A Roundtable of Hackers Dissects ‘Mr. Robot’ Season 3 Episode 3: ‘Legacy’
Credit to Author: Yael Grauer| Date: Fri, 27 Oct 2017 17:00:00 +0000
The third episode of Mr. Robot’s third season may have been light on hacks, but our crew of technologists hopped on Keybase group chat to talk baby cams, encryption, and more. (The chat transcript has been edited for brevity and clarity.) This week’s team of experts include:
- Bill Budington: a long time activist, programmer, and cryptography enthusiast, and a security engineer and technologist at the Electronic Frontier Foundation.
- Jason Hernandez: a technologist who studies surveillance and works in IT, and is the tech editor for North Star Post.
- Harlo Holmes: a digital security trainer at Freedom of the Press Foundation.
- Zachary Julian: a Senior Security Analyst at Bishop Fox, a security consulting firm
- Matt Mitchell: a hacker who leads cryptoharlem, which aims to teach basic cryptography tools in the inner city. He also trains newsroom journalists (at Global Journalist Security), activists & human rights defenders in digital & operational security.
Yael: So this whole episode seemed like sort of a series of “wrapping loose ends” scenes.
Bill: Yeah, remember last season where in the chats we kept saying, “Where’s TYRELL??” Well, we got our answer. Chopping wood in the territory of the Dark Army.
Yael: Any comments on the first hacking scene? Looked like some kind of cryptolocker encryption directory.
Bill: The name of the program was something like FSY ETY or something, so I think it was custom written for the show.
Matt: Yeah, F Society custom encryption.
Bill: F Society rolled their own encryption?
Harlo: They wouldn’t be the types to roll their own crypto 🙂
Jason: I doubt F Society wrote the crypto algorithm. It’s probably just a script that loops through directories and uses some existing encryption tool. It looked like it was accessing multiple servers over SCP.
Bill: Heh, yeah I figured. It’s not AES-FSOCIETY mode? 😉
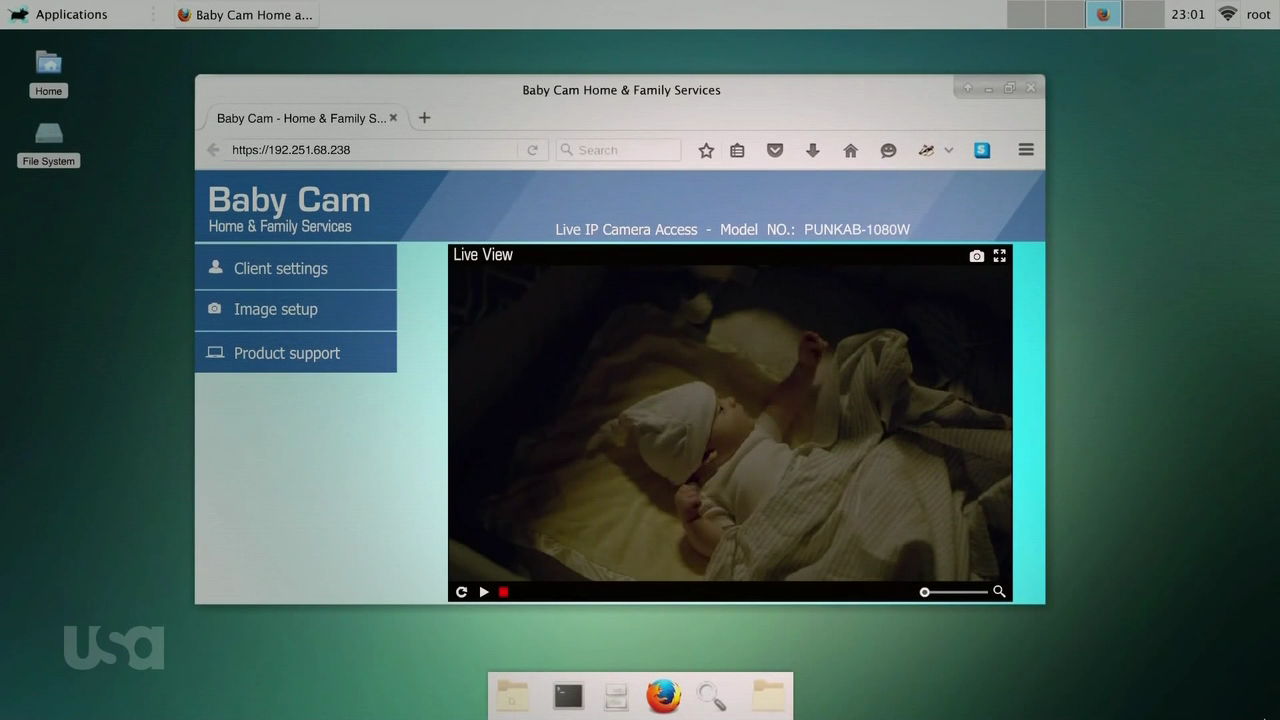
Yael: Did Tyrell hack into his own baby cam? I figured he either hacked in or had a shitty password he memorized. He was using the laptop that Irving/Dark Army had given him. I don’t think it had his own passwords saved on it, or his password manager. He wouldn’t put his password manager in the cloud, would he?
