A Roundtable of Hackers Dissects ‘Mr. Robot’ Season 3 Episode 2: ‘Undo’
Credit to Author: Yael Grauer| Date: Fri, 20 Oct 2017 17:47:27 +0000
The second episode of Mr. Robot’s third season is fast-paced as ever, and the hacks kept coming. Our crew of technologists hopped on Keybase group chat to delve into the details. (The chat transcript has been edited for brevity and clarity.) This week’s team of experts include:
- Bill Budington: a long time activist, programmer, and cryptography enthusiast, and a security engineer and technologist at the Electronic Frontier Foundation.
- Jason Hernandez: a technologist who studies surveillance and works in IT, and is the tech editor for North Star Post.
- Freddy Martinez: a technologist working on whistle blowing technologies. He serves as a Director for the Chicago-based Lucy Parsons Labs.
- Matt Mitchell: a hacker who leads cryptoharlem, which aims to teach basic cryptography tools in the inner city. He also trains newsroom journalists (at Global Journalist Security), activists & human rights defenders in digital & operational security.
This week we discussed Ecoin, safehouses, video exfiltration, rootkits, IP addresses, and monitor exploits.
Yael: So this episode starts with Elliot getting a job at ECorp to right his wrongs. Seems like an interesting strategy.
Bill: I love the happy-go-lucky music that’s playing in the background.
Freddy: I love all the scenes where Elliot becomes normal for about five minutes. The Starbucks scene also comes to mind.
Yael: Can he really rebuild the database/”undo” his hack by digitizing records and using PPT presentations to improve security?
Freddy: Hey, if the NSA can do it with PPT, so can Elliott.
Jason: The point is to make “Phase 2” impossible. Elliott gets a job at ECorp and almost immediately patches the UPSs so they can’t be loaded with unsigned code.
Matt: I think he wants to buy time, clean out bad execs, and work on digitizing things.
Yael: I was surprised that he could get so many people fired at work after getting into their email and not get caught.
Jason: It’s possible he was able to get a copy of users’ password hashes as part of his role in security, for an “audit.” He could brute force attack them offline if they weren’t hashed/salted well.
Yael: (For people who don’t know, hashing is turning passwords into strings of digits, and salting is adding a series of random bytes to the end of the passwords before they are hashed.)
Bill: Oh no, it’s stored in md5, unsalted! 😉
Yael: Aren’t these fellow security folks, though?
Freddy: Well they’re management. It’s not the same thing. They should have used Gmail’s advanced protection mode.
Yael: I am getting that set up!
Jason: No two-factor on anything at ECorp.
Bill: If anything, in this universe I’d expect delegated logins to go through ECorp. They control everything else, right?
Freddy: I’m sure Elliot knows enough PowerShell to abuse LDAP, or at least get credentials to their email. It’s not that hard when you’re already inside their network.
Matt: At ECorp with the creepy dude, Elliot was using security software from one of the companies that consult for tech accuracy: Tanium. Hak5 aka Darren Kitchen and co. He was in server room running a scan before one of the PPT meetings.
Bill: I just looked it up and it looks like they actually used the correct model of Dell monitor in the scene, too.
Yael: So what’s this Darlene/FBI deal? She’s got immunity by being a confidential human source. It sounds like she’s not getting prosecuted for…her role in something? if she gets intel on Tyrell from Elliot. I think she is also protecting Elliot as part of the deal.
Freddy: What are the terms of her deal? “Immunity” seems like a very broad term and there are multiple kinds of immunity.
Jason: This is the kind of immunity where you don’t have access to a lawyer.
Freddy: This is why you NEVER talk to the FBI. Also, how is it that Darlene flipped and Angela didn’t?
Matt: Yeah, she took a safe house and the whole shebang. Maybe it was the Cisco shooting. Got Darlene shook.
Bill: Cooperating with the feds against the Dark Army. Damn.
Jason: Did the Feds try and pressure Angela?
Bill: It’s that White Rose touch. Angela has been brainwashed or something.
