2022 Patch Tuesday cycle wraps with 48 CVEs, one advisory
Credit to Author: Angela Gunn| Date: Tue, 13 Dec 2022 18:00:22 +0000
Microsoft on Tuesday released patches for 48 vulnerabilities in seven Microsoft product families. This includes 6 Critical-class issues affecting Microsoft Dynamics, SharePoint, and Windows. The majority of CVEs affect Windows; the operating system accounts for 30 CVEs, including four shared with Azure. Including those four shared CVEs, Azure itself takes five patches. Office takes 13, including patches for both Outlook for Android and Outlook for Mac. Those are followed by two patches for SharePoint and one each for Microsoft Dynamics, .NET, and Windows Subsystem for Linux (shared with Windows).
The release also contains one advisory of more than ordinary significance. For information on ADV220005, “Driver Certificate Deprecation Defense in Depth,” please see our writeup. We will be presenting continuing coverage of this situation as it evolves.
As for the patches, one vulnerability (CVE-2022-44710), an Important-class elevation-of-privilege bug in the DirectX Graphics Kernel that affects only Windows 11 Version 22H2 for ARM64- and x64-based systems, has been publicly disclosed. Another (CVE-2022-44698), a flaw allowing for security feature bypass in Windows’ SmartScreen component, has already been exploited; finder Will Dormann discussed the implications of this bug in a recent Twitter thread.
The remaining 46 issues remain undisclosed and unexploited according to Microsoft.
By the Numbers
- Total Microsoft CVEs: 48
- Total advisories shipping in update: 1
- Publicly disclosed: 1
- Exploitation detected: 1
- Exploitation more likely in latest version: 6
- Exploitation more likely in older versions: 7
- Severity
- Critical: 6
- Important: 41
- Moderate: 1
- Low: 0
- Impact
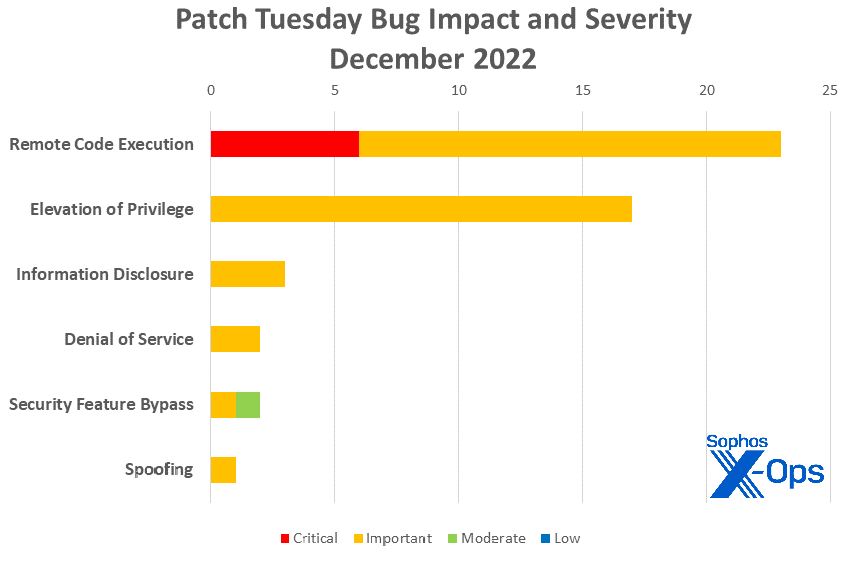
- Remote Code Execution: 23
- Elevation of Privilege: 17
- Information Disclosure: 3
- Denial of Service: 2
- Security Feature Bypass: 2
- Spoofing: 1
Figure 1: Remote-code execution vulnerabilities slightly outnumbered elevation-of-privilege bugs in the final scheduled Patch Tuesday release of 2022
Products:
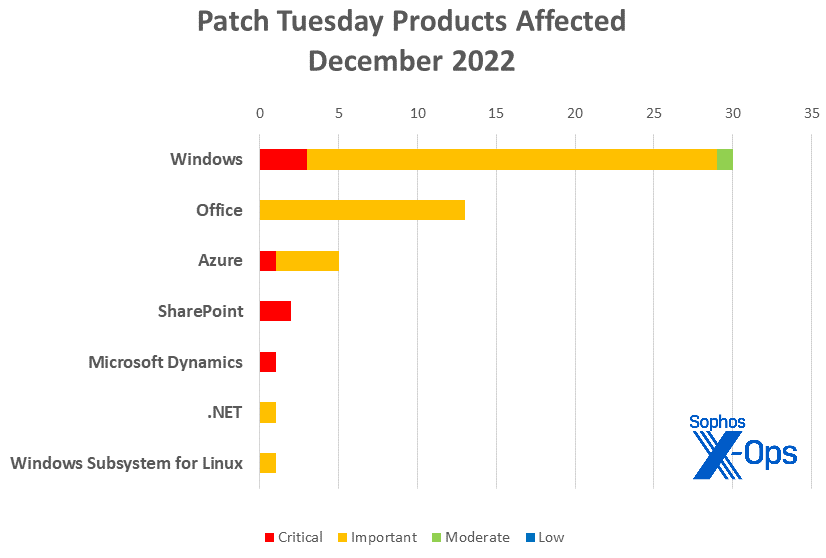
- Microsoft Windows: 30, including four shared with Azure and one shared with Windows Subsystem for Linux
- Microsoft Office: 13
- Azure: 5, including four shared with Windows
- SharePoint: 2
- Microsoft Dynamics: 1
- .NET: 1
- Windows Subsystem for Linux: 1, shared with Windows
Three Edge-related patches issued earlier in the month (CVE-2022-44688, CVE-2022-44708, CVE-2022-41115) are referenced in Microsoft’s release documentation but require no action as part of the release itself.
