Multiple attackers increase pressure on victims, complicate incident response
Credit to Author: Matt Wixey| Date: Tue, 09 Aug 2022 11:00:04 +0000
There’s a well-worn industry phrase about the probability of a cyberattack: “It’s not a matter of if, but when.” Some of the incidents Sophos recently investigated may force the industry to consider changing this rule-of-thumb: The question is not if, or when – but how many times?
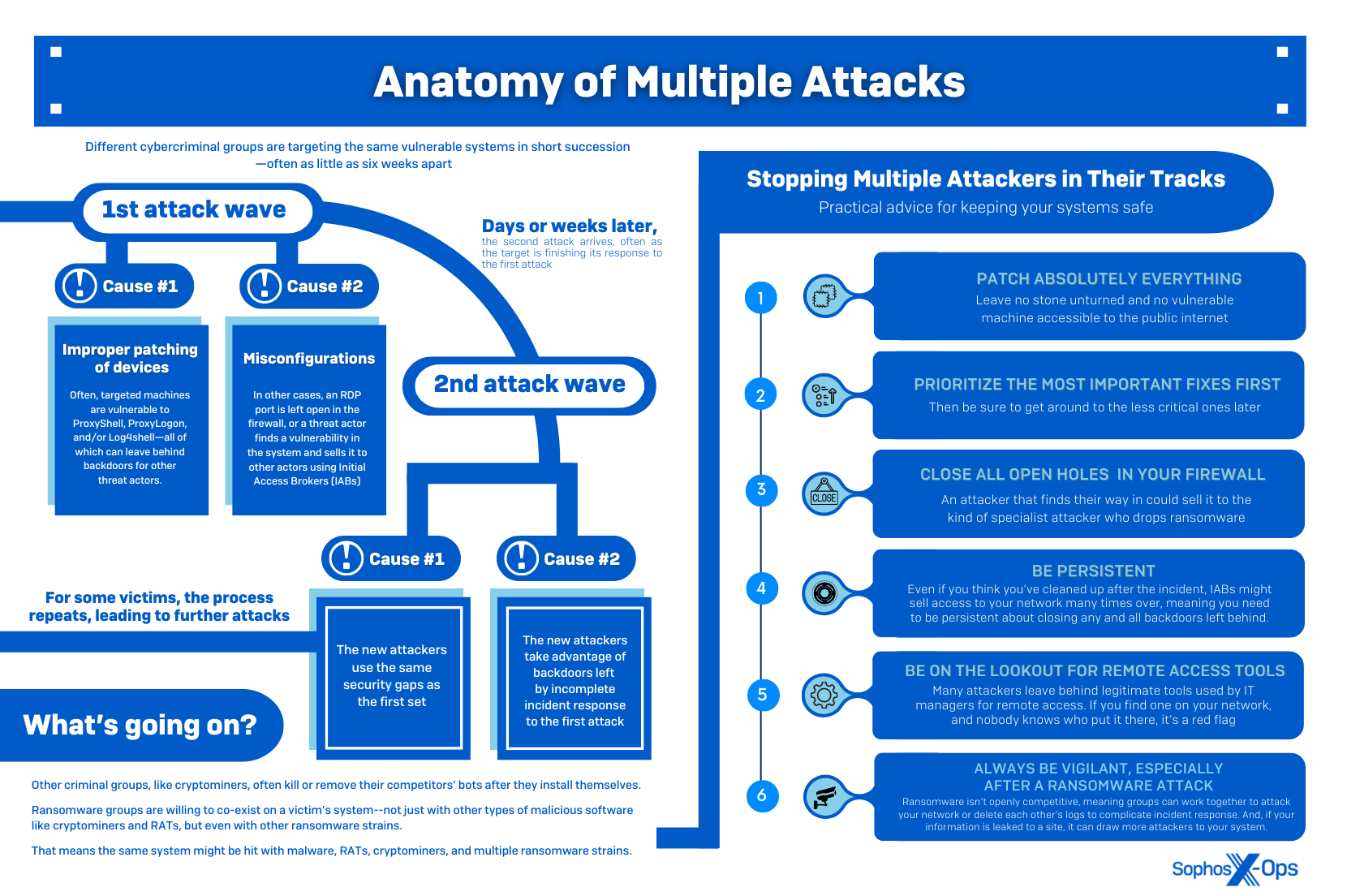
In an issue we highlighted in our Active Adversary Playbook 2022, we’re seeing organizations being hit by multiple attackers. Some attacks take place simultaneously; others are separated by a few days, weeks, or months. Some involve different kinds of malware, or double – even triple – infections of the same type.
Today, Sophos X-Ops is releasing our latest Active Adversary white paper: Multiple Attackers: A Clear and Present Danger. In the paper, we take a deep dive into the problem of multiple attackers, exploring how and why organizations are attacked several times. Recent case studies from our Managed Detection and Response (MDR) and Rapid Response (RR) teams provide insight into the how, and exploring cooperation and competition among threat actors helps explain the why.
