Android 7.0+ Phones Can Now Double as Google Security Keys
Credit to Author: BrianKrebs| Date: Thu, 11 Apr 2019 16:14:53 +0000
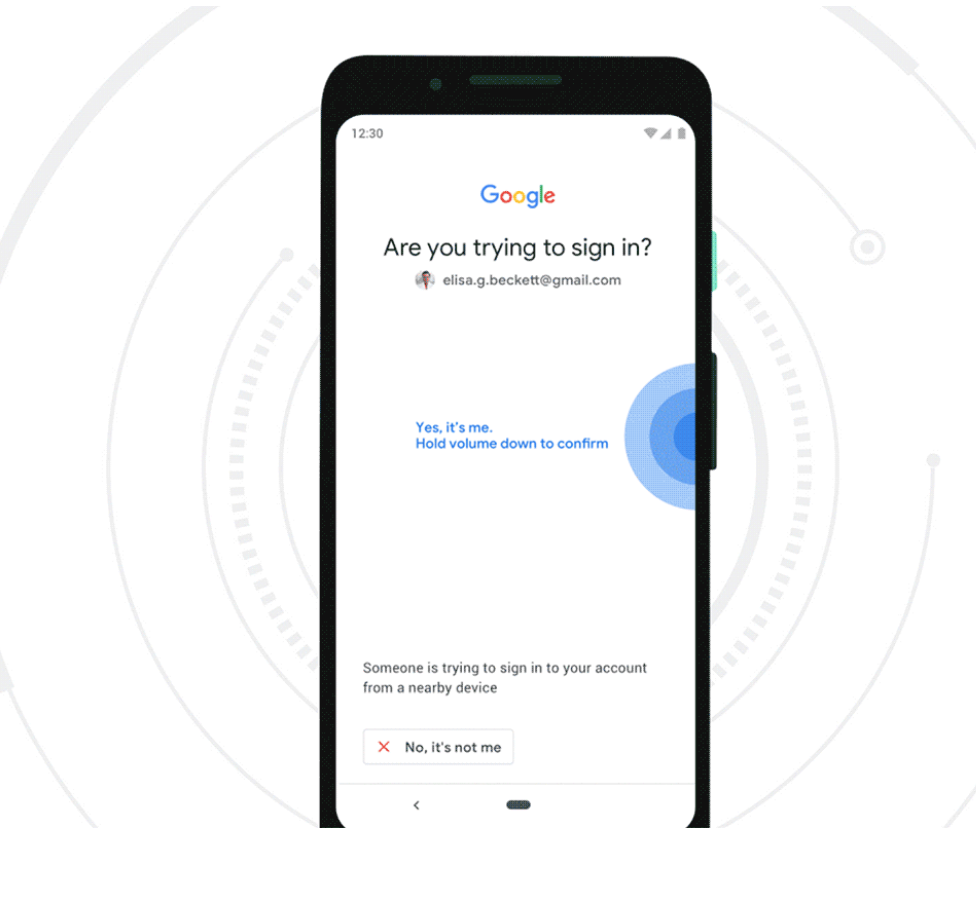
Google this week made it easier for Android users to enable strong 2-factor authentication (2FA) when logging into Google’s various services. The company announced that all phones running Android 7.0 and higher can now be used as Security Keys, an additional authentication layer that helps thwart phishing sites and password theft.
Read More