Feds Charge Three in Mass Seizure of Attack-for-hire Services
Credit to Author: BrianKrebs| Date: Thu, 20 Dec 2018 19:11:43 +0000
Authorities in the United States this week brought criminal hacking charges against three men as part of an unprecedented, international takedown targeting 15 different “booter” or “stresser” sites — attack-for-hire services that helped paying customers launch tens of thousands of digital sieges capable of knocking Web sites and entire network providers offline.
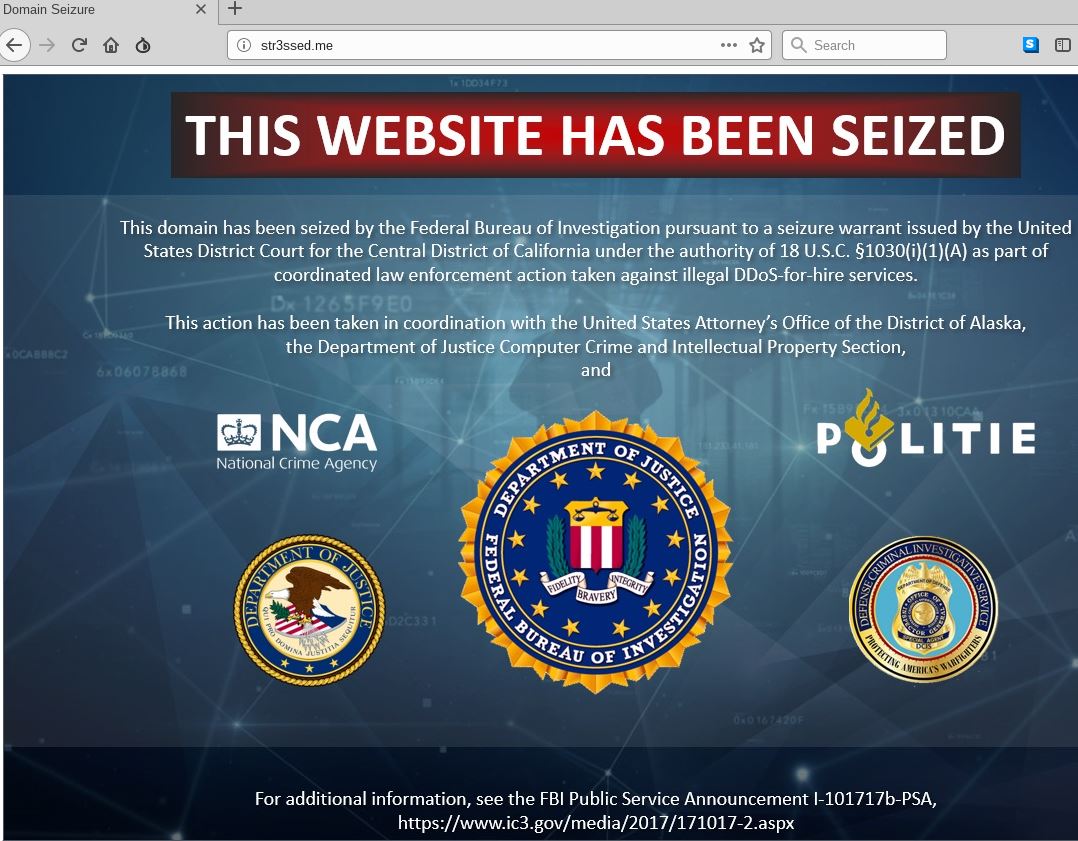
The seizure notice appearing on the homepage this week of more than a dozen popular “booter” or “stresser” DDoS-for-hire Web sites.
As of Thursday morning, a seizure notice featuring the seals of the U.S. Justice Department, FBI and other law enforcement agencies appeared on the booter sites, including:
anonsecurityteam[.]com
booter[.]ninja
bullstresser[.]net
critical-boot[.]com
defcon[.]pro
defianceprotocol[.]com
downthem[.]org
layer7-stresser[.]xyz
netstress[.]org
quantumnstress[.]net
ragebooter[.]com
request[.]rip
str3ssed[.]me
torsecurityteam[.]org
vbooter[.]org
Booter sites are dangerous because they help lower the barriers to cybercrime, allowing even complete novices to launch sophisticated and crippling attacks with the click of a button.
