For the win? Offensive research contests on criminal forums
Credit to Author: Matt Wixey| Date: Tue, 29 Aug 2023 10:00:17 +0000
If you’re a security researcher who wants to share your innovations and insights with the wider community (and gain some peer recognition into the bargain), you’ve got a few options: present at conferences; write papers, blogs, or Twitter threads; submit CVEs; or enter CTFs (capture-the-flag competitions) and vulnerability research contests like Pwn2Own. The legitimate side of the house is awash with opportunities.
But what if you’re a threat actor, whose research is usually more clandestine? In theory, there’s nothing stopping you from doing any of the above – but it could (and almost certainly will) draw unwanted attention and be counter-productive. Better to share it with other threat actors, perhaps – but how, and where?
If there’s one thing criminal marketplaces do well, it’s fulfilling the needs and demands of criminals, and this area is no exception. For several years, prominent Russian-language cybercrime forums like Exploit and XSS have run annual research contests for their members, with monetary prizes put up by sponsors – usually prominent threat actor groups.
As Digital Shadows notes in the article linked above, early contests were simple, involving trivia quizzes, graphic design competitions, or guessing games. We’ll dig into exactly how today’s contests work shortly, but the key point is that they’re very different from those first, basic competitions. Recent contests are more akin to typical Call for Papers (CFPs) for legitimate security conferences – with users invited to submit ‘articles’ on technical topics, complete with source code, videos, and/or screenshots.
And unlike those earlier contests, today’s events are big pulls for threat actors. This is partly because a considerable amount of money is up for grabs – not as much as Pwn2Own or the Tianfu Cup, but not exactly pocket change, either – and also because they’re an opportunity for threat actors to attain recognition and plaudits from their peers.
While the fact that these contests exist is interesting in itself, their entries provide us with some insight into threat actor innovation: what they’re working on, what obstacles they’re seeking to overcome and how, and what their peers deem important.
How contests work
Forums usually run their contests annually, although the last one on Exploit closed in May 2021, and at the time of writing there hasn’t been another. The process is pretty simple: an admin announces the contest, and specifies the closing date, topic area, and rules.
Any user of the forum can submit an entry, typically by posting it in a dedicated thread. At the closing date, admins disqualify any entries which don’t meet the rules (e.g., they’re below a minimum word limit, or have been plagiarized), and the rest are put to a public vote on the forum .
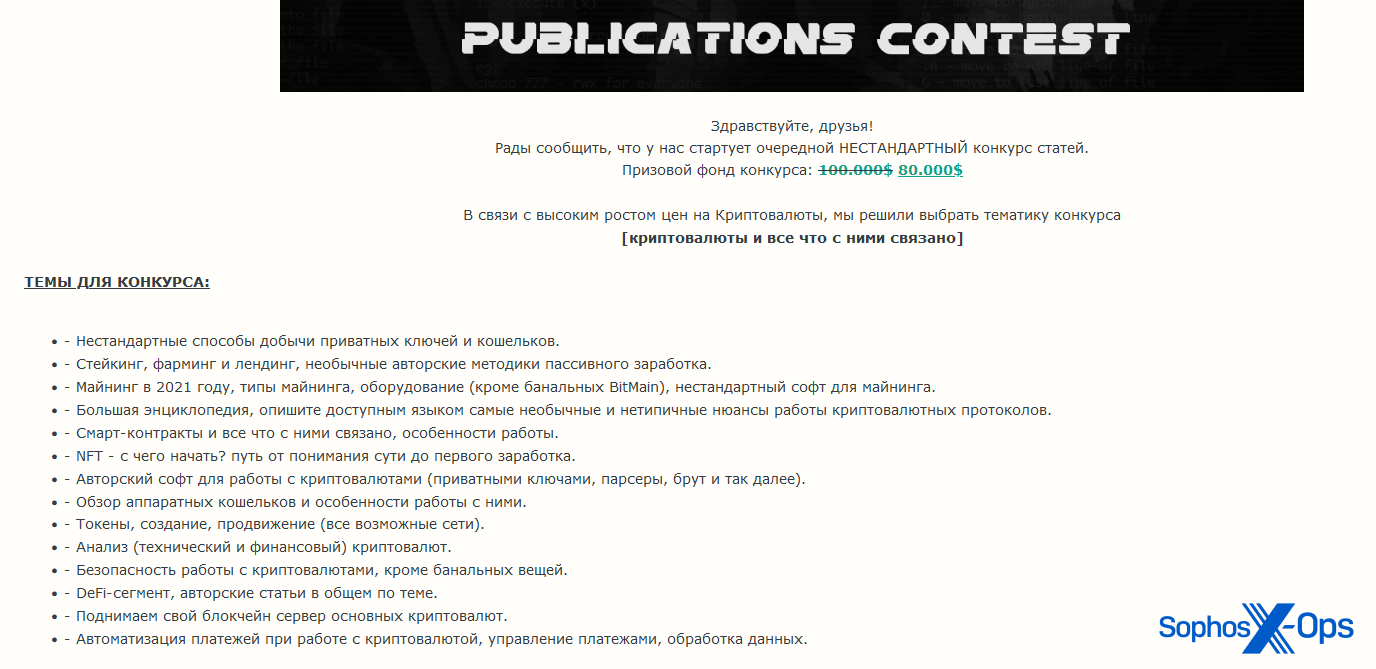
Exploit’s most recent contest at this writing was launched on April 20, 2021, with a total prize fund of $80,000 USD. The contest was themed around cryptocurrencies, with articles requested on attacks, thefts, weaknesses, and vulnerabilities. Specifically, the administrator suggested the following topics:
- Non-standard ways of extracting private keys and wallets
- Staking, farming and landing, unusual author’s methods of passive income
- Mining in 2021, types of mining, equipment (except for the banal BitMain), non-standard mining software
- A large encyclopedia, describe in an accessible language the most unusual and atypical nuances of cryptocurrency protocols
- Smart contracts and everything connected with them, features of work
- NFT – where to start? the path from understanding the essence to the first earnings
- Author’s software for working with cryptocurrencies (private keys, parsers, brute, and so on)
- Overview of hardware wallets and features of working with them
- Tokens, creation, promotion (all possible networks)
- Analysis (technical and financial) of cryptocurrencies
- Security of working with cryptocurrencies, except for banal things
- DeFi-segment, author’s articles in general on the topic
- We raise our blockchain server of the main cryptocurrencies
- Automation of payments when working with cryptocurrency, payment management, data processing
Figure 1: The announcement of the Exploit contest in April 2021, seen in translation in the bullet list above
The contest began on April 21, 2021 and closed to entries a month later, with the winners announced in September.
