Cyber Risk Management: Bring Security to the Boardroom
Credit to Author: Fernando Cardoso| Date: Wed, 14 Feb 2024 00:00:00 +0000
Discover how to strategically present security controls to the board to better manage cyber risk.
Read MoreRSS Reader for Computer Security Articles
Credit to Author: Fernando Cardoso| Date: Wed, 14 Feb 2024 00:00:00 +0000
Discover how to strategically present security controls to the board to better manage cyber risk.
Read MoreIn 2023, the CL0P ransomware gang broke the scalability barrier and shook the security world with a series of short, automated campaigns.
Read MoreMicrosoft has issued patches for 73 security vulnerabilities in its February 2024 Patch Tuesday.
Read More
Credit to Author: Stan Kaminsky| Date: Wed, 14 Feb 2024 11:44:17 +0000
Which AI assistants and tools are insecure, and how to use LLMs without risking your data.
Read More
The last few weeks have been a PR bonanza for Taylor Swift in both good ways and bad. On the good side, her boyfriend Travis Kelce was on the winning team at the Super Bowl, and her reactions during the game got plenty of air time. On the much, much worse side, generative AI-created fake nude images of her have recently flooded the internet.
As you would expect, condemnation of the creation and distribution of those images followed swiftly, including from generative AI (genAI) companies and, notably, Microsoft CEO Satya Nadella. In addition to denouncing what happened, Nadella shared his thoughts on a solution: “I go back to what I think’s our responsibility, which is all of the guardrails that we need to place around the technology so that there’s more safe content that’s being produced.”
Credit to Author: Quickheal| Date: Wed, 14 Feb 2024 11:52:03 +0000

Checked your Security and Privacy Score Lately? Discover the latest news from the digital world around you with…
The post Quick Bytes: Top 5 Cyber News of the Week appeared first on Quick Heal Blog.
Read More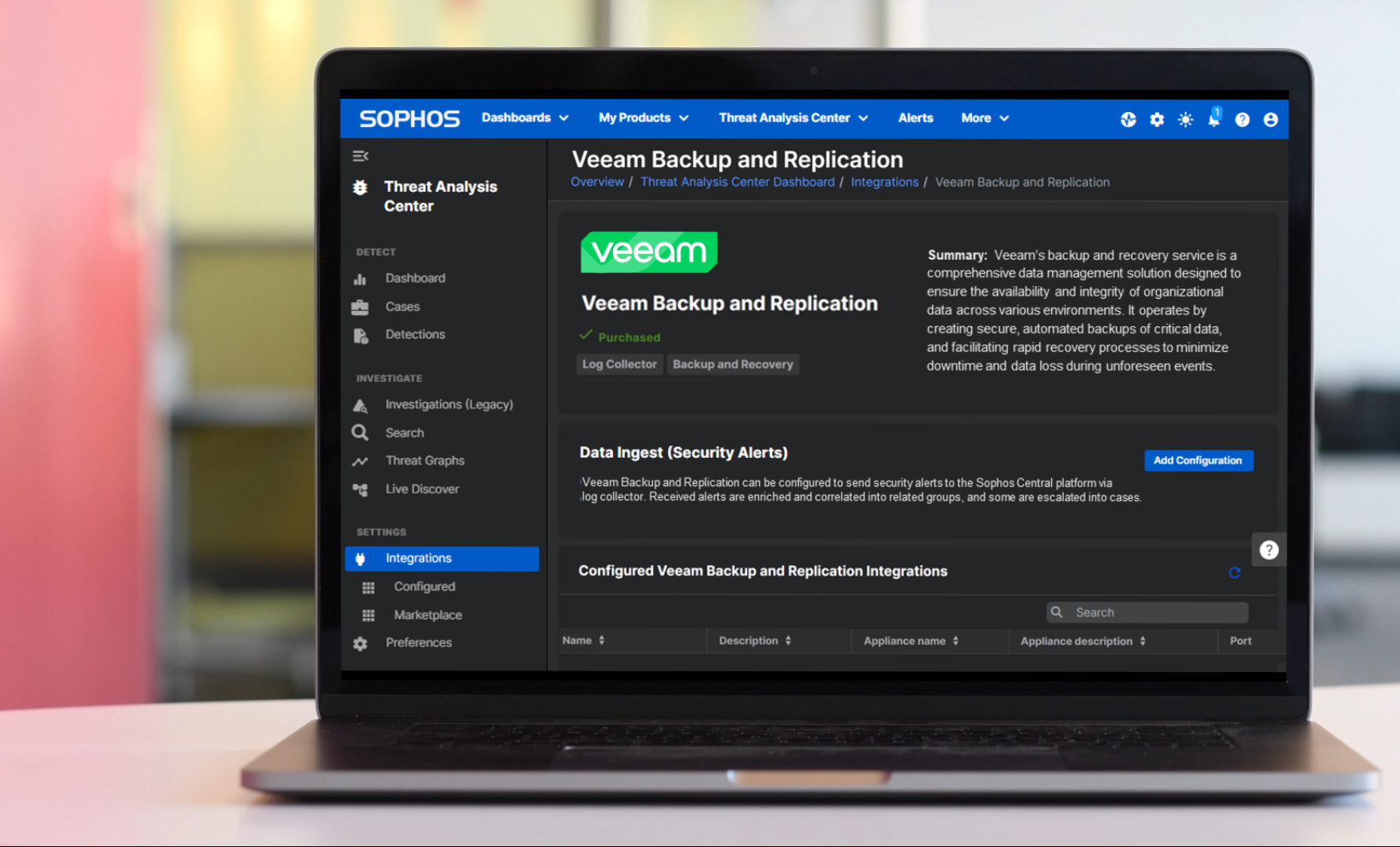
Credit to Author: Doug Aamoth| Date: Wed, 14 Feb 2024 10:11:03 +0000
Detect and stop threats targeting business-critical backup data.
Read More