Cloud Hosting Provider DataResolution.net Battling Christmas Eve Ransomware Attack
Credit to Author: BrianKrebs| Date: Wed, 02 Jan 2019 18:32:37 +0000
Cloud hosting provider Dataresolution.net is struggling to bring its systems back online after suffering a ransomware infestation on Christmas Eve, KrebsOnSecurity has learned. The company says its systems were hit by the Ryuk ransomware, the same malware strain that crippled printing and delivery operations for multiple major U.S. newspapers over the weekend.
San Juan Capistrano, Calif. based Data Resolution LLC serves some 30,000 businesses worldwide, offering software hosting, business continuity systems, cloud computing and data center services.
The company has not yet responded to requests for comment. But according to a status update shared by Data Resolution with affected customers on Dec. 29, 2018, the attackers broke in through a compromised login account on Christmas Eve and quickly began infecting servers with the Ryuk ransomware strain.
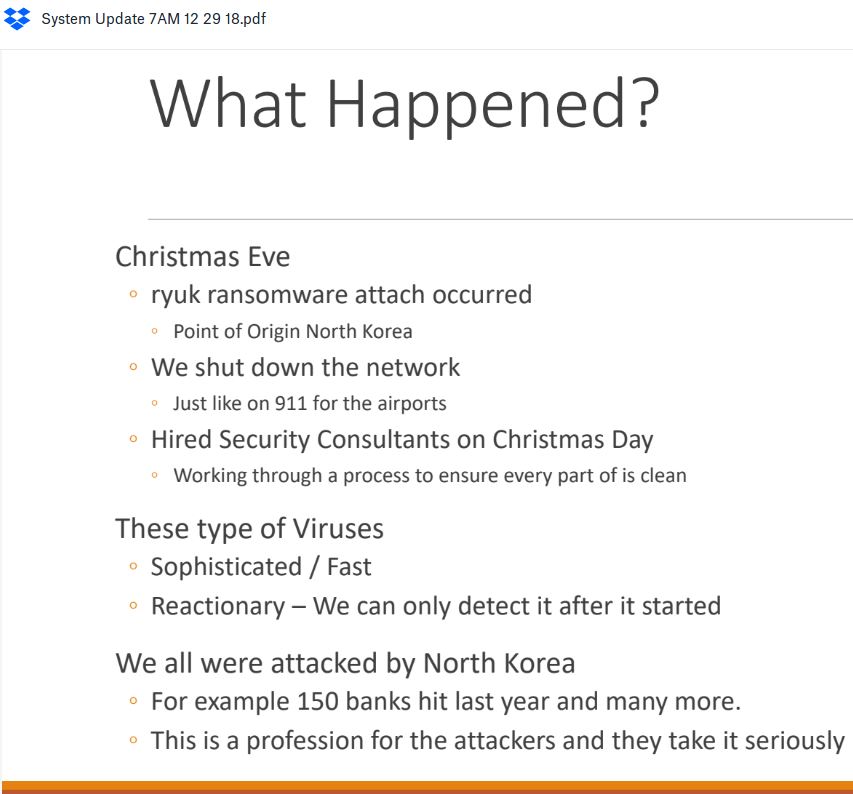
Part of an update on the outage shared with Data Resolution customers via Dropbox on Dec. 29, 2018.
The intrusion gave the attackers control of Data Resolution’s data center domain, briefly locking the company out of its own systems. The update sent to customers states that Data Resolution shut down its network to halt the spread of the infection and to work through the process of cleaning and restoring infected systems.
Data Resolution is assuring customers that there is no indication any data was stolen, and that the purpose of the attack was to extract payment from the company in exchange for a digital key that could be used to quickly unlock access to servers seized by the ransomware.

A snippet of an update that Data Resolution shared with affected customers on Dec. 31, 2018.
The Ryuk ransomware strain was first detailed in an August 2018 report by security firm CheckPoint, which says the malware may be tied to a sophisticated North Korean hacking team known as the Lazarus Group.
Ryuk reportedly was the same malware that infected the Los Angeles Times‘ Olympic printing plant over the weekend, an attack that led to the disruption of newspaper printing and delivery services for a number of publications that rely on the plant — including the Los Angeles Times and the San Diego Union Tribune.
A status update shared by Data Resolution with affected customers earlier today indicates the cloud hosting provider is still working to restore email access and multiple databases for clients. The update also said Data Resolution is in the process of restoring service for companies relying on it to host installations of Dynamics GP, a popular software package that many organizations use for accounting and payroll services.

A status update shared by Data Resolution with affected customers on Jan. 2, 2018 shows the company is still struggling to restore services more than a week after the attack began.
Cloud hosting providers are often pitched as a way for companies to increase security and to better protect themselves from threats like ransomware, which scrambles data on infected systems and demands payment in exchange for a digital key needed to unlock affected systems.
At the same time, cloud providers represent an especially attractive target for ransomware attacks because they store vast amounts of data for other companies. In 2017, cloud hosting provider Cloudnine was hit by a ransomware attack, leading to an outage that lasted for several days.
Much depends on security practices maintained by each provider, according to an MIT Technology Review story last year that named cloud ransomware attacks as a top security concern for 2018
“The biggest cloud operators, like Google, Amazon, and IBM, have hired some of the brightest minds in digital security, so they won’t be easy to crack,” wrote Martin Giles. “But smaller companies are likely to be more vulnerable, and even a modest breach could lead to a big payday for the hackers involved.”
A source at a company that uses Data Resolution to manage payroll payments told KrebsOnSecurity that the cloud hosting provider said it did not attempt to pay the requested ransom, preferring to restore systems from backups instead.