How to hack a hardware cryptocurrency wallet
Credit to Author: Alex Drozhzhin| Date: Thu, 10 Jan 2019 12:56:02 +0000
Hardware wallets are considered to be the most secure type of cryptocurrency wallet. However, nothing is 100% secure, and they can be compromised just as well. At the 35th Chaos Communication Congress, security researchers Thomas Roth, Dmitry Nedospasov, and Josh Datko demonstrated several ways to do it. But before we jump into hacking, a little background on what a hardware wallet actually is and how it works.
What is a cryptocurrency wallet?
First of all, let’s talk a bit about what a cryptocurrency wallet is in general. To put it simply, a wallet is a cryptocurrency account. The “account” consists of a pair of cryptographic keys, one public and one private. These two keys have some resemblance to login and password pairs: The public key is used as a wallet address, and the private key is used to access coins — that is, to sign outgoing transactions.
Another thing worth mentioning is how multiple public–private key pairs are generated in cryptocurrency systems for multiple wallets belonging to the same person. It might be inconvenient to store several completely independently generated key pairs. So what cryptocurrency systems really do is generate just one big number called a cryptographic seed and derive multiple public–private key pairs from the seed in a predictable manner for multiple wallets.
This one big number — the cryptographic seed — is what a user of a cryptocurrency system actually stores.
Unlike traditional financial systems, cryptocurrencies usually have no centralized authority, no registration mechanisms, nothing like chargeback insurance, and no account recovery options. Anyone who owns the cryptographic seed and therefore the keys derived from it, owns the corresponding cryptocurrency wallets. And if the seed is stolen or lost, so are the coins in the wallets.
By the way, formally a wallet is a pair of public–private keys. However, most of the time means of storing those keys are also referred to as wallets. If you put it this way, a hardware wallet is a device that stores cryptocurrency wallets. Easy, right?
Why would anyone need a hardware cryptocurrency wallet?
As you can imagine, it’s a good idea to keep this Very Important Seed as safe as possible. There are plenty of ways to store the seed, each with pros and cons. The most convenient method is storing the seed either in your computer or smartphone, or, even handier, online. However, malware hunting for cryptocurrency wallets is not uncommon at all. As for the online wallet services, they can be hacked and even go bankrupt, with large amounts of coins disappearing.
On top of that, further problems plague wallets, including phishing, payment information spoofing, loss of wallets due to hardware failure, and so on and so forth — so much so that at some point people decided to solve the mess by making hardware cryptocurrency wallets, dedicated devices designed to store cryptographic seeds reliably and safely.
How hardware cryptocurrency wallets work
The main idea behind a hardware cryptocurrency wallet is to store the cryptographic seed in a manner that it never leaves the device. All the cryptosigning stuff is done inside the wallet, not on a computer that it is connected to. Therefore even if your computer gets compromised, the invaders won’t be able to steal your keys.
In addition it would be nice to have some access-protection measures — like locking the device with a PIN code. And of course it would be quite useful for a hardware wallet user to be able to verify the actual transaction on the device and to either confirm or deny it.
All these considerations define the most suitable design: Usually a hardware cryptocurrency wallet is a relatively small USB-connected dongle that has a display and some buttons that are used for PIN entering and transaction confirmation.
However, the inner workings of such devices can vary. The two leading manufacturers of hardware wallets — Trezor and Ledger — represent two different approaches to the hardware design.
Ledger’s approach: The cryptographic seed is stored in the Secure Element chip
Ledger’s devices — namely Ledger Nano S and Ledger Blue — have two main chips. One is Secure Element, a microcontroller designed to store highly sensitive cryptographic data. More specifically, these chips are used in SIM cards, in chip-and-PIN banking cards, and in Samsung Pay– and Apple Pay– compatible smartphones.
