Compiling Open Source Threat Intelligence for Threat Hunts
Credit to Author: Mat Gangwer| Date: Wed, 15 Jan 2020 10:02:05 +0000
In addition to normal tradecraft adaptations, any time a change in the geopolitical landscape takes place, cyberattack campaigns and adversary behaviors typically shift as well. The recent events with Iran and the United States offer a relevant use case for organizations and have highlighted the benefit of having a threat intelligence driven hunting process.
The intent of this article is to show a method on how organizations can leverage threat intelligence sources to help align their threat hunting program and analyze if they’re impacted by these shifts. The end goal is not to say our organization can detect (adversary group X), instead leveraging the methods to validate core capabilities such as
- Are the necessary data sources available to the threat hunting team?
- Is detection or prevention logic in place to allow for easy identification and analysis?
- Is it possible to easily hunt for new relevant indicators of compromise or indicators of attack?
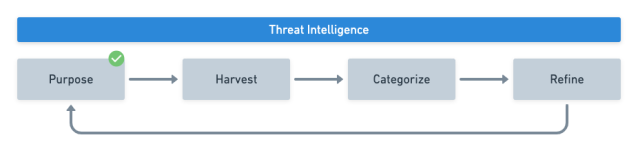
The Threat Intelligence Cycle
Purpose, harvest, categorize, and refine are the four phases of the threat intelligence cycle that focus on open source threat intelligence (otherwise known as OSINT). These phases foster consistency in collecting and analyzing data to be used for threat hunting.
Purpose
In this first step of the threat intelligence cycle, determine the purpose of the threat intelligence and how it will be applied. Use questions to guide the overarching goal of the threat hunting effort.
Using the most recent real world example of geopolitical change, a common question to ask is, “Do we see any known indicators of compromise (IOCs) or indicators of attack (IOAs) from adversary groups publicly attributed to state sponsored cyber campaigns from Iran?” Once a question has been ratified, the next step is to deconstruct the question to identify what to harvest in the next phase of the intelligence cycle.
The question above will be used as an example throughout this article, on how to apply this method.
Harvest
Intelligence sources vary widely, from feeds that can be purchased, information shared from industry specific Information Sharing and Analysis Centers (ISACs), data that can be gathered from Twitter, and information shared from organizations such as the FBI’s InfraGard. Regardless of where the data is obtained, a key factor is confidence in the data set.
All threat intelligence sources must be scrutinized (XREF TO INTEL POST), and efforts should be focused on those with the highest confidence factor. This will help reduce the overhead spent in conducting threat hunts, and lead to more valuable insights when performing the analysis.
In this example, the MITRE attack group repository is the OSINT location of choice. The links below detail which adversary groups are attributed to state sponsored cyber campaigns from Iran.
Iranian associated Adversary Groups:
- https://attack.mitre.org/groups/G0064/
- https://attack.mitre.org/groups/G0087/
- https://attack.mitre.org/groups/G0058/
- https://attack.mitre.org/groups/G0003/
- https://attack.mitre.org/groups/G0052/
- https://attack.mitre.org/groups/G0043/
- https://attack.mitre.org/groups/G0077/
- https://attack.mitre.org/groups/G0059/
- https://attack.mitre.org/groups/G0069/
- https://attack.mitre.org/groups/G0049/
Once the groups have been identified, collect the IOCs and IOAs that have been used by those adversary groups in previous cyber campaigns. To do this use the reference sources utilized to identify the groups’ tactics and techniques, provided by MITRE ATT&CK at the bottom of each adversary group page. Once the IOC and IOA artifacts have been gathered, they can be categorized for threat hunting.
Categorize
Categorization begins with identifying what category the IOC or IOA relates too. This is important to help identify for the threat hunting team what data can then be searched and analyzed to observe if the IOCs or IOAs are present.
Frameworks such as STIX offer a standard language and format for classifying observables. There is no right or wrong answer to categorization; Using something the organization is familiar with is often the best approach.
Generalized data categories were identified and used in this example. They are as follows:
- Hash
- IP
- Command
- Domain
- Port
- Filename
- Registry
- Exploit
- CVE
The IOC and IOA artifacts should be associated to the adversary group and the source reference. This will allow for the threat hunting team to pivot on the IOCs/IOAs if there is a suspected true positive. This also allows for prioritization of the indicators that are most relevant to the organization based on refinement.
We’ve published a categorized list of unrefined IOCs, put together using the method described above, to our Github.
Refine
Refinement is the act of researching what IOCs and IOAs are relevant to detection and threat hunting capabilities and identifying which IOCs and IOAs are immediately actionable and which IOCs and IOAs may pose visibility or coverage gaps. Specific questions should be asked of each category to determine if an organization has the capability to detect or threat hunt those IOCs or IOAs.
An example question would be, “Is the necessary data being collected for each category easily retrievable and reviewable?” This highlights the need for being able to historically analyze data to hunt for the IOCs. Whereas if the question was posed slightly different, “Will detections or alerts be created based on these IOCs?” highlights the need for creation of rules which provide real-time alerting if the IOCs are observed.
It is critical for the threat hunting team to refer back to the question(s) defined in the first phase “purpose” to understand the use case for which the threat intelligence IOCs will be used. Some of the observables, such as common port usage, will have a high false positive rate and would not make strong detection rules. However, when threat hunting, this data can be correlated with other observables if discovered to provide additional context.
Using the example of Iranian adversary groups, one method would be to highlight the intersection of their defined techniques and focus threat hunting efforts in those areas first. This can be accomplished using the MITRE ATT&CK Navigator, and loading this JSON file.
The following illustrates the most common techniques (darker red = more common) employed by the various adversary groups and provides a starting point.
Once the IOCs and IOAs have been refined threat hunting can now begin and detections/alerts/signatures can be created for real-time results. There should be a high level of confidence that they will be actionable against the defined purpose.
If the results after refinement are not producing rich and useful data, the process can be reperformed. Reframe the initial purpose, harvest new data, or categorize it differently to meet the objectives. Often times it can take more than one cycle through the process to get it right.