[updated]Unpatched Atlassian Confluence vulnerability is actively exploited
Credit to Author: Pieter Arntz| Date: Fri, 03 Jun 2022 14:41:58 +0000
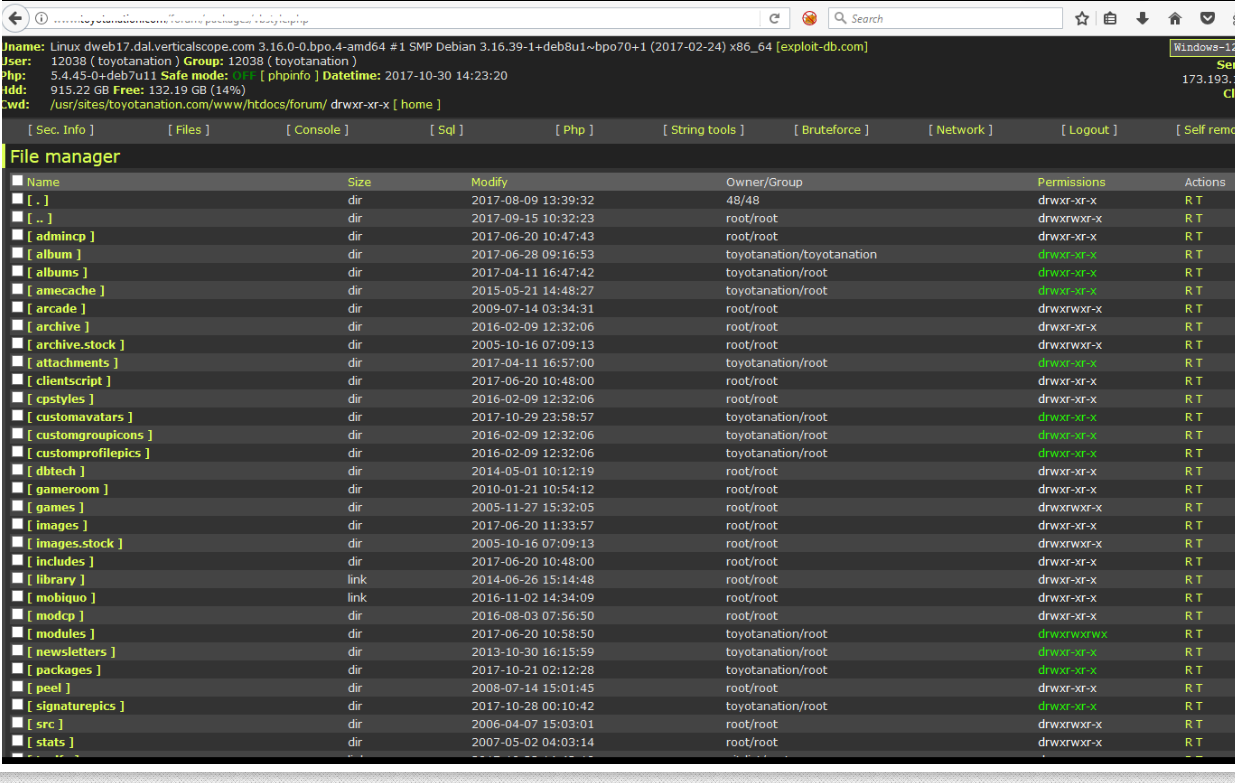
A vulnerability in Atlassian Confluence was found by performing an incident response investigation on a compromised server. The vulnerability is not yet patched.
The post [updated]Unpatched Atlassian Confluence vulnerability is actively exploited appeared first on Malwarebytes Labs.
Read more