Computer Security Articles
RSS Reader for Computer Security Articles
sql
Prompt injection could be the SQL injection of the future, warns NCSC
Categories: News Tags: AI Tags: ML Tags: LLM Tags: chatgpt Tags: data poisoning Tags: SQL Tags: prompt injection The NCSC has warned about integrating LLMs into your own services or platforms. Prompt injection and data poisoning are just some of the risks. |
The post Prompt injection could be the SQL injection of the future, warns NCSC appeared first on Malwarebytes Labs.
Read MoreUpdate your LearnPress plugins now!
Categories: News Tags: wordpress Tags: learnpress Tags: vulnerability Tags: SQL Tags: injection Tags: update Tags: fix Tags: plugin Tags: patch We take a look at reports of a WordPress plugin issue. It’s been fixed, but you may need to update! |
The post Update your LearnPress plugins now! appeared first on Malwarebytes Labs.
Read MoreCVE-2022-35737 vulnerability in SQLite | Kaspersky official blog

Credit to Author: Enoch Root| Date: Thu, 03 Nov 2022 16:45:10 +0000
A 22-year-old vulnerability has been found in SQLite that could theoretically be used for DoS and arbitrary code execution.
Read MoreGh0stCringe RAT makes database servers squeal for protection
Credit to Author: Pieter Arntz| Date: Thu, 17 Mar 2022 14:09:26 +0000
The Gh0stCringe RAT is hunting for poorly secured MS-SQL and MySQL servers. Once the servers are infected, the RAT contacts a C&C server for further instructions.
The post Gh0stCringe RAT makes database servers squeal for protection appeared first on Malwarebytes Labs.
Read MoreDirected attacks against MySQL servers deliver ransomware
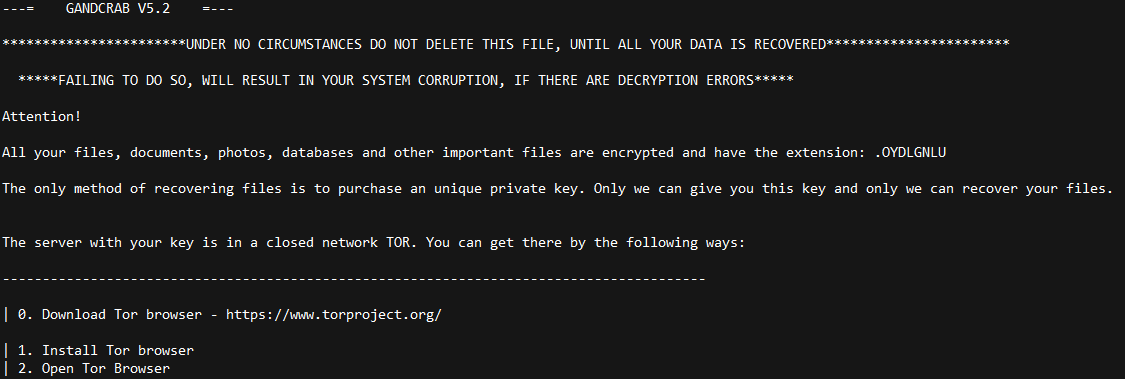
Credit to Author: Andrew Brandt| Date: Fri, 24 May 2019 12:00:29 +0000
Someone is attacking internet-facing Windows database servers with GandCrab ransomware<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/Cjmfa68wtrI” height=”1″ width=”1″ alt=””/>
Read MoreA taste of the onslaught at the network’s edge

Credit to Author: Andrew Brandt| Date: Tue, 30 Apr 2019 14:01:11 +0000
Edge devices take a licking so the rest of the network can keep on ticking, but they do need a little extra TLC<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/yLDeI_Y5qG8″ height=”1″ width=”1″ alt=””/>
Read MoreExplained: SQL injection
Credit to Author: Pieter Arntz| Date: Fri, 02 Mar 2018 18:30:40 +0000
 | |
| SQL injection is one of the most common attacks against businesses, with a high rate of success. So what can you do to prevent them? Categories: Tags: breachcodedrop tableinjectionphp. aspquerysqlSQL injection |
The post Explained: SQL injection appeared first on Malwarebytes Labs.
Read More