Figure 2: December’s patches include four shared by Windows and Azure, and one shared by Windows and Windows Subsystem for Linux (shared patched are represented under all applicable families)
Notable Vulnerabilities
Still Not Present: Exchange
System administrators should continue to monitor Microsoft communications for changes and updates regarding the two active Exchange Server vulnerabilities disclosed in early October. Sophos will continue to add protections as those become available.
CVE-2022-44690, CVE-2022-44693: Microsoft SharePoint Server Remote Code Execution Vulnerability
Both SharePoint vulnerabilities this month are Critical-class RCEs, and in both cases an authenticated attacker with Manage List permissions could execute code remotely on a SharePoint Server in the course of a network-based attack. Microsoft takes pains in its release information to note that the cumulative update for SharePoint Server 2013 includes the update for Foundation Server 2013, so customers running SharePoint Server 2013 Service Pack 1 can install the cumulative update or the security update, which is the same update as for Foundation Server 2013.
CVE-2022-41076: PowerShell Remote Code Execution Vulnerability
Another Critical-class RCE, this one requires fairly complex preparation by the attacker on the target environment, but it can be triggered by any authenticated user. In use, this vulnerability allows an authenticated attacker to escape the PowerShell Remoting Session configuration and run unapproved commands on the target system. The patch applies to PowerShell 7.2 and 7.3, all supported versions of Windows, and Windows Server 2022 Datacenter: Azure Edition.
CVE-2022-44666: Windows Contacts Remote Code Execution Vulnerability
Notable mainly because it’s likely the first time most technical folk have thought of Windows Contact as a distinct piece of code (or at all), this bug would require an attacker to convince a user to download and open a maliciously crafted file, leading to a local attack on the user’s computer. Both client and server machines are potentially vulnerable.
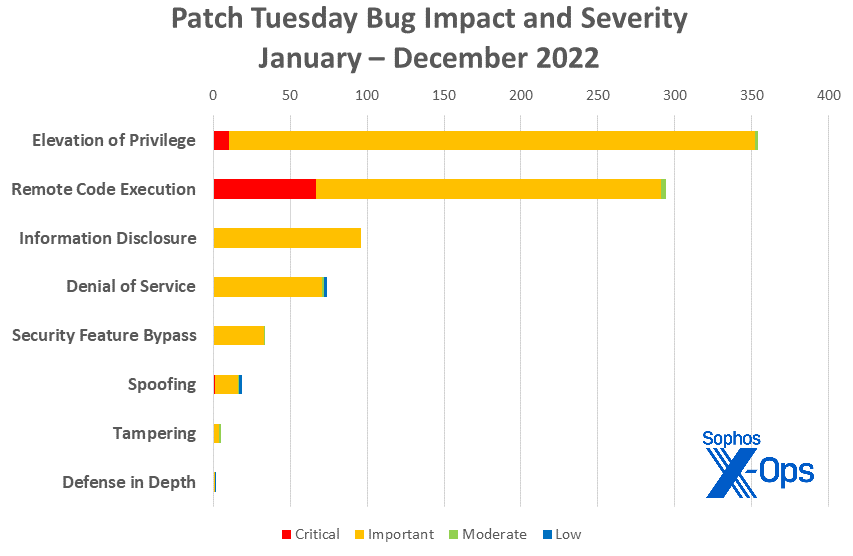
Figure 3: Even with December’s higher percentage of remote code execution vulnerabilities, 2022 was a year for elevation of privilege bugs – at least among bugs of Important or Critical severity
Sophos protections
As you can every month, if you don’t want to wait for your system to pull down the updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your particular system’s architecture and build number.