The ATM of Fortune
Credit to Author: Leonid Grustniy| Date: Thu, 21 Feb 2019 09:22:48 +0000
It sounds like a weird dream: ATMs that look more like slot machines. If you try your luck, you might even be rewarded with a nice bundle of cash. Could it be true?
WinPot: A jackpotting tool
In fact, the ability to turn a common ATM into something like a slot machine is real — and not dreamy at all. Actual malware called WinPot can do just that. Perhaps its creators were inspired by the term jackpotting, which commonly refers to attacks where cybercriminals force an automated teller machine to spew out money. Whimsically, they decided to make using WinPot look like playing slots for money mules, individuals who pick up the loot from ATMs.
Unlike machines in a casino, WinPot can make the “ATM game” a sure-fire win, which could explain the first part of the name. The software helps criminals pick and empty the ATM’s most lucrative cash-dispensing cassette.
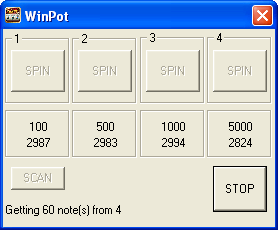
The slot machine’s windows display each cassette’s bill denomination and the number of bills inside the cassette. All the mule needs to do is select the cassette with the most money in it and press Spin. The Scan button can be used to recount the bills. WinPot’s creators also provided an emergency Stop button for helping the mule cut the payout short before raising suspicions.
Versions of WinPot are notably diverse, each with its own unique features. For example, certain flavors of the malware operate for a limited period of time (e.g. a month) and then silently deactivate themselves. The core feature set, though, is roughly consistent; the diversity helps it both adapt to new protective measures for ATMs and prevent abuse by mules, who might try to copy the software to keep all of the bounty.
Jackpot, but not for everyone
The upshot is, if you notice anything odd about an ATM’s appearance or operation, it’s unlikely to mean good news for you. Cybercriminals go far beyond robbing ATMs. Their arsenals include ways to steal cash from bank clients: hidden cameras, fake keypads, skimmers, and other devices for obtaining PINs and data from a card’s magnetic strip — in other words, everything they need to produce a duplicate and use it without your involvement.
Sometimes, though, dangers lurk inside perfectly normal-looking and working ATMs. Therefore, it is key to remember the basic …
… safety rules when using ATMs
- Activate text-message notifications about withdrawals and transfers to make sure that if someone else gets access to your card, you’ll learn about it sooner rather than later so you can block the card immediately.
- Use ATMs that are hard for criminals to approach and reprogram, or to install a device on. A bank branch or other well-guarded location is best.
- Stand as close to the terminal as you can and cover the keypad with your hand while entering your PIN. Doing so helps prevent criminals from tracking you with a camera hidden somewhere near the ATM — or doing it the old-fashioned way, by peeping over your shoulder.
- Pay attention to anything strange about the ATM’s external appearance or what is displayed on its screen. If anything arouses your suspicion, err on the side of caution and choose another ATM rather than potentially being left without cash in your account. Better yet, contact the bank. Even if you actually see that tempting WinPot interface with its Spin button, remember: Theft is theft, and thieves go to jail sooner or later.