Context-sensitive defenses in Sophos Endpoint
Credit to Author: Tom Walsh| Date: Tue, 26 Sep 2023 14:03:57 +0000
Sophos Endpoint leverages an extensive range of sophisticated technologies to protect users and devices. This includes threat exposure reduction to block as many threats as possible at the front door, powerful deep learning anti-malware protection, and the most comprehensive anti-ransomware and anti-exploit capabilities in the industry.
A new category of protection, pioneered by Sophos, is what we refer to as context-sensitive defenses, where Sophos Endpoint automatically adapts to the context of an attack by stepping up the level of protection. Read on for more details about two of its key components.
Adaptive Attack Protection
Central to context-sensitive defenses is automatically applying more aggressive protection when a device is under attack. Adaptive Attack Protection dynamically enables heightened defenses on an endpoint when a “hands-on-keyboard” attack is detected.
In this elevated “mode” of protection, actions that are usually benign but commonly abused by attackers are blocked outright. This buys time for admins to eject the attacker from their environment and restore devices to clean health.
Adaptive Attack Protection is powered by SophosLabs’ knowledge of attackers’ latest techniques to gain footholds and progress toward their objectives. Our global team of threat researchers constantly adapts the protection to reflect the evolving threat landscape.
This advanced protection is available to all Sophos Endpoint customers and is enabled by default. For more details, please take a look at this article.
Critical Attack Warning
While Adaptive Attack Protection is focused on detecting and disrupting attacks on individual devices, Sophos’ new Critical Attack Warnings notify customers of an active estate-wide attack.
It detects high-impact indicators of an advanced attack in progress across multiple endpoints or servers in an environment. Again, this is powered by knowledge from Sophos X-Ops of the latest attacks and the specific patterns seen in the lead-up to security incidents.
Critical Attack Warnings are sent to customer administrators by email and mobile push notification (using Intercept X for Mobile). Customers are directed to view more details and respond to the warning in the Sophos Central admin console, with a dashboard summary and a detailed report outlining the devices involved in the attack, and specific threats encountered.
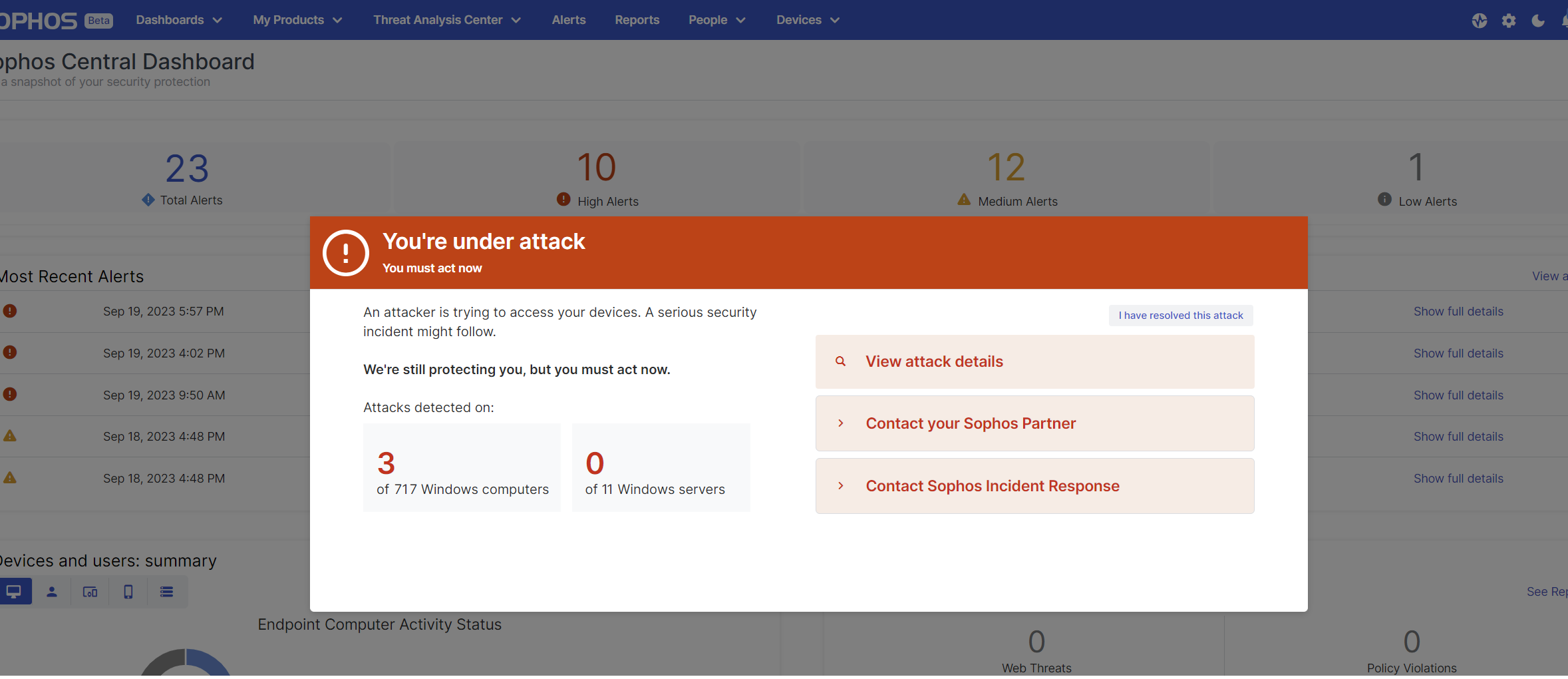
At this point, the key message is this: Sophos is continuing to protect you, but you must act now. Without urgent intervention, the attacker will continue their attempts and find a way to compromise your environment to achieve their malicious objectives, whether that is deploying ransomware or performing data exfiltration.
The most critical next step is to take immediate action to investigate and remove the threat. Customers can respond by seeking assistance from their Sophos partner, engaging the Sophos Incident Response team, or through their internal security team using tools such as Sophos XDR to help respond to the threat.
Critical Attack Warning is a new, innovative capability of Sophos Endpoint, available to all customers running Sophos Intercept X Advanced or Sophos XDR.
Ongoing innovation
We are relentless in our efforts to keep customers ahead of adversaries, and have plans to extend context-sensitive defenses to cater to additional scenarios and further elevate protection.
To learn more about Sophos Endpoint and how it can help your organization better defend against today’s advanced attacks, speak with a Sophos adviser or your Sophos partner today.