The second chip is a general purpose microcontroller that handles peripheral tasks: maintaining USB connection, controlling display and buttons, and so on. In effect, this microcontroller acts like a middleman between the Secure Element and everything else, including the user. For example, every time the user has to confirm a transaction, they are actually going through this general purpose microcontroller, not the Secure Element chip.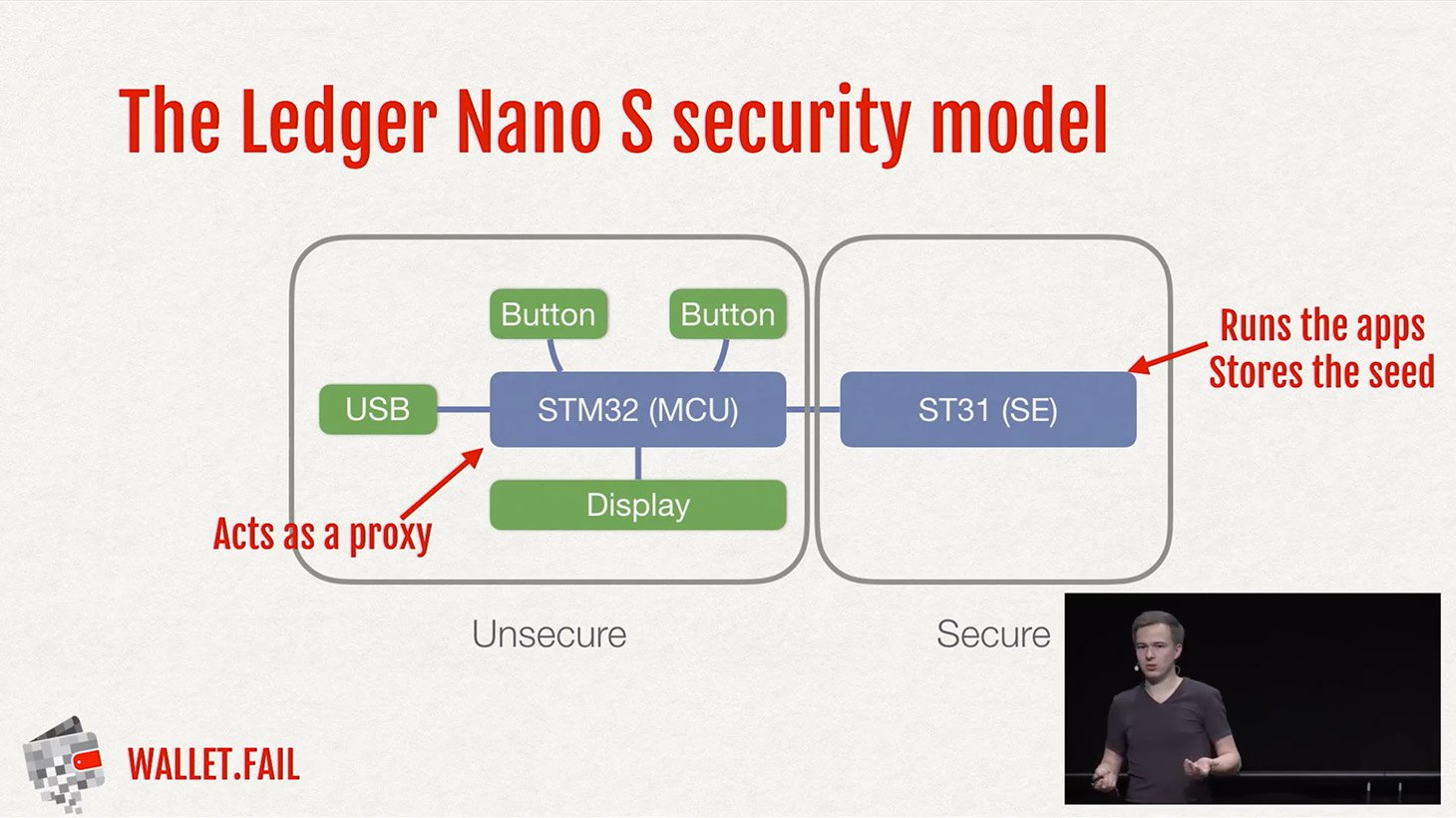
However, even storing cryptographic seeds in a protected chip doesn’t make Ledger’s device entirely impenetrable. For one thing, although it is very hard to hack into a Secure Element directly and steal a cryptographic seed, it’s relatively easy to compromise a general purpose microcontroller and thereby deceive a hardware wallet to confirm an outsider’s transactions.