Freddy: I meant, she wanted to turn herself in and Dark Army stopped her.
Bill: The glazed over look in her eyes while they were on the bus kind of gives it away.
Matt: Darlene’s house at the end is where Elliot is, with the feds looking at it.
Freddy: That’s the FBI operational base.
Matt: Darlene’s apartment is downstairs from the feds.
Freddy: Possibly. I didn’t consider that.
Bill: Oh, that makes a lot of sense. It also makes sense of the dialogue at the end of the episode from the FBI, after Elliott shows up.
Yael: Someone explain what’s going on with this Ecoin/China thing.
Bill: So China is behind bitcoin, possibly based on the real-life mining monopoly they have on the bitcoin market.
Matt: China is trying to annex Congo to make it part of China. The UN needs to vote for it to happen.
Bill: And the rest of the world is behind Ecoin, with EvilCorp’s backing.
Matt: They are using bitcoin, not E-coin, which affects the market, price, stability, and power of Ecoin.
Freddy: It’s weird. The US and China are using alt coins to argue about if China can invade Congo. This seems unlikely. Imperialist empires don’t function like this.
Jason: The geopolitics of it all makes no sense.
Bill: And EvilCorp is trying to get White Rose in line with this, and White Rose is like NOPE PLUS STAGE 2 NO MATTER WHAT.
Jason: There are people in the Congo that certainly have an opinion on whether their government should be run from Beijing.
Bill: Yeah, I think the Congo thing is just to make a point of just how evil these imperialist powerful capitalist masterminds are.
Freddy: Also notice they had this talk at a G20 meeting?
Jason: Yes, I did.
Matt: They need a place to move their base of operations.
Freddy: Yeah, show producers left out the mass protests around the G20 summits. Hamburg’s was called “welcome to hell!” and that was this year.
Yael: So what did Darlene put on Elliot’s computer exactly?
Jason: I think a device to exfiltrate video information.
Bill: I think it was something that wasn’t actually on the computer but sits in the middle of the monitor and its output, so it gets a feed from monitor in, sends it along its merry way as monitor out, but captures everything.
Matt: She put a USB with malware, that sends screenshots VNC style.
Bill: Possibly with a built-in cell connection.
Freddy: Elliott ran a rootkit checker and didn’t find anything, but if it’s on the video link, it wouldn’t be found.
Bill: Yes, rkhunter.
Freddy: He was in Linux Mint, then stopped and checked it using Kali, which the FBI saw.
Jason: To be clear, Elliot likely did the rootkit check to act like he was checking “normal” things.
Bill: I was thinking he was trying to fool the feds into being plausibly cautious. I don’t think he was being cautious, but just enough to fool the feds. I like how he booted directly to Kali, as if to make it seem to the feds like he’s trying to be really undetected (which would foil some malware).
Jason: He probably carries a flash drive with Kali installed on that and only trusts the flash drive. Tails is another popular option for that security model.
Freddy: In this version of the tool, it does a checksum on important files to verify that they haven’t been modified and compares it to “known” good results online. So if Darlene had touched his computer, he could detect very sloppy rootkits.
Jason: Ehh, this machine clearly isn’t one that he’s trusting. Might as well run Windows 7 and Adobe Flash.
Bill: When he sends the link at the end of the episode, he must have generated a new email address and key on a separate machine, right?
Yael: Was that a phishing link that he pretends to send to Tyrell to track the feds?
Matt: It’s a file. A rare compressed one.
Jason: Any web server logs the IP address of computers connecting to it. Anybody reading this article has their IP recorded by some web server.
Bill: It was a tripwire.
Freddy: FBI needs to use seven more proxies.
Yael: How does Tyrell know not to click on it? Because the email made no sense?
Bill: I don’t think it was sent to Tyrrell at all. I think it was meant to look like it was sent to Tyrell.
