Startup That Sells Zero-Days to Governments Is Offering $1 Million For Tor Hacks
Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Wed, 13 Sep 2017 14:18:31 +0000
A notorious startup is offering up to $1 million in rewards to security researchers who can find bugs and develop techniques to exploit the anonymous web surfing tool the Tor Browser.
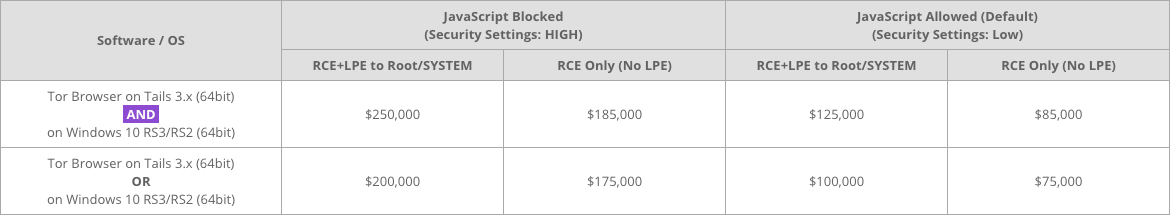
On Wednesday, Zerodium, a US-based company that buys exploits from researchers and sells them exclusively to government customers, announced the new bounty. The highest bounty is $250,000 for an exploit that allows the attacker to hack a target who’s using the Tor Browser with high security settings on Linux Tails and Windows, giving the attacker the highest kind of privileges on the target’s computer. Other bounties range between $75,000 (for exploits that only work for either Windows or Tails, and work only with Javascript allowed, for example, making them easier to develop) and $200,000.
Read more: iPhone Bugs Are Too Valuable to Report to Apple
“We need many exploits as we have many customers with many ongoing operations against illegal activities undertaken on Tor,” Chaouki Bekrar, the CEO and founder of Zerodium, told Motherboard in an online chat. “We have a higher demand for Tor exploits from our government customers as they are facing higher illegal activities on Tor and they must take action.”
In the announcement, Zerodium specifically pointed to “drug trafficking or child abuse” as examples of how “ugly people” use Tor. The bounty is open until November 30 unless payouts reach $1 million before then, the company said. Usually, bug bounty programs don’t have an expiration date.
Zerodium has gained notoriety for offering high payouts and bounties for targets such as the iPhone. In 2015, shortly after its launch, Zerodium offered $1 million for anyone who could develop a technique to hack an iPhone remotely. When the challenged ended, the company claimed that a team of hackers was able to claim the bounty. Zerodium always declines to discuss the identities of its customers or the researches it deals with.
Undoubtedly, there’s demand among intelligence and law enforcement agencies for such exploits. Last year, European cops hacked users of a child pornography website called The GiftBox Exchange using an unknown Firefox vulnerability—or zero-day. But some believe that Zerodium’s headline-grabbing prices are just a marketing stunt.
“I don’t think [the prices] are accurate reflections of Tor Browser as a secure system,” a security researcher with knowledge of the exploit market, who asked to remain anonymous, told Motherboard. “Those prices are marketing.”
Last month, when Zerodium announced new rates and bounties, offering the same amount of money ($100,000) for similar Tor Browser and Chrome exploits, Tor developer and cryptographer Isis Lovecruft told Motherboard that “maybe this is all a PR stunt to get people like us to pay attention to their silly 0day-hoarding startup :).”
In response to this criticism, Bekrar said that the “prices are high as exploitation without JavaScript is difficult and [Local Privilege Escalation] is required for the highest payouts.”
“Hard research work = big bounty,” he told me.
The Tor Project, which develops and maintains the Tor Browser, did not immediately respond to a request for comment.
This story has been updated to include a comment from Chaouki Bekrar.
Got a tip? You can contact this reporter securely on Signal at +1 917 257 1382, OTR chat at lorenzo@jabber.ccc.de, or email lorenzo@motherboard.tv
Get six of our favorite Motherboard stories every day by signing up for our newsletter.