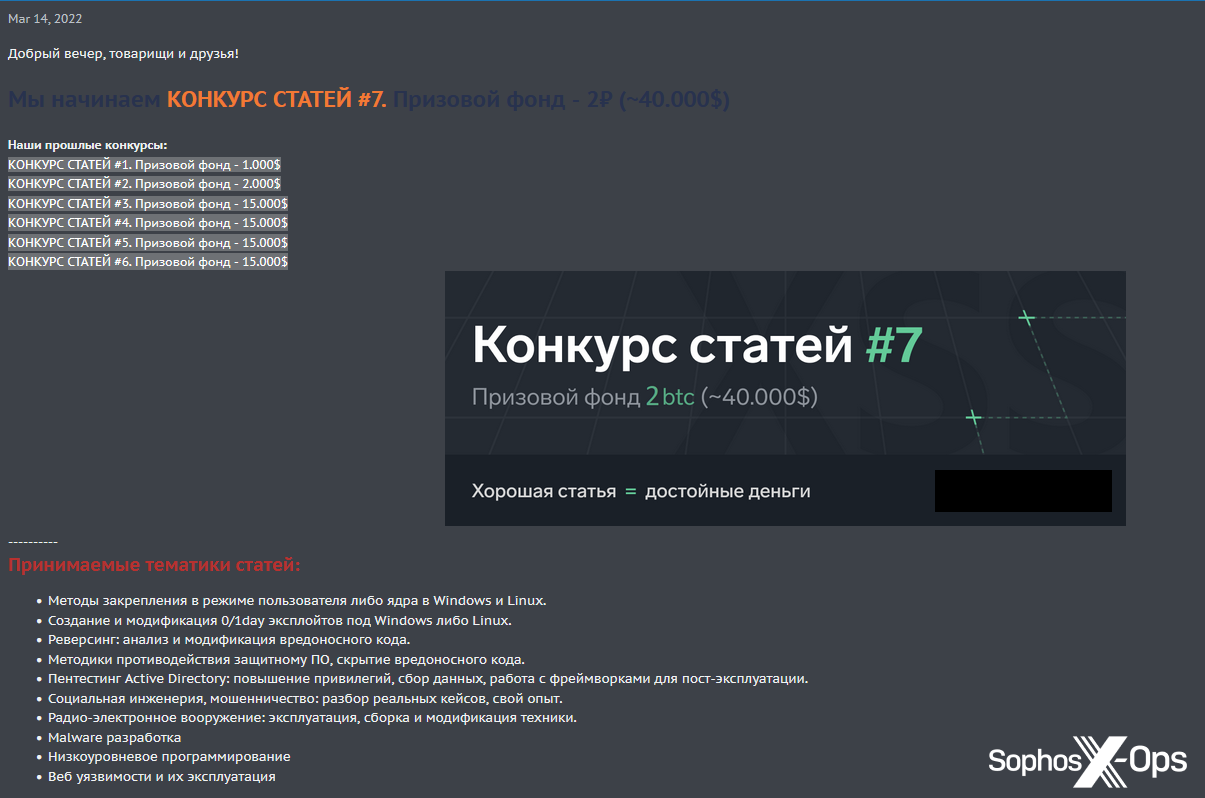
XSS’s latest competition, which ran from March 17 until July 1, 2022 and had a more modest prize fund of $40,000, although this was a significantly increase on the previous year’s pool of $15,000.
That contest was more general, with the following listed as acceptable topics:
- Methods for pinning in user or kernel mode on Windows and Linux
- Creation and modification of 0/1day exploits for Windows or Linux
- Reversing: analysis and modification of malicious code
- Techniques for countering security software, hiding malicious code
- Pentesting Active Directory: privilege escalation, data collection, working with frameworks for post-exploitation
- Social engineering, fraud: analysis of real cases, my own experience
- Radio-electronic weapons: operation, assembly and modification of equipment
- Malware development
- Low level programming
- Web vulnerabilities and their exploitation
Figure 2: XSS launches its latest contest in March 2022, seen in translation in the bullet list above
For both contests, any member of the forum is allowed to participate, regardless of when they registered or how many posts they have made. Entries are either submitted in a specific section of the forum, or in the announcement thread with a specific title.
Rules
Both Exploit and XSS contests stipulate specific rules for entry.
Exploit’s rules
- Entries must not have been published elsewhere, and must belong to the author
- Entries must be “meaningful and voluminous, touch on all aspects of the proposed topic, [and] describe the mechanisms, practices and tool used”
- Entries should contain technical details, in the form of algorithms, code, and/or diagrams
- Articles should be at least 5000 characters (excluding spaces)
XSS’s rules
- Maximum of three entries per participant
- Entries should be the author’s work (“copy-paste = expulsion from the contest, in disgrace”)
- Entries should be exclusively published on the forum
- Articles should be at least 7000 characters
- Entries should have a practical application, and should not be “boring theory, in its pure form, no one is interested in theory”
- Entries should use proper formatting, spelling, and punctuation
The XSS rules also include some guidance on the perfect article: “theory + practice + live real examples + your opinion/experience + thematic analysis of the material + screenshots + video demonstration.”