Cameron Schroeder, assistant U.S. attorney for the Central District of California, called this week’s action the largest simultaneous seizure of booter service domains ever.
“This is the biggest action U.S. law enforcement has taken against booter services, and we’re doing this in cooperation with a large number of industry and foreign law enforcement partners,” Schroeder said.
Booter services are typically advertised through a variety of methods, including Dark Web forums, chat platforms and even youtube.com. They accept payment via PayPal, Google Wallet, and/or cryptocurrencies, and subscriptions can range in price from just a few dollars to several hundred per month. The services are priced according to the volume of traffic to be hurled at the target, the duration of each attack, and the number of concurrent attacks allowed.
Purveyors of stressers and booters claim they are not responsible for how customers use their services, and that they aren’t breaking the law because — like most security tools — stresser services can be used for good or bad purposes. For example, all of the above-mentioned booter sites contained wordy “terms of use” agreements that required customers to agree they will only stress-test their own networks — and that they won’t use the service to attack others.
But experts say today’s announcement shreds that virtual fig leaf, and marks several important strategic shifts in how authorities intend to prosecute booter service operators going forward.
“This action is predicated on the fact that running a booter service itself is illegal,” said Allison Nixon, director of security research at Flashpoint, a security firm based in New York City. “That’s a slightly different legal argument than has been made in the past against other booter owners.”
For one thing, the booter services targeted in this takedown advertised the ability to “resolve” or determine the true Internet address of a target. This is especially useful for customers seeking to harm targets whose real address is hidden behind mitigation services like Cloudflare (ironically, the same provider used by some of these booter services to withstand attacks by competing booter services).
Some resolvers also allowed customers to determine the Internet address of a target using nothing more than the target’s Skype username.
“You don’t need to use a Skype resolver just to attack yourself,” assistant U.S. Attorney Schroeder said. “Clearly, the people running these booter services know their services are being used not by people targeting their own infrastructure, and have built in capabilities that specifically allow customers to attack others.”
Another important distinction between this week’s coordinated action and past booter site takedowns was that the government actually tested each service it dismantled to validate claims about attack firepower and to learn more about how each service conducted assaults.
In a complaint unsealed today, the Justice Department said that although FBI agents identified at least 60 different booter services operating between June and December 2018, they discovered not all were fully operational and capable of launching attacks. Hence, the 15 services seized this week represent those that the government was able to use to conduct successful, high-volume attacks against their own test sites.
“This is intended to send a very clear message to all booter operators that they’re not going to be allowed to operate openly anymore,” Nixon said. “The message is that if you’re running a DDoS-for-hire service that can attack an Internet address in such a way that the FBI can purchase an attack against their own test servers, you’re probably going to get in trouble.”
DOWN THEM ALL
Charged in a Los Angeles federal court this week were the alleged operators of “Downthem” — a booter service the government says helped some 2,000 customers launch debilitating digital assaults at more than 200,000 targets, including many government, banking, university and gaming Web sites.
Prosecutors say that in addition to running and marketing Downthem, defendants Matthew Gatrel from St. Charles, Ill., and Juan Martinez of Pasadena, Calif. sold huge, continuously updated lists of Internet addresses tied to devices that could be used by other booter services to make attacks far more powerful and effective.