Our key findings are:
- The key drivers of multiple exploitations are vulnerabilities and misconfigurations going unaddressed after a first attack
- Multiple attacks often involve a specific sequence of exploitation, especially after big, widespread vulnerabilities like ProxyLogon/ProxyShell are disclosed – with cryptominers arriving first, followed by wormable botnet builders, RATs, initial access brokers (IABs), and ransomware
- While some threat actors are interdependent (e.g., IABs later enabling ransomware), others, such as cryptominers, try to terminate rival malware, and may even ‘close the door’ by patching vulnerabilities or disabling vulnerable services after gaining access
- Historically, threat actors have been protective of their infections, to the extent of kicking rivals off compromised systems
- Ransomware actors, despite occasionally tangling with each other, seem less concerned about competition, and sometimes adopt strategies which directly or indirectly benefit other groups
- Certain features of the underground economy may enable multiple attacks – for instance, IABs reselling accesses, and ransomware leak sites providing data that other threat actors can later weaponize
- Some of the case studies we analyze include a ransomware actor installing a backdoor which was later abused by a second ransomware group; and an incident where one organization was attacked by three ransomware groups in the space of a few weeks, all using the same misconfigured RDP server to gain access. After the dust had settled, Sophos discovered some files which had been encrypted by all three groups
At this stage there’s only anecdotal evidence to suggest that multiple attacks are on the rise, but, as Sophos’ Director of Incident Response, Peter Mackenzie, notes: “This is something we’re seeing affecting more and more organizations, and it’s likely due to an increasingly crowded market for threat actors, as well as ransomware-as-a-service (RaaS) becoming more professionalized and lowering the bar to entry.”
Key takeaways for organizations
Multiple attacks not only complicate incident response, but also place additional pressure on victims – whether that’s through more than one ransom demand, or just the sheer technical difficulty of trying to recover from two or more attacks in a short space of time.
In the white paper we provide best practice security guidance, as well as the following eight actionable takeaways to help organizations lower the risk of falling victim to multiple attackers:
Takeaway 1: Update absolutely everything
It sounds simple, but: Update everything. One of our key findings is that cryptominers, and webshells and backdoors deployed by IABs, often come first when a vulnerability has been disclosed, and the latter typically try to operate stealthily – so you might think you’ve avoided an attack, when in fact there’s already malware on your system. That might be compounded (in a subsequent attack) by ransomware. Patching early is the best way to avoid being compromised in the future – but it doesn’t mean you haven’t already been attacked. It’s always worth checking that your organization wasn’t breached prior to patching.
Takeaway 2: Prioritize the worst bugs first
But how can you patch early, and how do you know what to patch? Prioritizing can be a big ask, given how many vulnerabilities are disclosed (18,429 in 2021, more than 50 a day on average, and the greatest number of reported vulnerabilities ever disclosed during a calendar year). So focus on two key elements: 1) critical bugs affecting your specific software stack; and 2) high-profile vulnerabilities that could affect your technology. There are paid services which offer vulnerability intelligence, but there are also free tools which let you set up custom alerts for particular products. Bug Alert is a non-profit service that aims to give early warning of high impact bugs. Monitoring ‘infosec Twitter’ is also recommended, as that’s where many prominent vulnerabilities are discussed when first released. Or you could use CVE Trends, which collates data from several sites to show the most-talked-about vulnerabilities.
Takeaway 3: Mind your configurations
Misconfigurations – and a failure to remediate them after an attack – are a leading cause of multiple exploitations. Cryptominer operators, IABs, and ransomware affiliates always look for exposed RDP and VPN ports, and they’re among the most popular listings on most criminal marketplaces. If you do need remote access and/or management over the internet, put it behind a VPN and/or a zero-trust network access solution that uses MFA as part of its login procedure.
Takeaway 4: Assume other attackers have found your vulnerabilities
Threat actors don’t operate in isolation. IABs might resell or relist their products, and ransomware affiliates may use multiple strains – so one vulnerability or misconfiguration can lead to multiple threat actors seeking to exploit your network.
Takeaway 5: Don’t slow-walk addressing an attack in progress
Being listed on a leak site may attract other, opportunistic threat actors. If you’re unfortunate enough to be hit with a ransomware attack, take immediate action, in conjunction with your security teams and incident response provider(s), to close the initial entry point and assess what data has been leaked, as part of your wider remediation plan.
Takeaway 6: Ransomware plays nicely with ransomware
Many threat actors have traditionally been competitive, to the point of kicking each other off infected systems, and that’s still true today when it comes to cryptominers and some RATs. But ransomware doesn’t seem to follow this trend, and may proceed to encrypt files even if other ransomware groups are on the same network – or operate in a mutually beneficial way, so that one group exfiltrates and the other encrypts.
Takeaway 7: Attackers open new backdoors
Some attackers may introduce further vulnerabilities after gaining access, or create deliberate or unintentional backdoors (including the installation of legitimate software), which a subsequent threat actor can exploit. So while it’s crucial to close off the initial infection vector, it’s also worth considering a) other weaknesses and misconfigurations that could be used to gain access, and b) any new ingress points that may have appeared.
Takeaway 8: Some attackers are worse than others
Not all ransomware strains are equal. Some have capabilities and features that may complicate attempts to respond to and investigate others – another reason to try to avoid becoming a victim of multiple attacks.
Conclusion
In an increasingly crowded and competitive threat environment, the problem of multiple attackers is likely to grow, with more threat actors coming into the mix and exploiting the same targets – either deliberately or unintentionally.
For organizations, this means that rapidly responding to attacks, applying patches, fixing misconfigurations – and checking for backdoors which attackers might have installed prior to any entry points being closed – will become more and more important.
Multiple attackers are bad news for analysts and responders too, complicating incident response, threat intelligence, and security monitoring. In one of the case studies we explore in the report, for example, one ransomware group wiped Windows Event Logs – which not only deleted traces of that group’s activities, but also those of the two ransomware groups which had attacked the network previously. In another case study, one threat actor was likely an affiliate of two separate ransomware groups.
The threat actors themselves –particularly ransomware actors – will at some point have to decide how they feel about cooperation: whether to fully embrace it or become more competitive. Going forward, some groups might deliberately team up, so that one group’s tactics complement another’s. Or we might see ransomware become more like cryptominers – actively searching for, and terminating, rivals on infected hosts. At the moment, however, it’s an uncertain area – one which we hope our report will shed some light on.