Many of these rules will be familiar to anyone who’s submitted to a conference CFP, a sign that criminal forums are seeking to legitimize and professionalize their contests.
Sponsors
For several years, prominent members of the criminal community have sponsored contests on Exploit and XSS, with past sponsors including All World Cards, a well-known carding group, and LockBit.
The sponsor of the most recent Exploit contest was a user called CryptoManiac, who contributed $15,000, but the forum administrators themselves stumped up most of the cash, writing: “The forum allocates $100,000, sponsors, if they wish, can increase the prize fund, for this they will be given special thanks in this topic.”
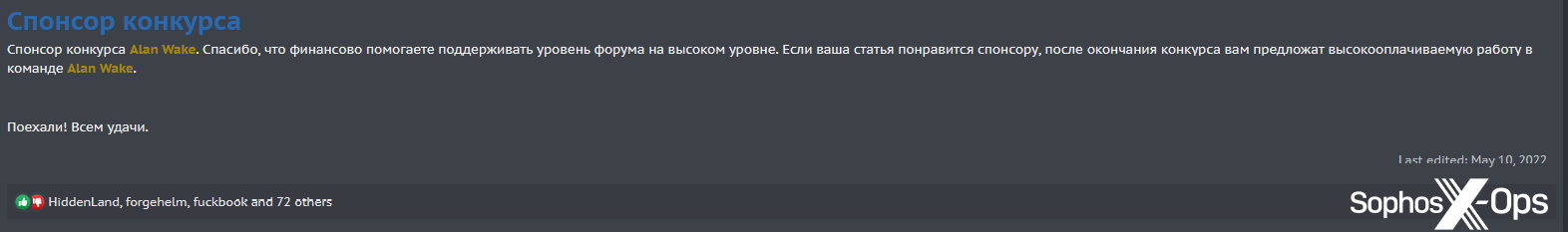
The sponsor of XSS’s 2022 contest was a threat actor called Alan Wake (after the video game of the same name), who has previously been accused by LockBit of being the leader of the Conti and Black Basta ransomware groups.
Figure 3: The XSS admin thanks the contest’s sponsor, Alan Wake
As if the prizes weren’t incentive enough, the admin advises that: “If your sponsor likes your article, after the end of the competition you will be offered a highly paid job in the Alan Wake team.”
Voting
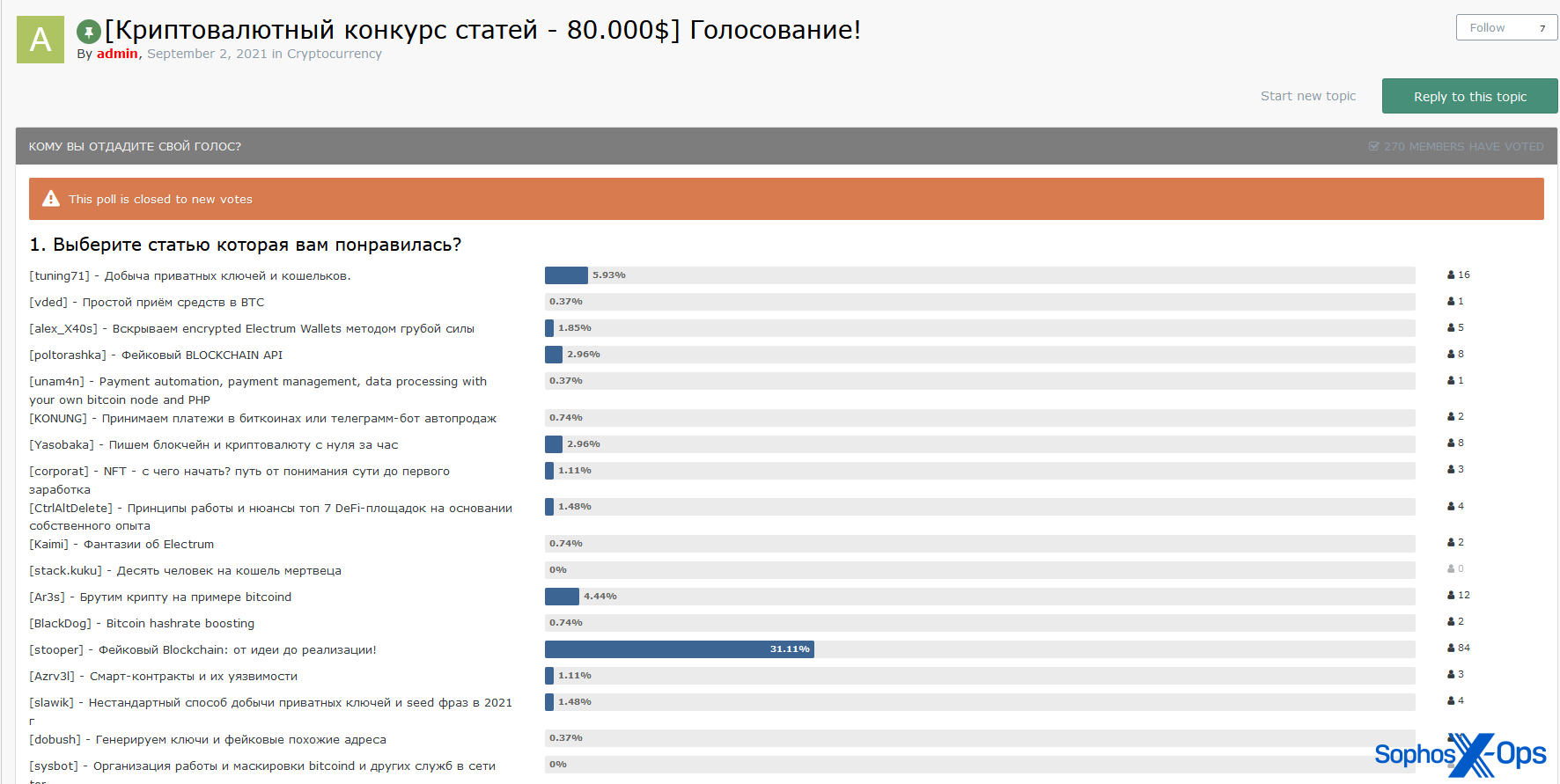
Both Exploit and XSS claim to run a democratic process for selecting contest winners. Entries which fulfil the requirements (those which don’t are disqualified) are put to a vote, with all forum users invited to take part.