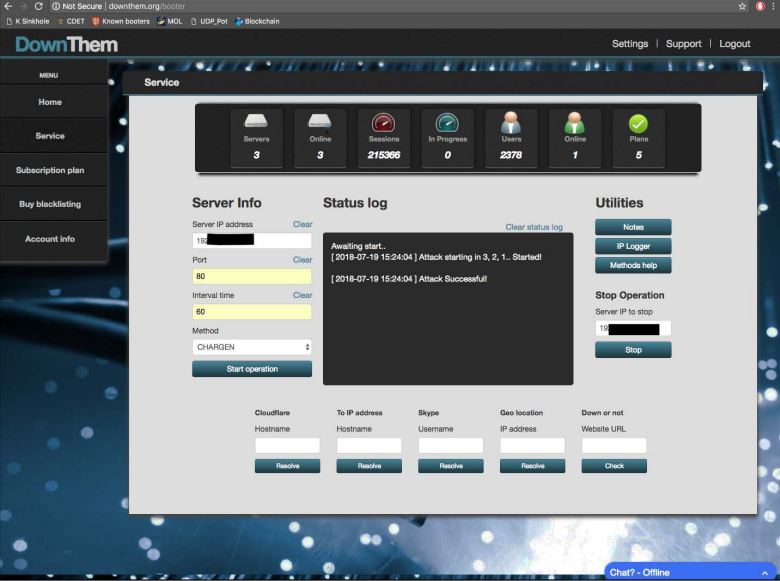
The user interface for Downthem[.]org, one of 15 booter sites seized by the feds today.
Booter and stresser services let customers pick from among a variety of attack methods, but almost universally the most powerful of these methods involves what’s known as a “reflective amplification attack.” In such assaults, the perpetrators leverage unmanaged Domain Name Servers (DNS) or other devices on the Web to create huge traffic floods.
Ideally, DNS servers only provide services to machines within a trusted domain — such as translating an Internet address from a series of numbers into a domain name, like example.com. But DNS reflection attacks rely on consumer and business routers and other devices equipped with DNS servers that are (mis)configured to accept queries from anywhere on the Web.
Attackers can send spoofed DNS queries to these DNS servers, forging the request so that it appears to come from the target’s network. That way, when the DNS servers respond, they reply to the spoofed (target) address.
The bad guys also can amplify a reflective attack by crafting DNS queries so that the responses are much bigger than the requests. For example, an attacker could compose a DNS request of less than 100 bytes, prompting a response that is 60-70 times as large. This “amplification” effect is especially pronounced if the perpetrators query dozens of DNS servers with these spoofed requests simultaneously.
The government alleges that Gatrel and Martinez constantly scanned the Internet for these misconfigured devices, and then sold lists of Internet addresses tied to these devices to other booter service operators.
Schroeder said the government is arguing that the use of these third-party servers in reflective amplification attacks can be prosecuted under existing wire fraud and computer trespass laws.
“Certainly [booter service operators] don’t have permission from all of those other devices owners to use the devices and their bandwidth to direct these attacks,” she said. “We look at it as a wire fraud violation because essentially they’re stealing property from upstream providers and using their resources to conduct these attacks. There are also multiple ways we can show this is pretty clearly not lawful under the Computer Fraud and Abuse Act.”
Prosecutors further allege Gatrel resold his booter services to other booter operators, including Quantum Stresser — one of the 15 services seized by the government this week. The alleged operator of that service, Pennsylvania resident David Bukoski, was charged in the District of Alaska this week for aiding and abetting computer intrusions.
Investigators say Bukoski’s booter service was among the longest running services targeted by the FBI, operating since at least 2012. An indictment against Bukoski unsealed this week maintains Quantum Stresser had over 80,000 customer subscriptions, and that during 2018 the service was used to conduct over 50,000 actual or attempted attacks targeting people and networks worldwide.
According to the government, the use of booter and stresser services to conduct attacks is punishable under both wire fraud laws and the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in arrest and prosecution; seizure of computers or other electronics; significant prison sentences; a penalty or fine.
Schroeder said the government understands this week’s takedowns aren’t going to solve the booter problem once and for all, and that other booter services will likely spring up in the wake of those dismantled this week. But she said the arrests and seizures have helped build a template that the government can use in tandem with its industry partners to shorten the lifespan of new booter services and to bring those responsible to justice.
“We certainly don’t expect this problem to go away after this,” Schroeder said. “But this is an attempt to build a strategic approach to this problem, to look at it in a more systemic way and deal with it on a much larger scale.”
The Justice Department’s press release about this action is here.
This is a developing story and may be updated throughout the day. Any substantive updates will be noted here with a timestamp.
Update, 2:42 p.m. ET: Added link to DOJ press release.