Medical research data Advarra stolen after SIM swap
Medical research company Advarra reportedly had data stolen after a SIM swap incident on one of their employees.
Read MoreRSS Reader for Computer Security Articles
Medical research company Advarra reportedly had data stolen after a SIM swap incident on one of their employees.
Read MoreCredit to Author: Christopher Boyd| Date: Wed, 16 Feb 2022 16:51:24 +0000
 | |
| We take a look at a story regarding so-called “Beamers”, who use a number of techniques to compromise and then sell Roblox items. Categories: Privacy Tags: compromisediscordgamersgamingphishphishingrobloxRobuxSIM swapvideo games |
The post Roblox Beamers steal items from kids appeared first on Malwarebytes Labs.
Read More
Credit to Author: BrianKrebs| Date: Sun, 17 Mar 2019 23:25:06 +0000
Phone numbers stink for security and authentication. They stink because most of us have so much invested in these digits that they’ve become de facto identities. At the same time, when you lose control over a phone number — maybe it’s hijacked by fraudsters, you got separated or divorced, or you were way late on your phone bill payments — whoever inherits that number can then be you in a lot of places online.
Read More
Credit to Author: BrianKrebs| Date: Wed, 16 Jan 2019 00:52:34 +0000
Unsettling new claims have emerged about Nicholas Truglia, a 21-year-old Manhattan resident accused of hijacking cell phone accounts to steal tens of millions of dollars in cryptocurrencies from victims. The lurid details, made public in a civil lawsuit filed this week by one of his alleged victims, paints a chilling picture of a man addicted to thievery and all its trappings. The documents suggest that Truglia stole from his father and even a dead man — all the while lamenting that his fabulous new wealth brought him nothing but misery.
Read More
Credit to Author: BrianKrebs| Date: Fri, 09 Nov 2018 20:52:01 +0000
A Connecticut man who’s earned “bug bounty” rewards and public recognition from top telecom companies for finding and reporting security holes in their Web sites secretly operated a service that leveraged these same flaws to sell their customers’ personal data, KrebsOnSecurity has learned.
Read More
Credit to Author: BrianKrebs| Date: Wed, 07 Nov 2018 05:49:37 +0000
KrebsOnSecurity recently had a chance to interview members of the REACT Task Force, a team of law enforcement officers and prosecutors based in Santa Clara, Calif. that has been tracking down individuals engaged in unauthorized “SIM swaps” — a complex form of mobile phone fraud that is often used to steal large amounts of cryptocurrencies and other items of value from victims. Snippets from that fascinating conversation are recounted below, and punctuated by accounts from a recent victim who lost more than $100,000 after his mobile phone number was hijacked.
Read MoreCredit to Author: BrianKrebs| Date: Wed, 12 Sep 2018 20:58:31 +0000
The four major U.S. wireless carriers today detailed a new initiative that may soon let Web sites eschew passwords and instead authenticate visitors by leveraging data elements unique to each customer’s phone and mobile subscriber account, such as location, customer reputation, and physical attributes of the device. Here’s a look at what’s coming, and the potential security and privacy trade-offs of trusting the carriers to handle online authentication on your behalf.
Read More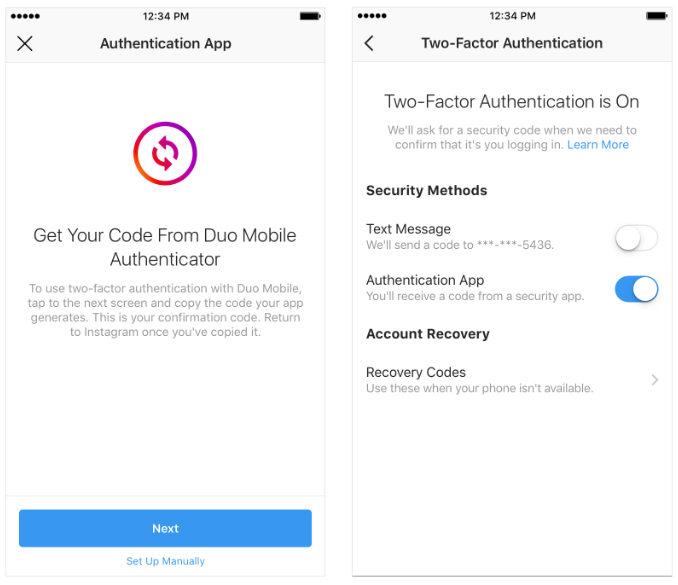
Credit to Author: BrianKrebs| Date: Wed, 29 Aug 2018 22:59:39 +0000
Instagram users should soon have more secure options for protecting their accounts against Internet bad guys. On Tuesday, the Facebook-owned social network said it is in the process of rolling out support for third-party authentication apps. Unfortunately, this welcome new security offering does nothing to block Instagram account takeovers when thieves manage to hijack a target’s mobile phone number — an increasingly common crime.
Read More