However, both processes seem to lack transparency, and it’s unclear how much weight individual votes carry. The Exploit admin writes that “since there are often cases of fraud and vote cheating…the final decision will be made by the forum team and me in particular, we will definitely take into account the results of the general vote.”
Over on XSS, the admin notes that “suspicious and stuffed votes” will be removed. Moreover, votes by the admin and the sponsor(s) account for an “increased percentage.”
Both contests make the poll results visible to all users.
Figure 4: The Exploit contest poll
Entries
Both forums received a similar amount of entries in their most recent contests: 35 on Exploit (with 3 individual prizes, plus 5 honorable mentions), and 38 – excluding 10 disqualified entries – on XSS (7 individual prizes).
While the Exploit contest was themed specifically around cryptocurrencies, XSS’s was more diverse, and topics ranged from social engineering and attack vectors to evasion and scam proposals. Cobalt Strike was a popular topic, with three of the seven prize-winning entries focusing on the legitimate pentesting tool often abused by threat actors. Other popular topics included tutorials about attack vectors and finding vulnerabilities (eight entries); crypto-related scams (six entries); and evasion (five entries).
Let’s examine the top-placed entries.
Exploit
First place: Fake blockchain: From idea to implementation!
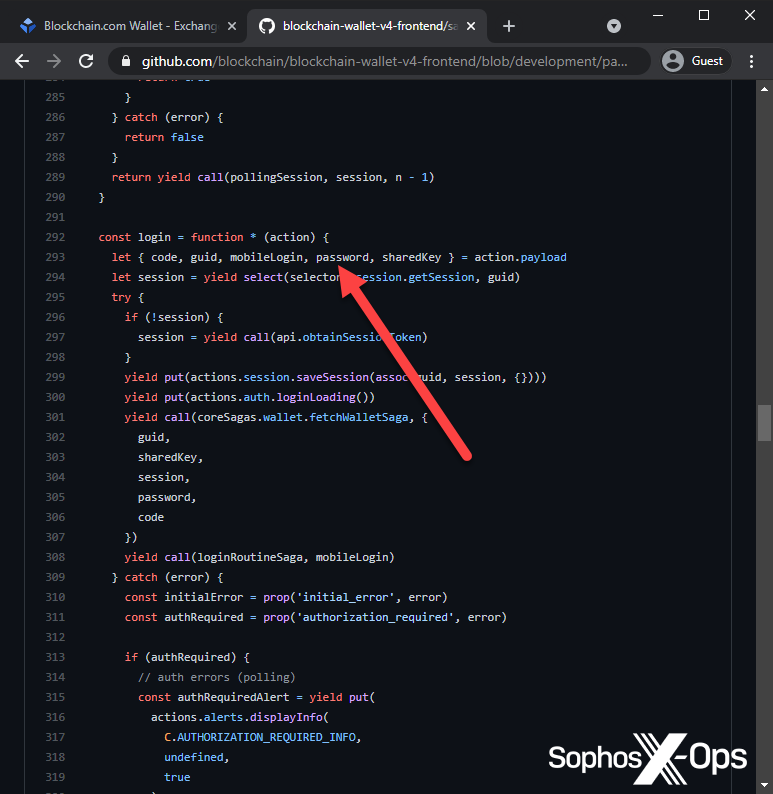
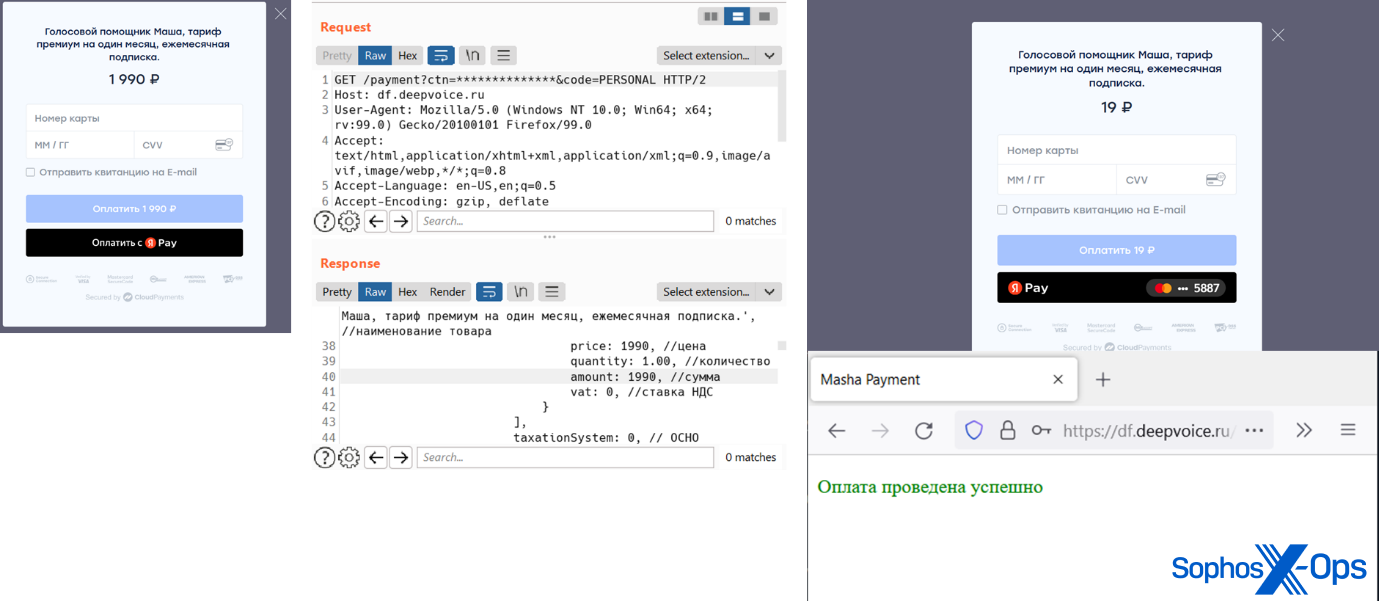
The winning entry in Exploit’s most recent contest was relatively simplistic – creating a cloned version of blockchain.com (using a GitHub repository) to harvest credentials. The author had to overcome several technical difficulties, such as configuring the cloned site’s authorization routine, and setting up a reverse proxy to bypass the Cross-Origin Resource Sharing (CORS) mechanism, but a cloned site like this would typically be used like any other phishing or credential-harvesting site. Because the target is a cryptocurrency exchange/wallet site, this could potentially be a lucrative attack.