Jason: A few diceware passphrases are not hard to memorize.
Bill: About that baby cam: it has HTTPS Everywhere (which I develop at EFF) and Privacy Badger (another EFF project) :] Also notice his baby cam has an HTTPS address, that’s kind of interesting/rare for an IP address. Not unheard of though. Whoa, you can go to that address! It redirects you to https://y9bukwer.bxjyb2jvda.net/. Http://192.251.68.238 is the baby monitor address.
Yael: With all the baby monitor hacks, I think I’d use a radio frequency-based baby monitor, which could only be hacked by someone intercepting the radio signal with a sniffing device outside of your house, rather than literally everyone on the Internet.
Jason: Disagree with using RF baby monitors. They’re all awful, but at least there are ways to secure an internet connected one. I’d stick it behind a VPN internally and have my router limit its external network connectivity.
Yael: So how did Tyrell get in?
Bill: Maybe he prepared, or maybe he used SSH tunneling to his home. SSH tunneled the baby cam to https://192.251.68.238, and he could have used basicauth behind https. There are any number of possible pretty-secure setups.
Zachary: He probably has a dedicated IP at the Wellick house anyway. :p
Yael: So you can SSH tunnel to a static IP address even from a Dark Army laptop you’ve never seen before?
Bill: Well, say the 192.251.68.238 address was a VPS, and then he could tunnel to his home address, which is perhaps a static address he remembered or perhaps he has DynDNS or an onion service running on it, so he doesn’t have to worry about his home IP changing.
Jason: Yeah, makes sense. Lots of hackers have a VPS or two that they use as jump boxes.
Zachary: Interesting that the baby cam has 8080 and 8443 also internet facing. Or rather, the actual Easter egg IRL has those ports open to the internet.
Yael: Okay, so moving onto the femtocell hack… anyone have anything on that? Tyrell seemed upset that it had Android malware.
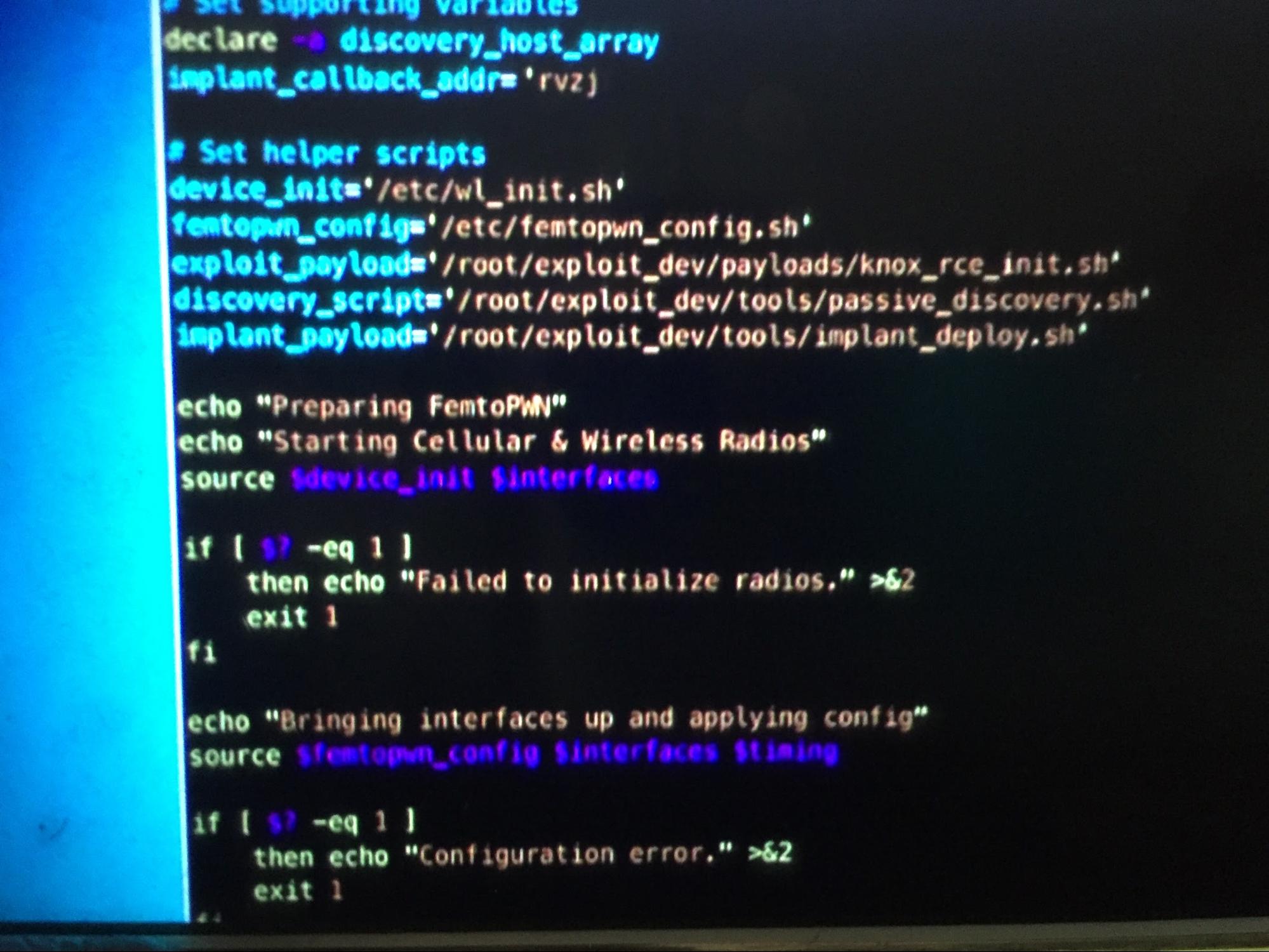
