NIST CSF (Cybersecurity Framework) 2.0 is just around the corner
Credit to Author: Doug Aamoth| Date: Wed, 04 Oct 2023 12:18:22 +0000
The US National Institute of Standards and Technology (NIST) has released a draft of the Cybersecurity Framework 2.0 for public comment before its 2024 release.
What’s changing? The scope of the framework has been expanded for use by all sectors and is not limited to critical infrastructure organizations anymore.
The 2.0 draft addresses modern-day threats by bringing increased focus to issues such as supply chain security and elevating the importance of corporate governance as a new function in the framework.
Expanded focus from US critical infrastructure to global organizations
First issued by NIST in 2014, the “Framework for Improving Critical Infrastructure Cybersecurity (CSF)” focused on securing the United States’ critical infrastructure. However, it proved helpful to organizations of all sizes, sectors, and stages of business.
The Cybersecurity Framework 2.0 thus has removed the focus on critical infrastructure and changed the title to the commonly known term “Cybersecurity Framework (CSF).” The change reflects the framework’s relevance globally, embracing organizations worldwide.
Why is NIST 2.0 important for those in the know?
The NIST Cybersecurity Framework is a powerful tool for businesses and organizations looking to improve their information security and better manage their cybersecurity risks.
By adopting a uniform approach of established standards and industry best practices, businesses can leverage the NIST CSF as proof that their networks and systems are protected from cyber threats.
Adhering to the NIST CSF can lead to easy compliance with other security standards and frameworks, such as the PCI DSS and the Sarbanes-Oxley Act (SOX). Implementing the security rules listed under NIST 800-53 aligns an organization directly with the Federal Information Security Modernization Act (FISMA) and Federal Information Processing Standard Publication 200 (FIPS 200).
What’s new in 2.0?
The CSF 2.0 draft includes many significant changes to bolster defenses against modern, advanced cyber threats. The following are the most notable changes:
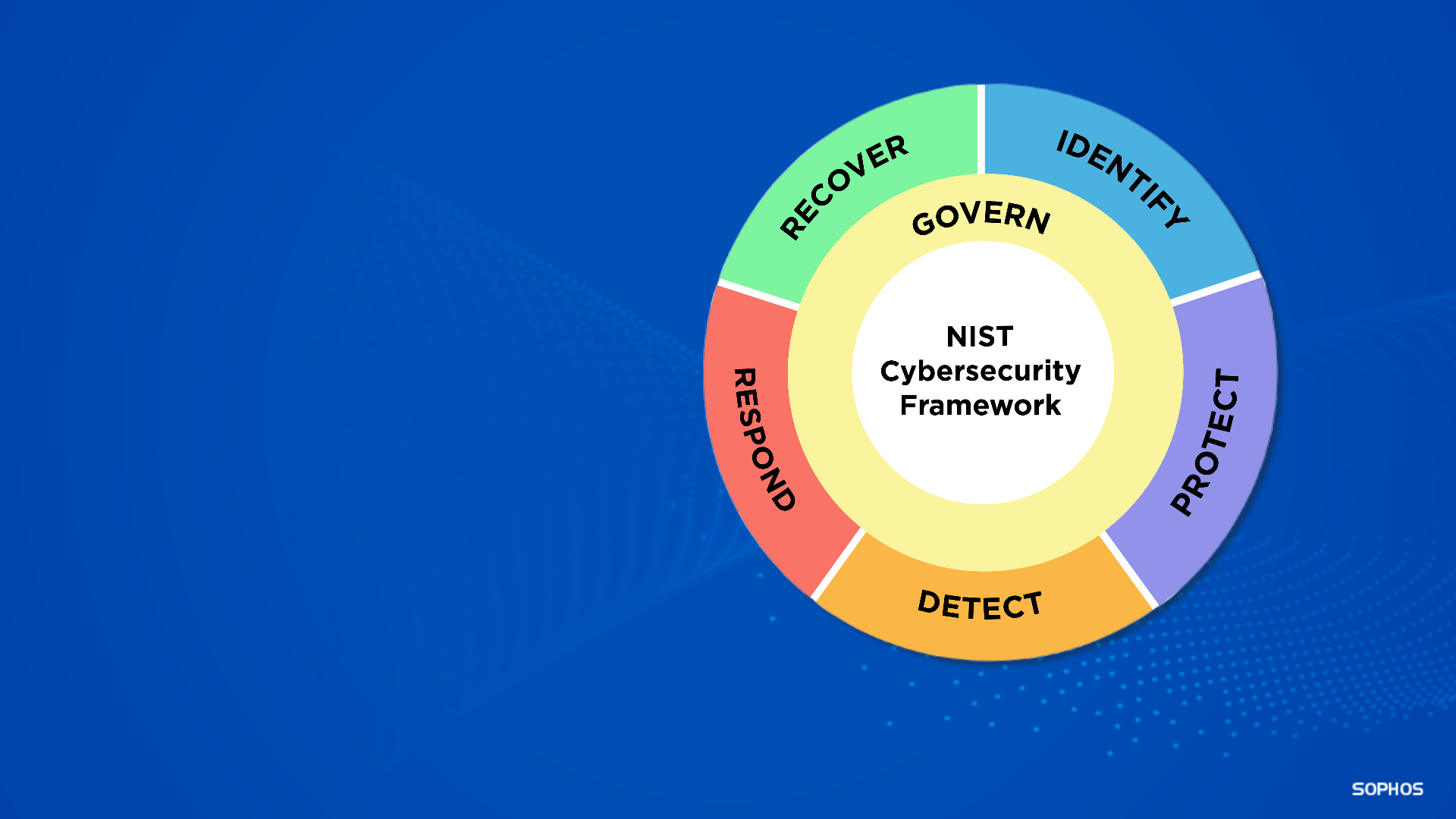
To emphasize cybersecurity governance, a sixth function, Govern, has been added in the 2.0 draft. Govern joins the existing core five functions of the NIST CSF: Identify, Protect, Detect, Respond, and Recover. With this new function, the focus is on each organization’s people, processes, and technology needed to make and execute cybersecurity decisions. While the previous CSF version specified what needed to be done, it lacked focus on the people overseeing those tasks and the policies and procedures governing those controls.
The Govern function introduces a new category for supply chain risk management and secure software development. This category breaks into 10 subcategories and enables organizations to effectively identify, establish, manage, and monitor supply chain risk management processes.
