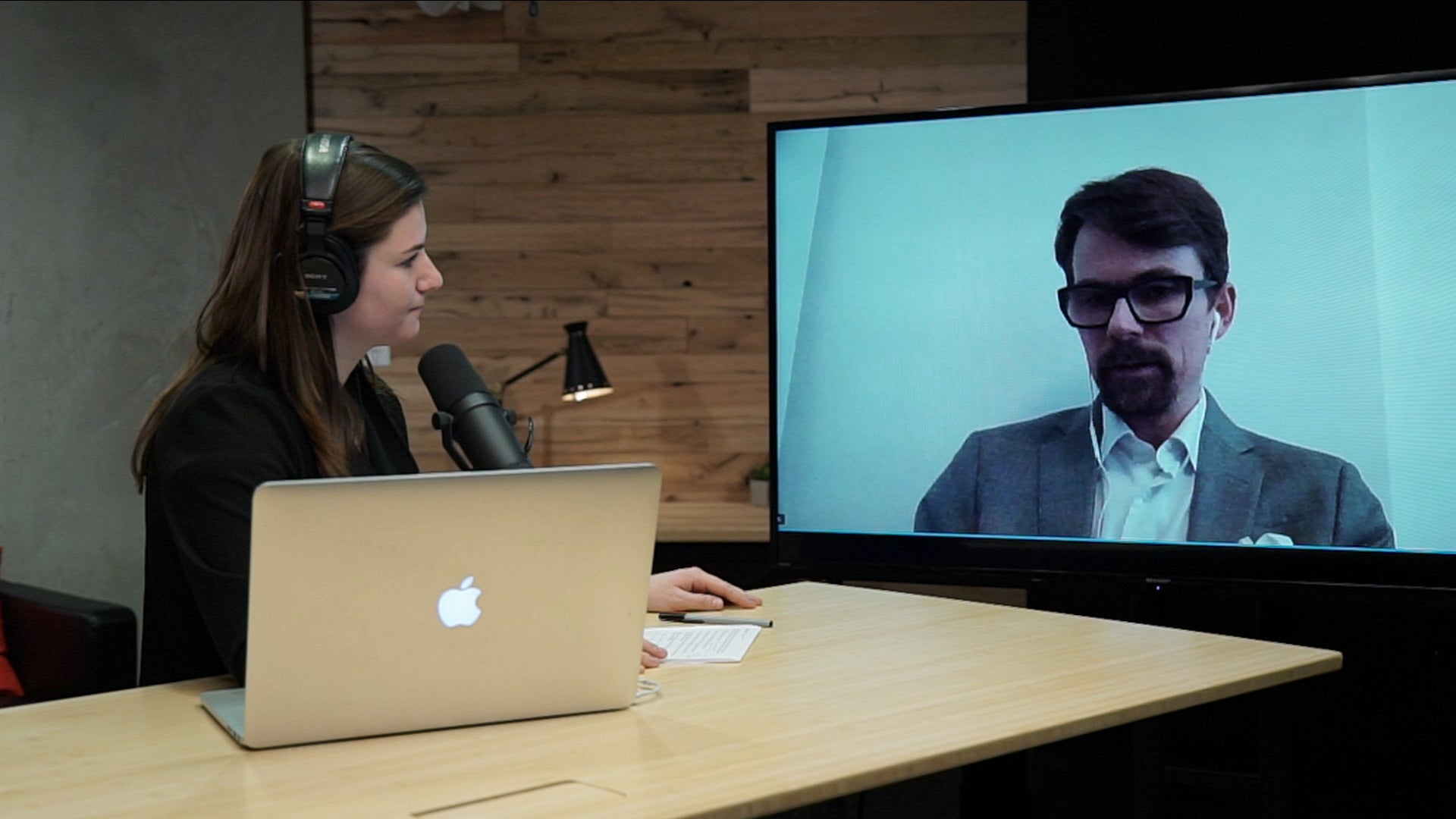
Guest host Juliet Beauchamp and CSO senior writer J.M. Porup talk about the challenges around securing the systems and networks used to control industrial plants and infrastructures.
Credit to Author: Shriram Munde| Date: Tue, 29 Jan 2019 06:09:49 +0000
While everyone was engaged in new year celebrations, malware authors were busy creating new ransomware for 2019. Quick Heal Security Labs has discovered the first ransomware of 2019 — Anatova ransomware. During our analysis, we found that Anatova is not just ransomware but a modular one. By modular ransomware we…
Read MoreCredit to Author: Shriram Munde| Date: Tue, 29 Jan 2019 05:30:20 +0000
Ransomware has become one of the most dangerous cyber-attack methods because of the different techniques it uses to encrypt the files and evade the detection of security software to earn money. Also, at a time, it’s not limited to encrypting user’s files but also deletes the files and formats the…
Read MoreCredit to Author: Malwarebytes Labs| Date: Mon, 28 Jan 2019 18:00:14 +0000
 | |
| A roundup of last week’s security news from January 21 to 27, including Modlishka, Crytekk, PUPs, and the State of Malware report. Categories: Tags: 2019 State of Malware report2faALPRandroid malwareanprArs TechnicaBleeping Computercrytekkcrytekk ransomwareDark ReadingfortnightgdprGoDaddyHelp Net SecurityKrebsOnSecuritymitsubishimodlishkaphishingrecapSecurity WeekTechCrunchThe Wall Street Journalvishingvoicemail phishingvulnerabilityweek in securityweekly blog roundupyoutube |
The post A week in security (January 21 – 27) appeared first on Malwarebytes Labs.
Read More
Credit to Author: Andrew Brandt| Date: Mon, 28 Jan 2019 17:30:52 +0000
Just connecting to a (malicious) wireless network could lead to Bad Things Happening, but none of the patched bugs have been seen in the wild (yet!)<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/a-RO7S2VeRA” height=”1″ width=”1″ alt=””/>
Read More