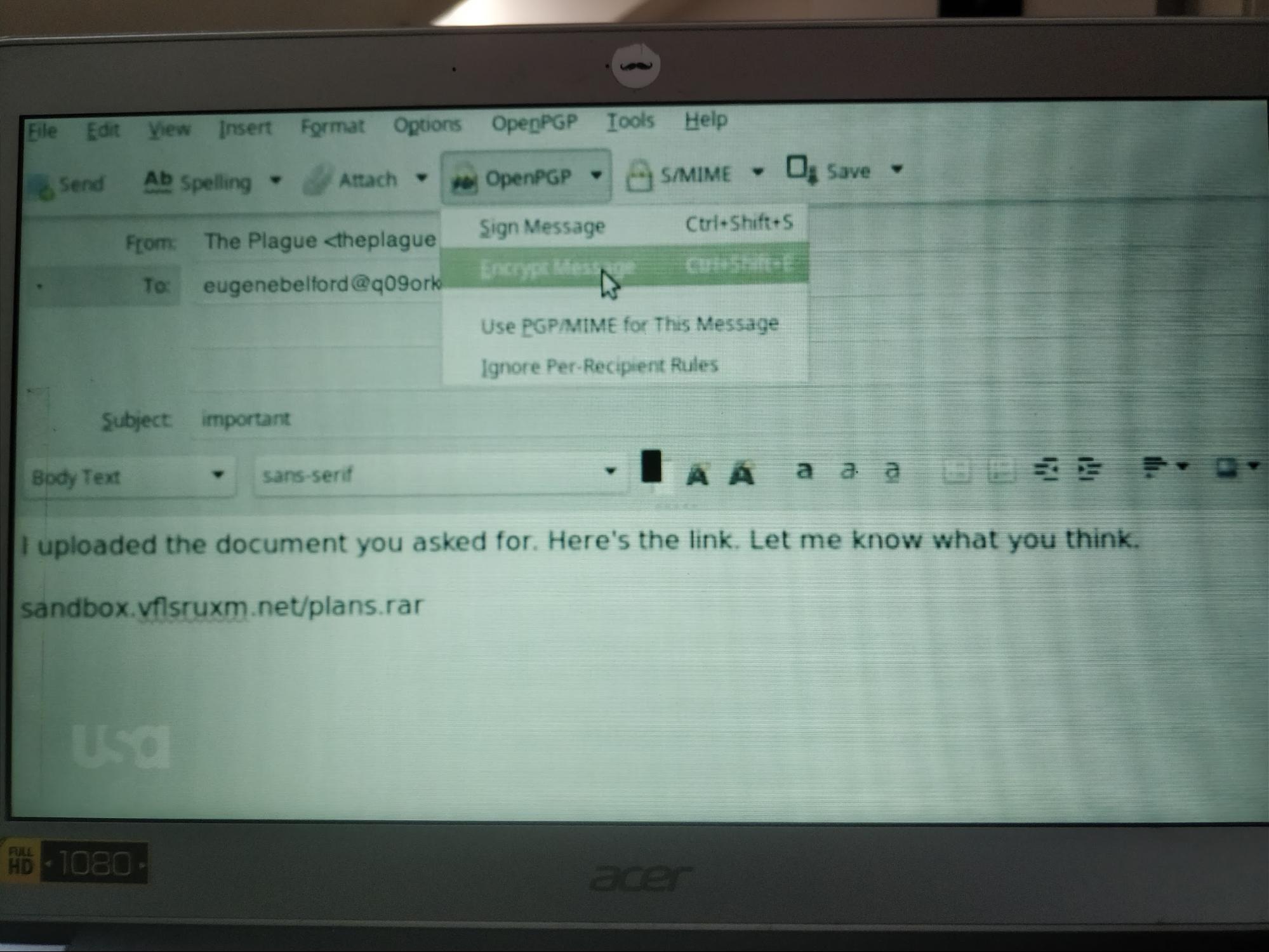
Freddy: Elliot wrote a fake email to “Tyrell” knowing the FBI was monitoring the email and would click the URL he encrypted to “Tyrell.”
Jason: Also it doesn’t matter if Tyrell also clicked it. Then there are just two IP addresses, and Elliot can pick out which one is the interesting one.