Matt: With that scene we get to see more of the femtocell source code. Maybe I can finally solve that Angela femtocell hack from last season. I think Tyrell was upset that Dark Army has plans of their own. The femtocell lets F Society in but also makes the backdoor and lets them hack the FBI.
Zachary: Not sure if we’ve seen this Easter egg yet, but the CnC for the compromised femtocell is https://www.rvzjtenpula.net/.
Harlo: I thought I saw a reference to a KNOX (Samsung) exploit, which was cute! Exploit-db has some sploits that aim to force installation of an APK (Android app) that has permissions necessary to do whatever to the affected phone.
Bill: ❤️ exploit-db. Carrying on the legacy of milw0rm.
Yael: So, uh, moving onto handcuffs… Tyrell didn’t need to break/dislocate his own thumb.
Matt: You need a metal pin or rod to pick handcuffs. He was without, so he improvised by dislocating his own thumb.
Yael: Or a coffee straw. You can sometimes squeeze your wrists out of the cuffs, but you have to make them really big when you’re getting cuffed. Maybe he should’ve grabbed a bobby pin before he planned his escape, though
Zachary: I like how Irving gives a mini social engineering lesson in the parking lot of the used car dealership, with his coffee mug to establish a connection.
Bill: He had a “#1 dad” travel coffee mug in hand.
Zach: And in his apartment, you see he has a bunch of different coffee mugs, all of which are probably lies: veteran, cat lover, God is my copilot. He goes on about how people want a connection.

Bill: Did you notice when Tyrell goes and shaves, he has a Power over Ethernet buzzer? Power over Ethernet is just getting power from an ethernet connection, but typically this is for routers, like Ubiquiti routers that sit outside and you only want to run a single line to. In this episode, his buzzer is powered over ethernet, and it looks like the same model as my own buzzer which is definitely not powered over ethernet.
Matt: Maybe in alternate future 2015 it is.