Figure 5: A screenshot from the winning entry in the Exploit contest
Second place: ICO: Wild hunt Cost: $0, profit: $742
In second place, another relatively basic attack, this time targeting initial coin offerings (ICOs) – a way to raise funds for launching a new cryptocurrency. The author provides a tutorial on looking for suitable ICOs to target (small, but with about 20,000 views a month), and then gives instructions on using well-known tools like sqlmap to find and exploit SQL injection vulnerabilities, in order to extract user data and tokens from databases.
Third place: Extraction of private keys and wallets
The third-placed entry in the Exploit contest was a tutorial on creating a phishing site and processing sensitive cryptocurrency-related data (secret words, wallets, etc) via Telegram.
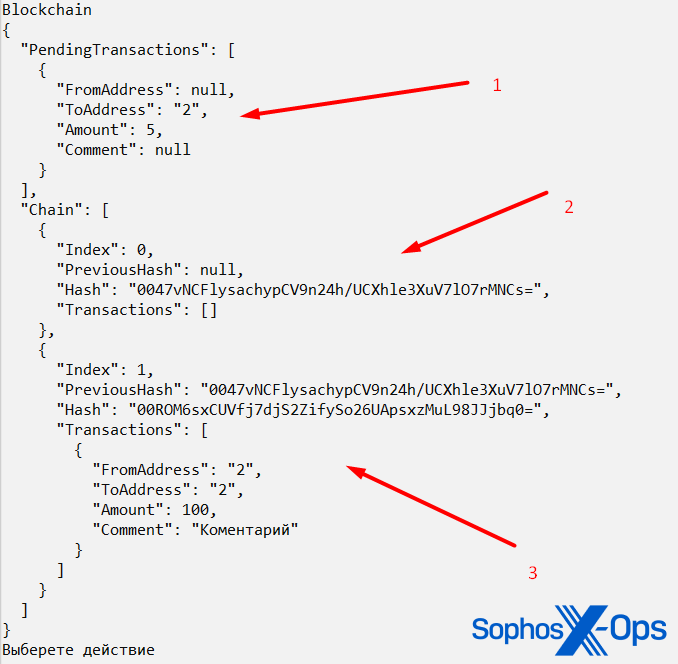
Honorable mention: We write blockchain and cryptocurrency from scratch in an hour
A tutorial on creating a cryptocurrency from scratch. It is worth noting that there have been free and publicly available tutorials on how to do this for several years.
Figure 6: A screenshot from the ‘We write blockchain and cryptocurrency from scratch in an hour’ article
Honorable mention: Fake blockchain API
A slightly more complex entry, this article advocates creating a malicious library to be used by a “lazy developer” when making cryptocurrency applications. The entry includes advice on creating the library and tips to make it attractive to developers (free, simple, anonymous, useful functionality, and so on); how to write and hide the malicious components of the library (i.e., how to intercept, encrypt, and covertly process sensitive data such as private keys); and how to process the resulting stolen data.
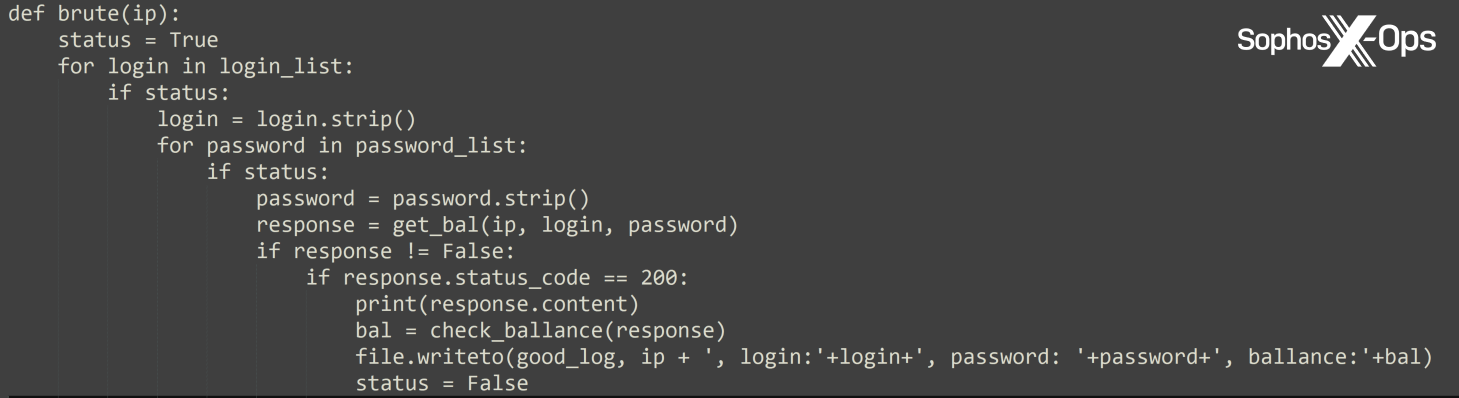
Honorable mention: Bruting crypt for example Bitcoin
Another simple tutorial, this entry comprised a guide on mass-scanning for Bitcoin daemons which accept incoming connections, and then bruteforcing them to access sensitive data.
