WikiLeaks Starts Releasing Source Code For Alleged CIA Spying Tools
Credit to Author: Emanuel Maiberg| Date: Thu, 09 Nov 2017 18:58:21 +0000
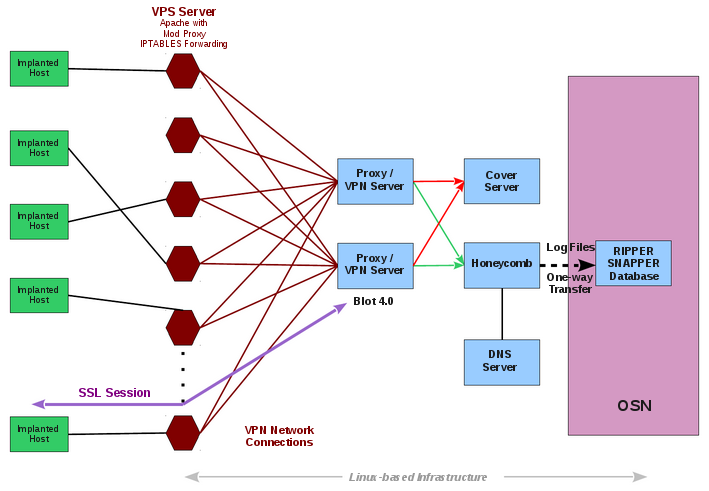
WikiLeaks published new alleged material from the CIA on Thursday, releasing source code from a tool called Hive, which allows its operators to control malware it installed on different devices. WikiLeaks previously released documentation pertaining to the tool, but this is the first time WikiLeaks has released extensive source code for any CIA spying tool.
This release is the first in what WikiLeaks founder Julian Assange says is a new series, Vault 8, that will release the code from the CIA hacking tools revealed as part of Vault 7.
“This publication will enable investigative journalists, forensic experts and the general public to better identify and understand covert CIA infrastructure components,” WikiLeaks said in its press release for Vault 8. “Hive solves a critical problem for the malware operators at the CIA. Even the most sophisticated malware implant on a target computer is useless if there is no way for it to communicate with its operators in a secure manner that does not draw attention.”
Read more: The Man Who Made the Mistake of Trying to Help Wikileaks
In March of this year, WikiLeaks revealed that it had obtained a cache of documents and hacking tools allegedly stolen from the CIA. The initial release was followed, in classic WikiLeaks style, by periodic new spills of docs and tools. But Assange and his colleagues decided not to publish code that might reveal unpatched bugs or vulnerabilities, so that these could be patched and so that people “can be secure.”
Instead, WikiLeaks contacted the affected companies to disclose them, but the negotiations with the companies—at least at the beginning—didn’t go very well, as WikiLeaks made demands without sharing information. Later, however, companies such as Cisco reported fixing vulnerabilities stemming from the leaks, indicating they either found them on their own or WikiLeaks finally told them.
Jake Williams, a former NSA hacker who now works at the security firm Rendition InfoSec, said that the code WikiLeaks released on Thursday doesn’t seem that dangerous, because it will just “help forensics professionals and cause CIA to refactor code, but nothing that will enable a cyberattack.”
But, he added “releasing code for other tools described in Vault 7 could give attackers the ability to exploit and implant new machines.”
“For instance, the code for Pandemic and Brutal Kangaroo tools could be a game changer,” Williams told me via Twitter direct message, referring to CIA tools that are used create persistent implants on Windows machines and to target closed Windows networks. “There’s still a possibility that an unpatched zero-day exists for USB infection as described in the Brutal Kangaroo documents.”
In its release, WikiLeaks said that materials published as part of Vault 8 will “not contain zero-days or similar security vulnerabilities which could be repurposed by others.”
Martijn Grooten, an editor at Virus Bulletin, agreed with Williams, saying that the data leaked on Thursday likely is not that useful for criminals, “not more than an average advanced malware analysis (or a DEF CON) talk is useful to them,” he said
WikiLeaks did not respond to a request for comment.
When reached for comment, the CIA referred me to its March 8 statement, where the spy agency said that it had “no comment on the authenticity of purported intelligence documents released by Wikileaks.”
Get six of our favorite Motherboard stories every day by signing up for our newsletter.