Following the Money Hobbled vDOS Attack-for-Hire Service
Credit to Author: BrianKrebs| Date: Tue, 06 Jun 2017 12:12:47 +0000
A new report proves the value of following the money in the fight against dodgy cybercrime services known as “booters” or “stressers” — virtual hired muscle that can be rented to knock nearly any website offline.
Last fall, two 18-year-old Israeli men were arrested for allegedly running vDOS, perhaps the most successful booter service of all time. The young men were detained within hours of being named in a story on this blog as the co-proprietors of the service (KrebsOnSecurity.com would later suffer a three-day outage as a result of an attack that was alleged to have been purchased in retribution for my reporting on vDOS).
The vDos home page.
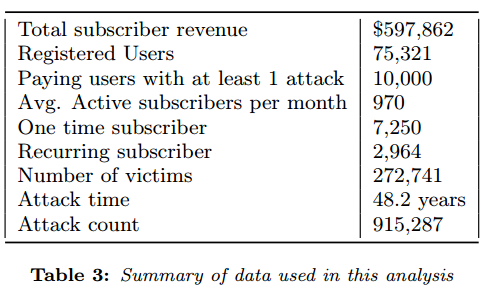
That initial vDOS story was based on data shared by an anonymous source who had hacked vDOS and obtained its private user and attack database. The story showed how the service made approximately $600,000 over just two of the four years it was in operation. Most of those profits came in the form of credit card payments via PayPal.
But prior to vDOS’s takedown in September 2016, the service was already under siege thanks to work done by a group of academic researchers who teamed up with PayPal to identify and close accounts that vDOS and other booter services were using to process customer payments. The researchers found that their interventions cut profits in half for the popular booter service, and helped reduce the number of attacks coming out of it by at least 40 percent.
At the height of vDOS’s profitability in mid-2015, the DDoS-for-hire service was earning its proprietors more than $42,000 a month in PayPal and Bitcoin payments from thousands of subscribers. That’s according to an analysis of the leaked vDOS database performed by researchers at New York University.
As detailed in August 2015’s “Stress-Testing the Booter Services, Financially,” the researchers posed as buyers of nearly two dozen booter services — including vDOS — in a bid to discover the PayPal accounts that booter services were using to accept payments. In response to their investigations, PayPal began seizing booter service PayPal accounts and balances, effectively launching their own preemptive denial-of-service attacks against the payment infrastructure for these services.
Those tactics worked, according to a paper the NYU researchers published today (PDF) at the Weis 2017 workshop at the University of California, San Diego.
“We find that VDoS’s revenue was increasing and peaked at over $42,000/month for the month before the start of PayPal’s payment intervention and then started declining to just over $20,000/month for the last full month of revenue,” the paper notes.
 The NYU researchers found that vDOS had extremely low costs, and virtually all of its business was profit. Customers would pay up front for a subscription to the service, which was sold in booter packages priced from $5 to $300. The prices were based partly on the overall number of seconds that an attack may last (e.g., an hour would be 3,600 worth of attack seconds).
The NYU researchers found that vDOS had extremely low costs, and virtually all of its business was profit. Customers would pay up front for a subscription to the service, which was sold in booter packages priced from $5 to $300. The prices were based partly on the overall number of seconds that an attack may last (e.g., an hour would be 3,600 worth of attack seconds).
In just two of its four year in operation vDOS was responsible for launching 915,000 DDoS attacks, the paper notes. In adding up all the attack seconds from those 915,000 DDoS attacks, the researchers found vDOS was responsible for 48 “attack years” — the total amount of DDoS time faced by the victims of vDOS.
“As VDoS’s revenue and active subscriber base dwindled, so did the amount of harmful DDoS attacks launched by VDoS,” the NYU researchers wrote. “The peak attack time we found was slightly under 100,000 attacks and 5 attack years per month when VDoS’s revenue was slightly over $30,000/month. This decreased to slightly under 60,000 attacks and 3 attack years during the last month for which we have attack data. Unfortunately, we have incomplete attack data and likely missed the peak of VDoS’s attack volume. However, the payment intervention correlates to a 40% decrease in attack volume, which equates to 40,000 fewer attacks and 2 fewer attack years per month.”
Although a small percentage of vDOS customers shifted paying for their monthly subscriptions to Bitcoin after their preferred PayPal methods were no longer available, the researchers found that most customers who relied on PayPal simply went away and never came back.
“Near the middle of August 2015, the payment intervention that limited vDOS’s ability to accept PayPal payments began to take its toll on vDOS,” the researchers wrote. “Disrupting vDOS’s PayPal payment channel had a noticeable effect on both recurring and new revenue. By August 2015, payments from the PayPal channel decreased by $12,458 (44%) from an average of $28,523 over the previous five months. The Bitcoin payment channel increased by $6,360 (71%), but did not fully compensate for lost revenue from PayPal.”
The next month, vDOS established a number of ad-hoc payment methods, such as other third-party payment processors that accept credit card payments. However, most of these methods were short lived, likely due to the payment processors learning about the nature of their illicit DDoS service and terminating their accounts, the researchers observed.
“The revenue from these other regulated payment channels dwindled over a ten month period from $18,167 in September 2015 to $1,700 during June 2016,” the NYU team wrote. “The last month of the database leak in July 2016 shows no other forms payments other than Bitcoin.”
Other developments since vDOS’s demise in September 2016 have conspired to deal a series of body blows to the booter service industry. In October 2016, Hackforums — until recently the most bustling marketplace on the Internet where people could compare and purchase booter services — announced it was permanently banning the sale and advertising of these services on the forum.
In December 2016, authorities in the United States and Europe arrested nearly three-dozen people suspected of patronizing booter services. The enforcement action was a stated attempt by authorities to communicate to the public that people can go to jail for hiring booter services.
In April 2017, a U.K. man who ran a booter service that delivered some 1.7 million denial-of-service attacks against victims worldwide was sentenced to two years in prison.
Prosecutors in Israel say they are preparing formal charges against the two young Israeli men arrested last year on suspicion of running vDOS.
Check out the full NYU paper here (PDF).