The weird and wonderful side of information security
Credit to Author: Julia Glazova| Date: Mon, 09 Jul 2018 13:00:26 +0000
Information security is a serious subject indeed, but everything is better with some good humor, and infosec is no exception. Today we cover five online projects that address security-related issues from an unusual angle.
123456+qwerty=♥
No matter how much we go on about the need for strong passwords, easily guessable strings such as 1q2w3e, iloveyou, and the like remain depressingly popular among users. “Who are these people?!” we exclaim whenever the latest analytical report on this topic is published. “What if they met each other?” pondered programmer Krzysztof Zając, who launched Words of Heart.
This site matches pairs of users who specify the same password during registration. At first, security experts believed the new resource to be the brainchild of cybercrooks. However, the Words of Heart creator soon revealed himself and explained that it was all just a bit of fun. Joking aside, it might prompt users to consider: “If I have the same password as 10 other people, maybe it’s not that strong?”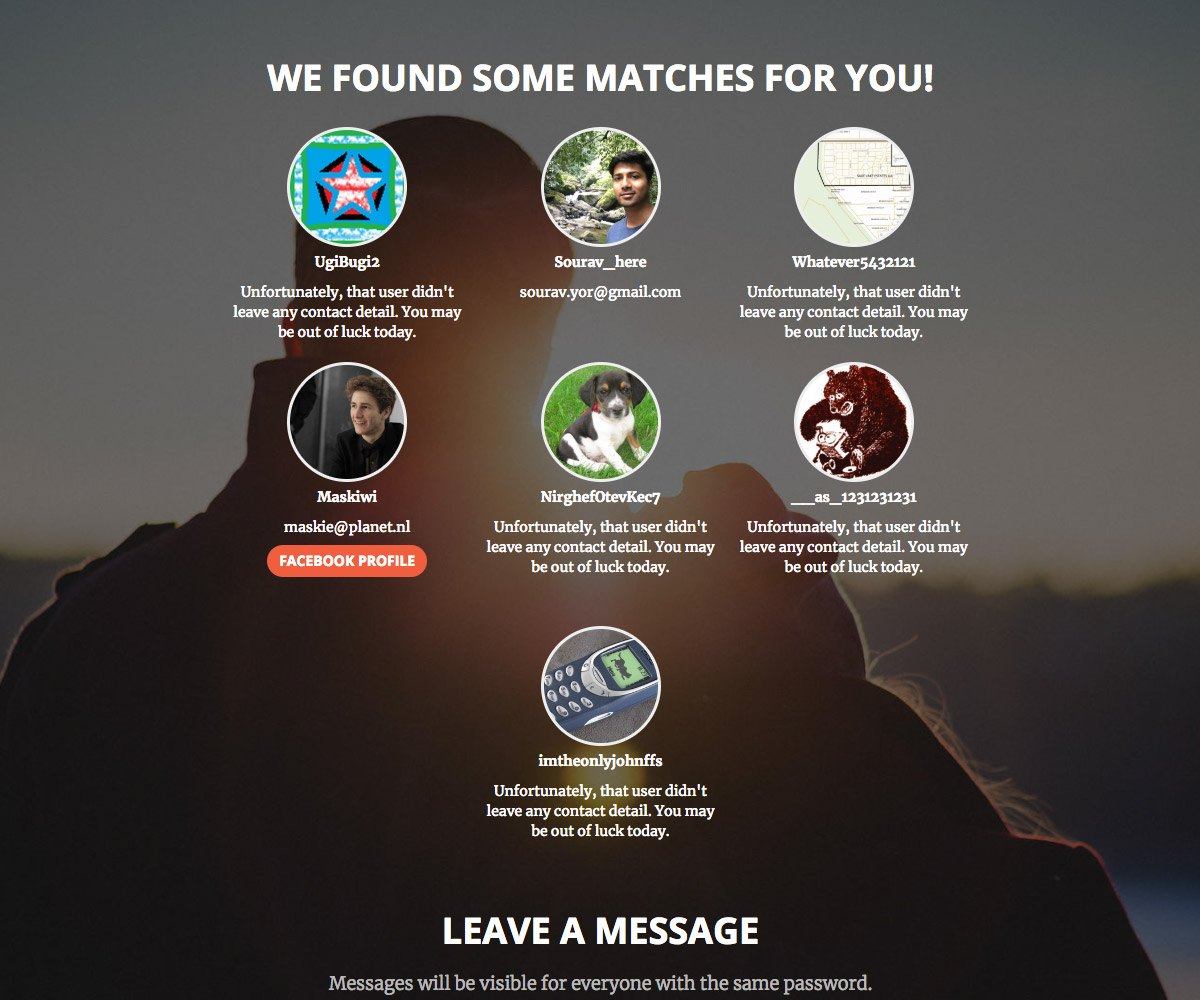
The traffic symphony
Ever heard an orchestra of computer hosts? Now you can, thanks to a team of US researchers who created a musical panorama of online traffic — or, rather, you could; the demonstration video was removed from YouTube for some unspecified reason. The team divided a stream of network data into different categories and linked each to its own sound: violin, cello, harp, xylophone, and others. The larger the volume of each type of data, the louder the sound of the corresponding instrument. The team says it even sounded pretty good.
Admittedly, the would-be composers were not doing it for aesthetic purposes only. Data transmission by sound (sonification) has long been used in different analytical and alarm systems. Sonifying Internet traffic helps monitor its intensity, a sharp increase in which can be a sign of a DDoS attack.
But the researchers went one step further, supplementing their “alarm” with a device for enabling anti-DDoS protection at the sound of a crescendo simply by squeezing…a tomato. And disabling it by means of a cucumber. Don’t ask why vegetables are involved; we have no idea. Whatever the case, the project authors proudly assert that it’s the first time a tomato has ever helped out with DDoS protection.
Eternal radio
