Link to Google Translate in phishing email | Kaspersky official blog
Credit to Author: Roman Dedenok| Date: Thu, 24 Nov 2022 12:14:04 +0000
When discussing cybercriminal tricks, we always recommend that you look carefully at the URL when clicking a link in an email. Here’s another red flag — a link to a page translated using Google Translate. In theory, it could be that the sender of the email is inviting you to visit a site in a different language and is trying to be helpful. In practice, however, this technique is most often used to bypass antiphishing mechanisms. If the message forms part of business correspondence, and the site that’s opened after you click on the link wants you to enter your mail credentials, close the browser window and delete the email right away.
Why attackers use Google Translate links
Let’s take a look at a recent example of phishing through a Google Translate link caught by our traps:
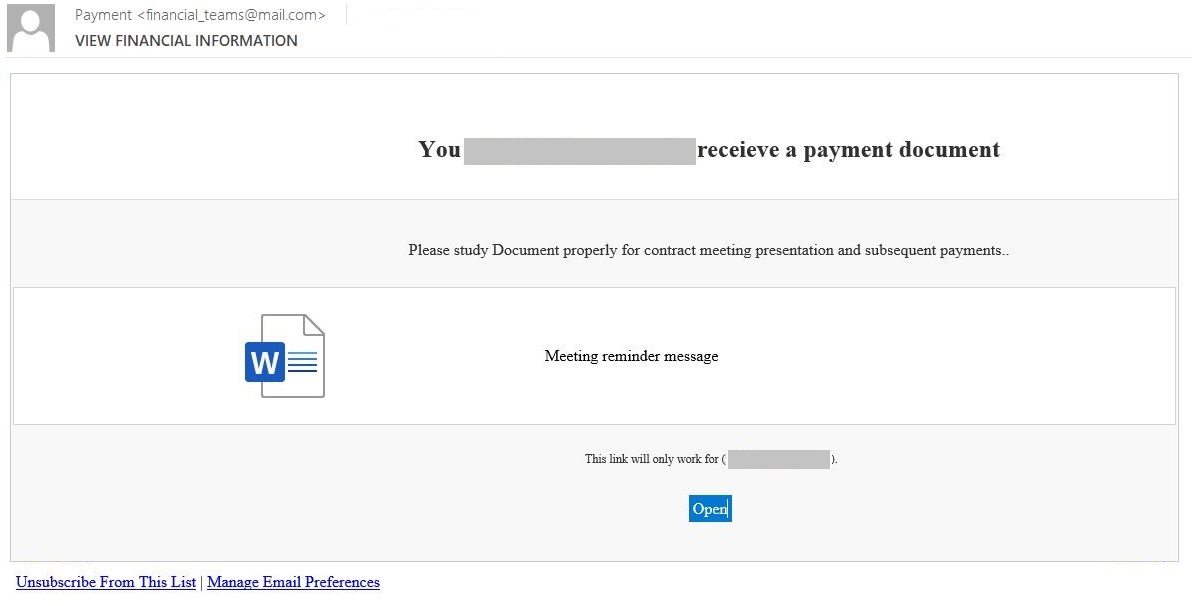
The senders of the email allege that the attachment is some kind of payment document available exclusively to the recipient, which must be studied for a “contract meeting presentation and subsequent payments.” The Open button link points to a site translated by Google Translate. However, this becomes clear only when clicking on it, because in the email it appears like this:
The strange wording is perhaps intentional — an attempt by the attackers to create the impression of not being native English speakers to make the Google Translate link seem more convincing. Or maybe they’ve just never seen a real email with financial documents. Pay attention to the two links below (“Unsubscribe From This List” and “Manage Email Preferences”), as well as the sendgrid.net domain in the link.
These are signs that the message was not sent manually, but through a legitimate mailing service — in this case the SendGrid service, but any other ESP could have been used. Services of this type normally protect their reputation and periodically delete mail campaigns aimed at phishing and block their creators. That’s why attackers run their links through Google Translate — the ESP’s security mechanisms see a legitimate Google domain and don’t consider the site to be suspicious. In other words, it’s an attempt not only to dupe the end-user target, but the filters of the intermediary service as well.
What does a link to a page translated by Google Translate look like?
Google Translate lets you translate entire websites simply by passing it a link and selecting the source and target languages. The result is a link to a page where the original domain is hyphenated, and the URL is supplemented with the domain translate.goog, followed by the name of the original page and keys indicating which languages the translation was made to and from. For example, the URL of the translation of the home page of our English-language blog www.kaspersky.com/blog into Spanish will look like this: www-kaspersky-com.translate.goog/blog/?_x_tr_sl=auto&_x_tr_tl=es&_x_tr_hl=en&_x_tr_pto=wapp.
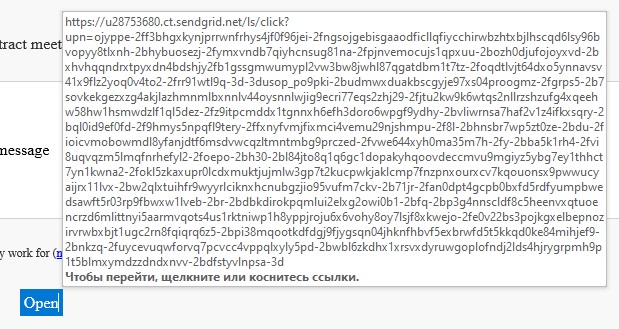
The phishing email we analyzed sought to lure the user here:
The browser address bar, despite the string of garbage characters, clearly shows that the link was translated by Google Translate.
How to stay safe
To keep company employees from falling for cybercriminal tricks, we recommend periodically refreshing their knowledge of phishing tactics (for example, by sending them relevant links to our blog) or, better still, raising their awareness of modern cyberthreats with the aid of specialized learning tools. Incidentally, in the above example, a trained user would never have gotten as far as the phishing page — the chances of a legitimate financial document addressed to a specific recipient being sent through an ESP service are pretty slim at best. A while back, we posted about ESP-based phishing.
To be extra sure, we additionally recommend using solutions with antiphishing technologies both at the corporate mail server level and on all employee devices.
https://blog.kaspersky.com/feed/