Human-operated ransomware attacks: A preventable disaster
Credit to Author: Eric Avena| Date: Thu, 05 Mar 2020 17:00:31 +0000
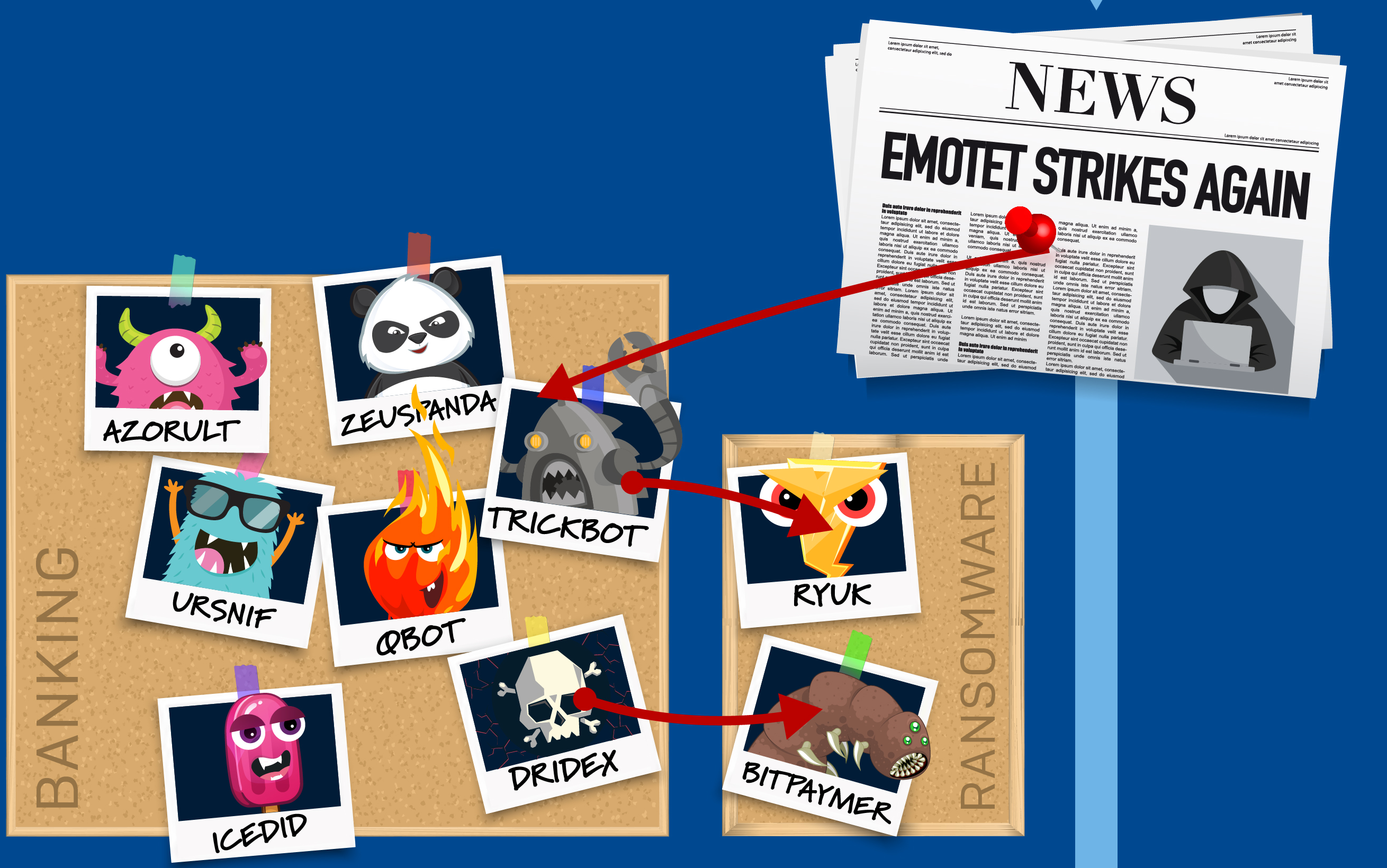
In human-operated ransomware attacks, adversaries exhibit extensive knowledge of systems administration and common network security misconfigurations, perform thorough reconnaissance, and adapt to what they discover in a compromised network.
The post Human-operated ransomware attacks: A preventable disaster appeared first on Microsoft Security.
Read more