Scammers Are Targeting Naive Bitcoin Owners With Terribly Simple Trick

Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Wed, 06 Sep 2017 13:00:00 +0000
PSA: don’t give anyone your Bitcoin private key.
Read MoreRSS Reader for Computer Security Articles

Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Wed, 06 Sep 2017 13:00:00 +0000
PSA: don’t give anyone your Bitcoin private key.
Read More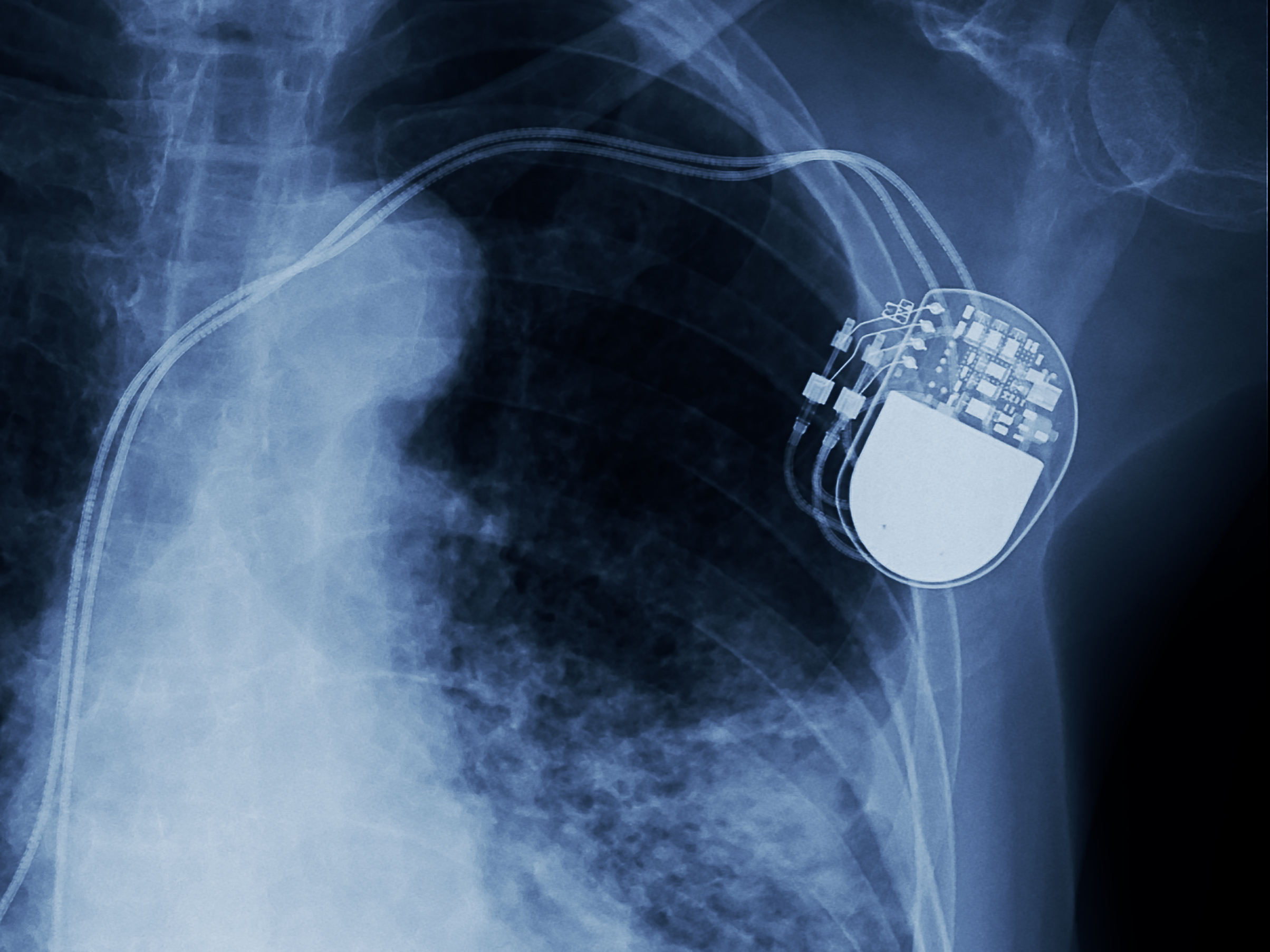
Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Wed, 30 Aug 2017 14:53:53 +0000
A painful reminder that a future where the internet is in every device—even the most critical one—can be disastrous.
Read More
Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Mon, 28 Aug 2017 16:19:24 +0000
The drone maker is offering between $100 and $30,000 to hackers who find and report vulnerabilities in the software of its unmanned aerial vehicles.
Read MoreCredit to Author: Dana Torgersen| Date: Wed, 23 Aug 2017 19:04:56 +0000
 | |
| 4 key steps you can take within your business to help gain trust with your employees while educating them to make more secure decisions. Categories: Tags: businessCTNTcybercrime tactics and techniquescybercriminalscybersecuritysecurity |
The post 4 Steps for improving employee trust while securing them appeared first on Malwarebytes Labs.
Read More
Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Thu, 17 Aug 2017 19:11:53 +0000
VICELAND’s show on hacking and cyberwarfare is back for a new season.
Read More
Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Fri, 11 Aug 2017 13:03:15 +0000
The hackers used booby-trapped Word documents and a leaked NSA hacking tool to get a foothold into the networks to then attack guests.
Read MoreCredit to Author: Daniel Desruisseaux| Date: Mon, 07 Aug 2017 15:46:06 +0000
Today in Schneider Electric’s News Release it was announced that we are partnering with Claroty, an innovator in Operational Technology (OT) network protection, to help to address cybersecurity challenges for the… Read more »
The post Partnering with specialists to help protect the world’s critical infrastructure from cyber attacks appeared first on Schneider Electric Blog.
Read More
Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Thu, 03 Aug 2017 18:54:02 +0000
Hackers behind two strains of WannaCry have moved out their bitcoin proceedings in a very similar way.
Read More