Figure 7: An extract from the code supplied in the ‘Bruting crypt for example Bitcoin’ article
Honorable mention: We squeeze the logs to dryness
In this entry, the author discusses parsing “logs” (presumably logs from infostealers such as Redline or Raccoon Stealer, which are collections of stolen cookies, browsing history, and tokens) in order to find cryptocurrency-specific information.
Figure 8: A screenshot from the ‘We squeeze the logs to dryness’ article
Honorable mention: Bitcoin price peak: When and where to exit the crypto?
In the final honorable mention, the author writes a 50-page article (by far the longest entry) on how and when to sell Bitcoin. It dives into the psychology of investing, cryptocurrency economics, and market cycles, and does not include any information specific to cybercrime, although the content is likely to be of interest to threat actors who hold and/or trade in Bitcoin as part of their activities. It also includes tips on how to sell Bitcoin – for instance, staggering sales, investing in stablecoins or tokenized shares, and so on.
XSS
First place: 20 years of payment acceptance problems
The winning entry in the XSS contest gives an overview of vulnerabilities in electronic payment systems. It discusses the architecture of some of these systems, and typical vulnerabilities within them – including lack of signature verification; length extension attacks; intercepting and changing price and currency information (a technique that has been around for many years); business logic flaws; rounding, overflow, and negative number errors; and race conditions. It also provides some case studies of vulnerabilities in electronic payment systems that have been exploited in the past.
Figure 9: A screenshot from the winning entry in the XSS contest. This particular screenshot was provided by the author as evidence that they could intercept and change the payment amount to a paid Telegram bot
Two particularly interesting things about this entry: 1) it gives readers ‘homework,’ encouraging them to try various attacks for themselves; and 2) it discusses a specific vulnerability in the XSS forum itself, whereby a race condition in the Bitcoin transfer system allowed users to effectively generate cryptocurrency out of thin air.
Second place: Remote Potato Zero and Cobalt Strike
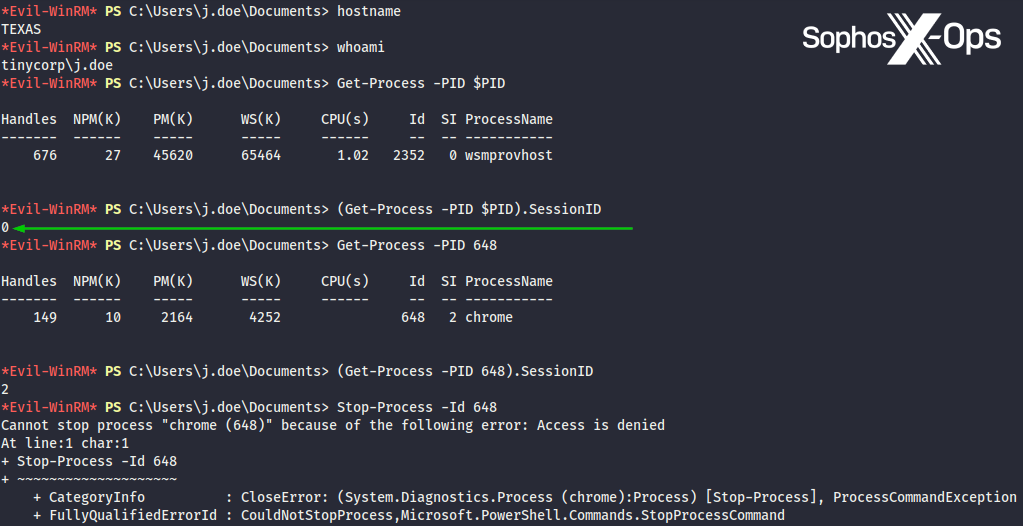
In second place, a much more technical article, purportedly based on the author’s experiences attacking an Active Directory environment where members of the Domain Users group had the ability to remotely connect to domain controllers via RDP. The author sought to escalate privileges, and in their article they argue that Remote Potato, in conjunction with Cobalt Strike, is an effective means to do this in some environments.
The author discusses how to hide Remote Potato from Windows Defender, how to use it in different scenarios, and the use of other tools, including Ngrok and Socat.
Figure 10: A screenshot from the ‘Remote Potato Zero and Cobalt Strike’ article
Third place: Disable Windows Defender (plus UAC bypass and elevate to SYSTEM)
The third-placed entry includes a tutorial on manipulating privilege tokens in order to disable Windows Defender. Specifically, the author outlines an attack flow involving obtaining administrative privileges with a UAC bypass, escalating to SYSTEM by stealing a token and starting a process, and then disabling Defender.
Fourth place: Hide your Cobalt Strike like a pro!