Spam has become such a permanent fixture in our lives that we hardly notice it anymore, except perhaps when an important e-mail lands in the trash and we have to rummage through a load of garbage. When that happens, we get to gaze upon a feast of “unique offers” and untold Nigerian riches. This fount of human wisdom inspired an anonymous group of netizens to launch SpamRadio.com. That’s right, it’s spam-broadcasting radio.
Sadly, the site no longer broadcasts the 24/7 stream, but the site operators still offer audio of the original robot reading out a sampling of spam ads to the sound of light background music. All addresses are removed, so even if a particular offer tickles your fancy, you won’t be able to contact the seller. Which is just as well.
No humans allowed
Our century is not just high-tech minded; it’s geared toward fighting injustice. For example, UNESCO has started exploring the concept of robot rights. Who knows, maybe in 10 or 15 years’ time, our electronic brethren will also be in need of common-interest meetup groups where they can unwind after a hard day. If so, the face control technology for these groups and clubs already exists. See for yourself at HumansNotInvited.com.
Entry to the site is CAPTCHA-protected. The mechanics will be familiar to all Internet users: From the series of images displayed, those depicting a specific object need to be selected — only in this case, the illustrations are so blurred that the human eye cannot distinguish the images, whereas bots with machine vision have no problem. As did some Reddit users — suspicious creatures if you ask us…
Honey, I shortened the URL
The last site in our list does not tackle any major global problems and was created more in jest than anything else. You’ve probably heard of URL shorteners (aka link shrinkers, TinyURL and Bitly being perhaps the most well-known examples). There’s just one problem with these handy tools for shortening lengthy URLs: You never know exactly where such links point until you click (or until a snippet is preloaded). That makes them popular with scammers and shunned by savvy users.
ShadyURL is a shrinker that — you guessed it — shortens links, but it also makes them look as suspicious as possible (hence the name), even to the rookie eye. Here’s an example: http://www.5z8.info/bomb_shhf. Bomb, huh? In fact, the link points to our blog. But even if such links are perfectly harmless, it’s still not a bad idea to stay wary of them.