Researchers inspected the Ledger Nano S firmware and found that it can be re-flashed with a compromised version if a certain value is written to a certain memory address. This memory address is blacklisted to make it unwritable. However, the microcontroller that is used in the device supports memory remapping, which changes the address to accessible. Researchers exploited this feature and uploaded modified firmware into the Nano S. For demonstration purposes, this modified firmware contained a Snake game. However, this modified firmware could contain, for example, a malicious module that changes wallet addresses in all outgoing transactions.
An alternative approach to compromise a hardware wallet is to use a hardware implant. Josh Datko managed to insert into a Ledger Nano S a cheap RF-triggered implant that pushes the confirmation button upon receiving a malicious radio command. The same method probably works with any hardware wallet; the researcher chose Ledger Nano S because it is one of the smallest, and therefore the most challenging for this physical attack.
Another device by the same manufacturer, the Ledger Blue, turned out to be vulnerable to side-channel attacks. Ledger Blue is a hardware wallet with a really large display and a big battery. It has a circuit board design flaw that leaks pretty distinguishable RF signals when the user is entering a PIN code. Researchers recorded the signals and trained a machine-learning algorithm to recognize them with 90% accuracy.
Trezor’s approach: The cryptographic seed is stored in the general-purpose microcontroller’s flash memory
Trezor’s devices work a bit differently. They don’t use a Secure Element, so everything in the device is controlled by a single chip, a general purpose microcontroller based on ARM architecture. This chip is responsible both for cryptographic data storage and processing, and for managing the USB connection, display, buttons, and so on.
Theoretically this design approach could make it easier to hack the device’s firmware and thus get access to the cryptographic seed stored in the microcontroller’s flash memory. However, as the researchers said, Trezor did a really good job with hardening the firmware, so researchers had to go for hardware hacking, where they found success.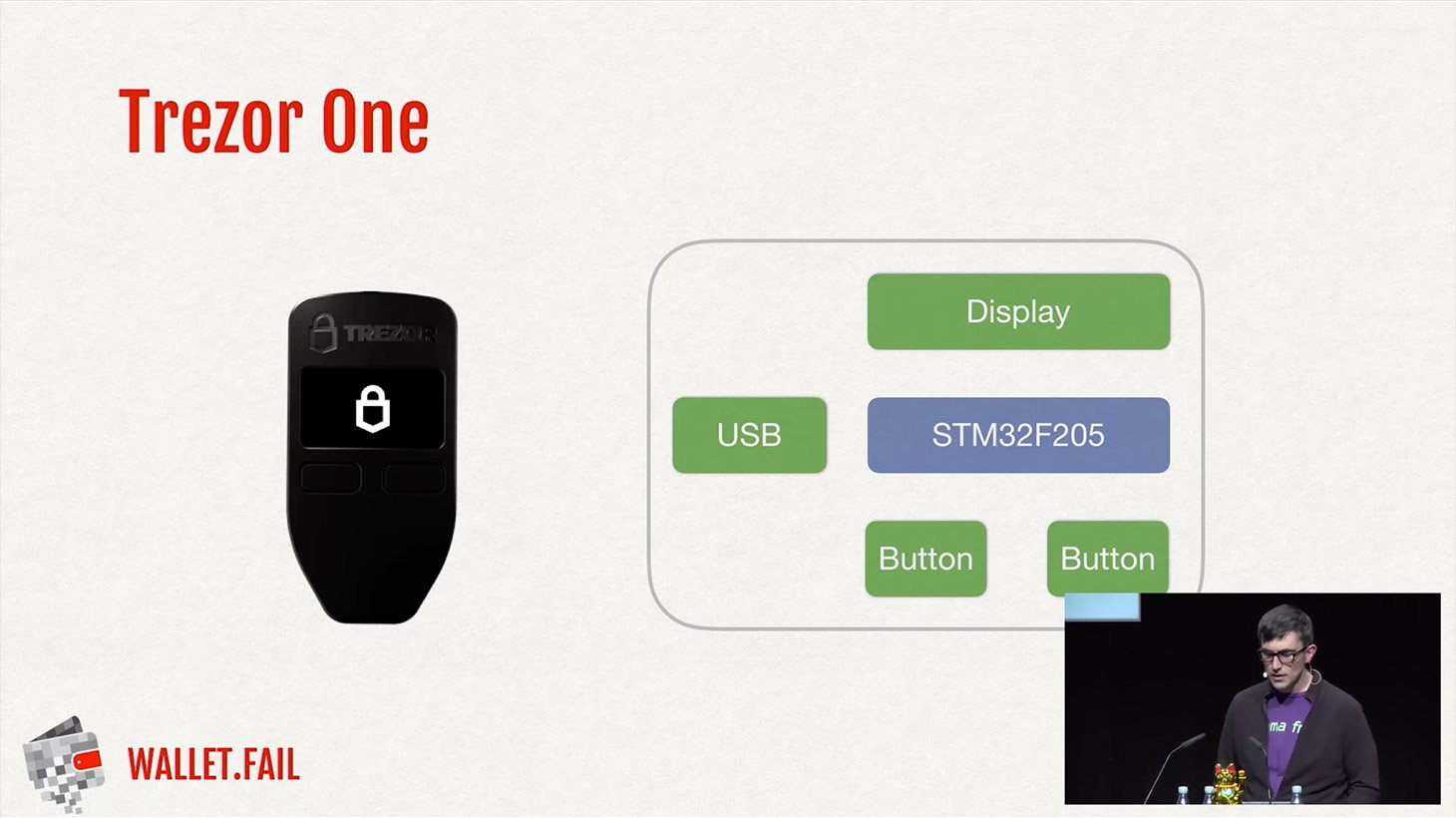
Using a hacking technique called voltage glitching (applying lowered voltage to a microcontroller, which causes funny effects in the chip) they switched Trezor One’s chip state from “no access” to “partial access,” which allowed them to read the chip’s RAM, but not the flash storage. After that they found out that when the firmware upgrade process is started, the chip places the cryptographic seed into RAM to retain it while the flash is being overwritten. In this manner, they managed to get all memory contents. Finding the cryptographic seed in this dump turned out to be no problem; it was stored in RAM unencrypted, in the form of a mnemonic phrase (meaning actual words instead of random number) that was easy to spot.