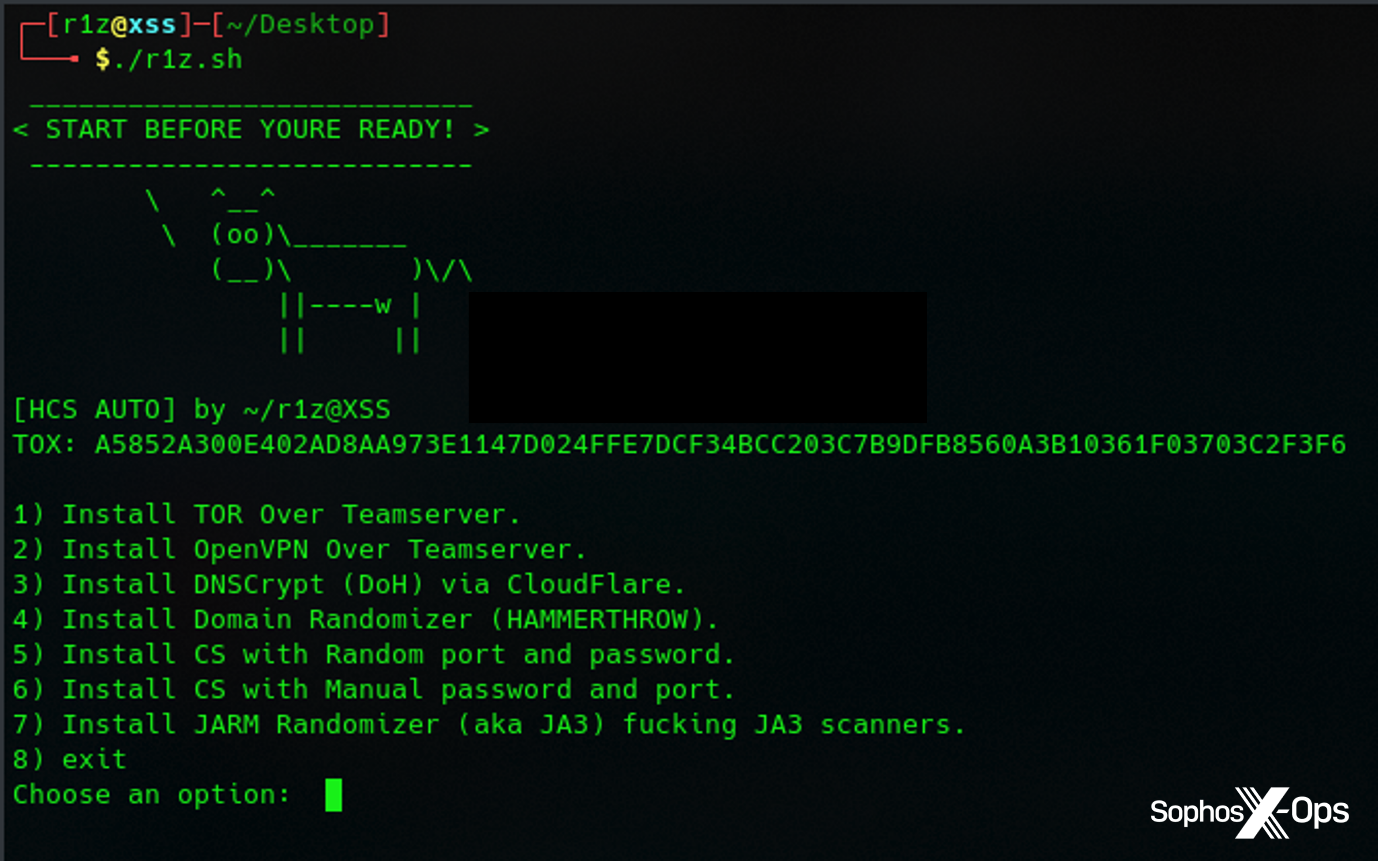
In fourth place, this article is a deep technical dive into various ways to hide Cobalt Strike from detection, and is one of several in a series. The methods advocated by the author include using Tor and OpenVPN for Cobalt Strike’s TeamServer , DNSCrypt, domain randomizers, and a JARM randomizer. The author also provides a step-by-step guide on modifying Cobalt Strike’s source code and obfuscating beacons.
Figure 11: A screenshot from the ‘Hide your Cobalt Strike like a pro!’ article
Fifth place: Cobalt Strike A-Z
In yet another Cobalt Strike-related article, but not quite as wide-ranging as the title would suggest, an entrant discusses using DLL hijacking in conjunction with Cobalt Strike.
Sixth place: Scam crypto big
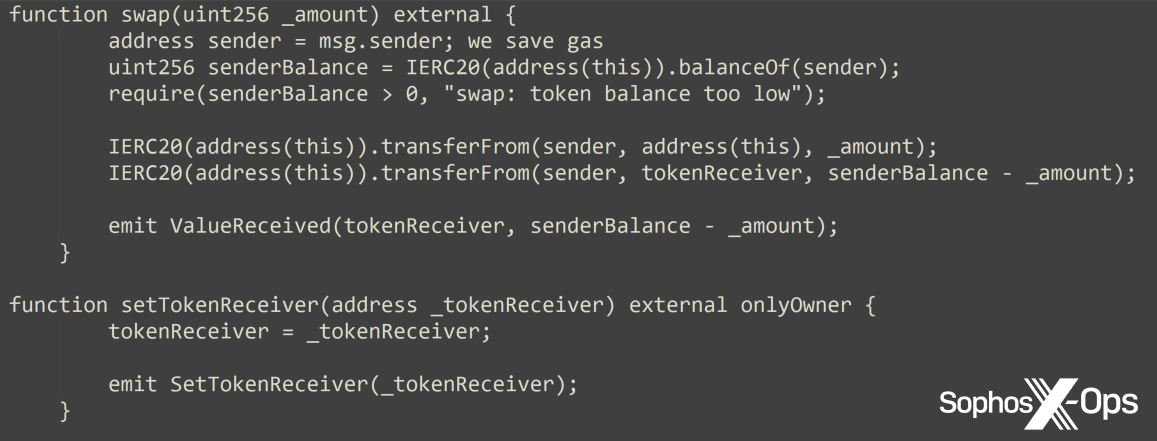
The sixth-placed entry talks about abusing the standards of smart contracts, and specifically how to create smart contracts to secretly withdraw a victim’s tokens. It also covers various methods to distribute malicious contracts, including AirDrop, Discord, email, and malvertising.