Bill: But it was never intended for him. It was just for the feds. Again, he must have a backup computer to set up that web architecture and log when the URL is tripped.
Jason: If the FBI checked the link over Tor or a VPN, they wouldn’t have given away their location. That screenshot is Thunderbird with the Enigmail extension, FYI.
Yael: I have that setup!
Bill: Also, if he sent it via something like WhatsApp, the URL would have been pinged automatically, due to “intelligent” URL pre-fetching. Good he used PGP instead, I guess
Yael: So then what does Elliot get, the FBI IP address?
Freddy: Yes, and then some breaking and entry on the address.
Jason: Was it a breaking & entry? Or did he have a key for Darlene’s apartment?
Freddy: No way the FBI sets up an operations platform inside Darlene’s apartment.
It must be a safe house they were keeping her at.
Jason: But they could have from the one above her apartment.
Freddy: Too much traffic coming and going. Someone would notice.
Bill:
Jason: I also want to clarify to readers that getting an IP address doesn’t necessarily give a perfect location. IP lookup databases aren’t perfect. There’s a great article by Kashmir Hill on them and this one place in Kansas…
Yael: Well, they can be…. I wrote a thing about this once. You just need access to a special database.
Matt: The FBI tends to set up in places across the street or next door to places they watch, according to some published case files. Setting up monitoring equipment inside while posing as cable or power utility employees.
Matt: Maxmind’s database is popular, but they don’t always get it right. I am sure the feds have their own IP database to cross-reference.
Yael: I wonder if Skyhook Wireless includes the FBI address. I don’t think Elliot has Skyhook but ECorp certainly might.
Freddy: Did you notice the electric company that was outside the FBI safehouse had Sputnik on it? 60 years since Sputnik went up! October 4, 1957.
Jason: It’s possible that the RAR file had an exploit that gathered some more information or exploited a location API on a GPS-enabled device to get better location info.
Matt: In real life, the link and domain don’t work, unless there is some weird Unicode character in there. Sandbox.vflsruxm.net. Oh, wait. There is a directory there.
Yael: It doesn’t look like very strong encryption.
Matt: The RAR file is real, too.
Jason: Who wants to open that up in a Qubes VM?
Bill: On it
Freddy: Boots a VM.
Bill: Though I don’t think they’d distribute malware if the showrunners set the site up. 🙂
Jason: Also note this page is designed to look like a file directory, but it has terms of service and a privacy policy, thanks to USA Networks’ legal team.
Bill: user@browsing:~/blah$ unrar x plans.rar
UNRAR 5.21 freeware
Copyright (c) 1993-2015 Alexander Roshal
plans.rar is not RAR archive
No files to extract. Looks like it’s b64 encoded. It’s a png.

Matt: I kept forgetting it’s 2015 in Mr. Robot when I was watching that talk at IFF in Turkey about China and Ecoin.
Jason: I’d also say it’s not so plausible that Elliot would leave a computer around without disk encryption at boot-up.
Matt: Disk encryption at boot won’t protect you from a USB that’s there running as a keyboard like a rubber ducky.
Bill: It’s a GitHub repo. “Poc, Presentation of Monitor OSD Exploitation, and shenanigans of high quality” Hahaha it’s the MONITOR EXPLOIT!!!!!
Matt: QR are deadly. I don’t scan; just use https://zxing.org/w/decode.jspx/.
Bill: https://github.com/RedBalloonShenanigans/MonitorDarkly Dude, this is the exploit for Elliot’s monitor!
Bill: I sent an email to the MonitorDarkly repo maintainers letting them know about their appearance :]
Jason: So maybe Darlene booted up Mint and ran this exploit against the monitor.
Freddy: Predictions for next episode in 140 characters?
Yael: I think Darlene escapes and gets caught/arrested and somehow Angela bails her out.
Freddy: Dark Army pulls off Phase 2.
Jason: I think Elliot goes after Dark Army.
Matt: I think from the doors the woodcutter and Irving do a different kind of hacking. Beware Elliot. Hipsters with axes don’t play.