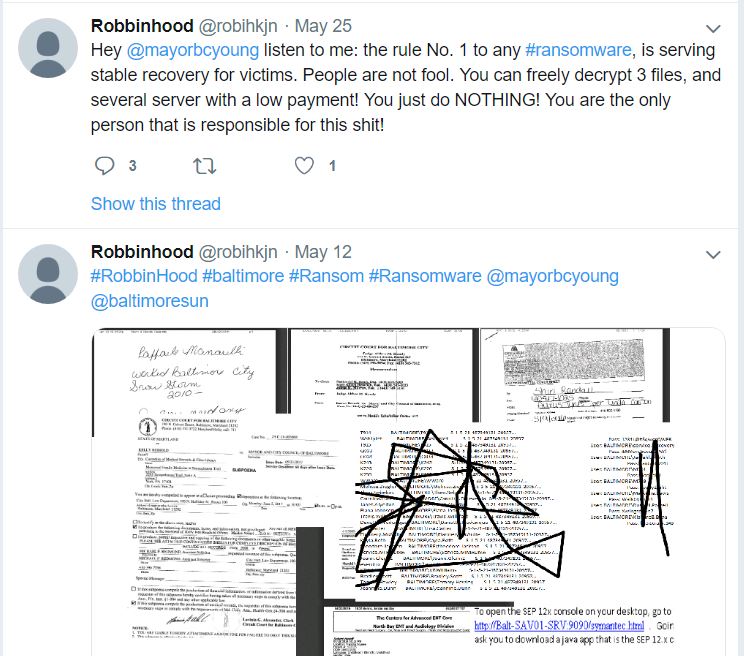
Pakistani Firm Shipped Fentanyl Analogs, Scams to US

Credit to Author: BrianKrebs| Date: Wed, 07 May 2025 22:22:48 +0000
A Texas firm recently charged with conspiring to distribute synthetic opioids in the United States is at the center of a vast network of companies in the U.S. and Pakistan whose employees are accused of using online ads to scam westerners seeking help with trademarks, book writing, mobile app development and logo designs, a new investigation reveals.
Read More