Figure 12: Code from the ‘Scam crypto big’ article
Seventh place: NoSQL injection
Finally, in the last placed entry, the author provides a primer on NoSQL injection, the differences between it and SQL injection, and a tutorial on some of the causes.
Other noteworthy entries
Exploit
We make a hardware cryptocurrency wallet with our own hands
This entry was particularly noteworthy as it was the only one, on either forum, which specifically covered hardware. The author provides a guide on creating a hardware cryptocurrency wallet, from theory to practice, complete with CAD drawings and photographs. As with the guide on exiting Bitcoin, this article doesn’t have much relevance to cybercrime, and is more aimed at helping users to protect their funds rather than having to trust off-the-shelf wallets.
In line with this aim, the author also provides a lot of OPSEC advice relating to hardware wallets, and information relating to various known attacks against them, including malicious firmware updates; brute-forcing PIN codes; fault injection; supply chain attacks; and surveillance.
Figure 13: A photograph included in the ‘We make a hardware cryptocurrency wallet with our own hands’ article
Smart contract vulnerabilities
A primer on smart contracts and the Ethereum Virtual Machine (EVM), and a guide on how to create a basic contract. The author discusses various vulnerabilities, including access control, front-running, time manipulation, arithmetic issues, and re-entrancy, and then moves on to writing exploits to leverage them.
Figure 14: A screenshot from the ‘Smart contract vulnerabilities’ article
XSS
Elegantly breed daddies on lavender
In this rather cryptically titled entry, the author provides instructions on socially engineering and scamming customers of webcam models, specifically those users who pay to watch videos of performers. The article covers some details on socially engineering victims and how to build rapport with them, before moving on to obtaining and illicitly selling videos.
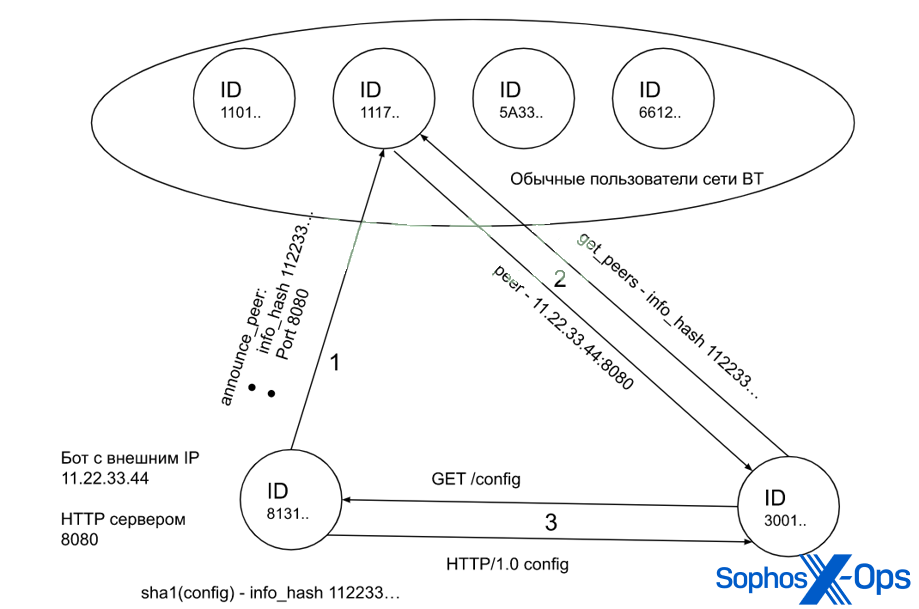
BitTorrent botnet – from design to implementation
A relatively innovative entry, this article describes a problem faced by botnet operators – that control servers are also shut down – and proposes a solution: the distributed hash table (DHT) feature in BitTorrent.
Figure 15: A diagram included in the ‘BitTorrent botnet – from design to implementation’ article
Conclusion
The fact that users of criminal forums are designing, running, and participating in research contests suggests that they seek to foster innovation, especially with regards to new methods of attack and evasion. The sponsorship of these contests by prominent threat actors is further evidence that this is a goal shared among broad sections of the criminal community. It’s worth noting that, in at least one case, past contests have served as a sort of recruitment tool for prominent threat actor groups.
In the contests themselves, we noted an increased interest in Web3-related topics, particularly cryptocurrencies, smart contracts, and NFTs – to the extent that Exploit’s most recent contest was specifically themed around this subject. However, even in the latest XSS contest – which gave entrants a much wider scope – there were a still significant number of related entries.
More generally, there appears to be a reasonable amount of innovation when it comes to topics like evasion and privilege escalation, especially in the context of enhancing or augmenting pre-existing tools like Cobalt Strike.
However, on the whole, there was less innovation than we expected. Even highly placed articles often contained little novel material, and were sometimes simply basic tutorials or guides containing information that is already public . Certainly, in our opinion, there was less original research compared to many prominent security industry contests and conferences.
Winning or highly placed entries tended to be either relatively simplistic, with a broad appeal, or were focused on techniques which could be put to practical use, even if those techniques were not new. The fact that these entries were voted for by the authors’ peers may suggest that this is reflective of the wider community’s preferences and priorities.
Of course, it may be that threat actors are just not that keen to share cutting-edge tools and techniques with each other publicly, and instead keep their best research to themselves – perhaps reasoning that they could realize more profit by using them in real-world attacks, rather than by entering contests.
Competitions on criminal forums are a longstanding, albeit not widely known, feature, and are likely to continue in one form or another. But, going by the most recent entries, they are not likely to become a hotbed of disruption and innovation in the near future.