The memory dump contains the cryptographic seed in the form of mnemonic phrase and PIN (in this case, it’s 1234), stored in plain text
Conclusions
I have to mention here that most of the hacks described by Thomas Roth, Dmitry Nedospasov, and Josh Datko are quite sophisticated — and they require physical access to the device. So don’t rush to throw your Ledger or Trezor into a trash bin. As long as no one has access to it, your bitcoins should be fine (though somewhat depreciated).
Nevertheless, it’s a good idea to keep in mind the existence of supply chain attacks. Hardware wallets are relatively easily tampered with and can be compromised even prior to purchase. Of course, the same goes for regular laptops or smartphones. However, attackers can’t be sure if a particular laptop will be used for cryptocurrency storage. Hardware wallets, in this context, are a sure thing.
Manufacturers of hardware wallets are trying to address the problem, for example by using security stickers on devices’ packages and creating pages on their websites that allow customers to perform online security checks of their wallets. However, these measures may not be helpful enough, and they can even be confusing.
Anyway, unlike some other hardware wallets, Ledger’s and Trezor’s devices are designed with security in mind. Just don’t assume that they are 100% unhackable. Take a few additional steps to protect your cryptofortune:
- Buy hardware cryptocurrency wallets only from trusted vendors.
- When buying, check thoroughly for any signs of tampering.
- To be more certain pop the device open and make sure no extra elements are attached to the circuit board.
- Store your cryptowallet in a safe place, and don’t allow people you don’t trust to get their hands on it.
- Protect the computer you use for cryptocurrency with reliable security software. A good part of the hacks described above require malware to be installed on the computer the hardware wallet is connected to.
Extra Trezor tips:
- Trezor is an open-source platform, both software and hardware. So if you are skilled enough with electronics, you can build your own hardware wallet using off-the-shelf components. This way you can be 100% sure nobody has messed with the hardware part of your wallet.
- Trezor devices provide extra protection with a passphrase to protect from seed extraction hacks (the idea of this mode is that the stored seed is incomplete without the passphrase). Consider using this mode.
Here’s the original talk. Have a look — it’s both entertaining and helpful for hardware wallets users.