The 2.0 draft updates the resources and Informative References in the older CSF versions. This includes references to the NIST Privacy Framework, NICE Workforce Framework for Cybersecurity (SP 800-181), Secure Software Development Framework (SP 800- 218), Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations (SP 800-161r1), Performance Measurement Guide for Information Security (SP 800-55), Integrating Cybersecurity and Enterprise Risk Management (NIST IR 8286) series, and the Artificial Intelligence Risk Management Framework (AI 100-1).
NIST has launched the CSF 2.0 Reference Tool, which offers human- and machine-readable versions of the Cybersecurity Framework 2.0 and allows users to view and export portions of the draft’s functions, categories, subcategories, and implementation examples using key search terms. In its finalized form, the tool will include Informative References, which will help show the relationship between the CSF and other cybersecurity frameworks, standards, guidelines, and resources.
For easier adoption of the CSF, NIST provides increased guidance on CSF implementation using Implementation Examples, which offer real-world use cases and actional guidance for each function’s subcategories, helping organizations effectively implement the framework. Similarly, Framework Profiles guidance has been considerably expanded to offer advice on how and for which purpose one could use the Profiles, helping organizations to tailor the CSF to their unique organizational contexts.
Timeline for the CSF 2.0 draft completion
NIST hosted the third and final workshop on CSF 2.0 on September 19 and 20, 2023. While it does not intend to release another draft of the CSF 2.0 for comment, public comments and feedback on the Draft of the NIST Cybersecurity Framework 2.0 and related implementation examples are accepted via cyberframework@nist.gov until November 4, 2023.
Conclusion
Sophos’s midyear Active Adversary Report revealed the changing landscape of sophisticated cyber techniques like credential compromise, vulnerability exploits, AD server compromise, unauthorized RDP access, and more. The shift in the threat landscape is rapid, and organizations must adopt frameworks like the CSF to navigate the cyber-threat labyrinth.
At a time when the threat landscape is evolving, a makeover of the world’s leading cybersecurity guidance is inevitable. Built in close collaboration with the community, CSF 2.0 is expected to ensure that more organizations can manage and improve their cybersecurity programs to defend against advanced threats.
Sophos can help organizations in their efforts to align with the NIST CSF and other cybersecurity frameworks. We offer a prevention-first approach that reduces breaches, adapts defenses in response to attacks, and improves detection and response. Enabled by our powerful XDR platform, Sophos offers cybersecurity as a service with Sophos MDR, delivering 24/7 threat detection and response, expert-led threat hunting, and full-scale incident response – all available to be customized to an organization’s specific needs.