ALPHV ransomware gang returns, sorta
The ALPHV ransomware gang, arguably the second most dangerous “big game” ransomware operator, appears to be back in business after its infrastructure went down for five days. But all does not appear to be going well for group.
ALPHV’s dark web leak site may be back but it is only showing a single victim with no sign of any of the hundreds of others it normally lists. The solitary listing on the site is dated December 13, which is after the site was restored.
Many of the group’s negotiation links are reportedly not working either, meaning that victims looking to pay off the gang are stuck in limbo, and its likely that neither the ALPHV group, nor the affiliates who use its ransomware to carry out attacks, are being paid.
When the gang’s infrastructure went down a week ago, many suspected the hand of law enforcement, despite no official word on the subject. According to VX Underground, APLHV’s own explanation is that it suffered a hardware failure. If the group really has lost access to the data its business relies on, then it’s now getting a first hand look at what its victims go through when they’re attacked and their data is encrypted.
ALPHV wouldn’t be the first ransomware gang to suffer problems behind the scenes. Earlier this year, Analyst1 reported that LockBit, the 800-lb gorilla in the ransomware space “cannot consistently publish stolen data … due to limitations in its backend infrastructure and available bandwidth.”
However, while it’s perfectly plausible that ALPHV is suffering hardware woes, law enforcement action can’t be ruled out. ALPHV would likely lose affiliates if it admitted to a brush with the law, so the ransomware gang is likely going to attribute the outage to something benign—whether that is true or not. Equally, the silence from the FBI could mean everything and nothing. In January, the agency took down one of ALPHV’s contemporaries, Hive, and revealed it had penetrated the group’s infrastructure six months prior:
Since late July 2022, the FBI has penetrated Hive’s computer networks, captured its decryption keys, and offered them to victims worldwide, preventing victims from having to pay $130 million in ransom demanded. Since infiltrating Hive’s network in July 2022, the FBI has provided over 300 decryption keys to Hive victims who were under attack. In addition, the FBI distributed over 1,000 additional decryption keys to previous Hive victims.
There were infiltration rumors about LockBit later in the year too, after it went inexplicably dark for two weeks. Analyst1’s undercover investigator revealed they had “received another message from a third party who indicated they may have hacked the gang’s infrastructure … I believe the gang went dark to clean up the intrusion into its infrastructure.”
Analyst1 didn’t say whether the third party that claimed to have hacked LockBit was a law enforcement agency, a criminal hacker, or another ransomware gang, but all are possible—there is no honor among thieves.
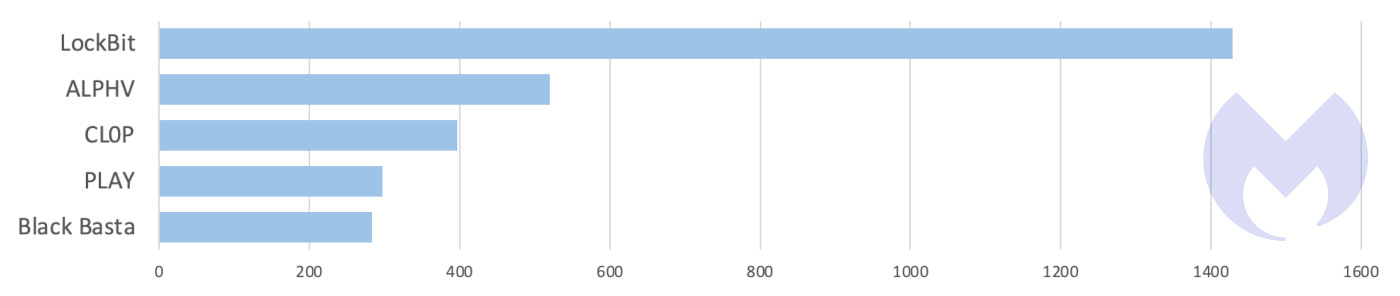
ALPHV would certainly be of great interest to both law enforcement and its rivals. Over the last 18 months it has been the second most dangerous ransomware group in the world, listing more victims on its leak site than every other group apart from LockBit.
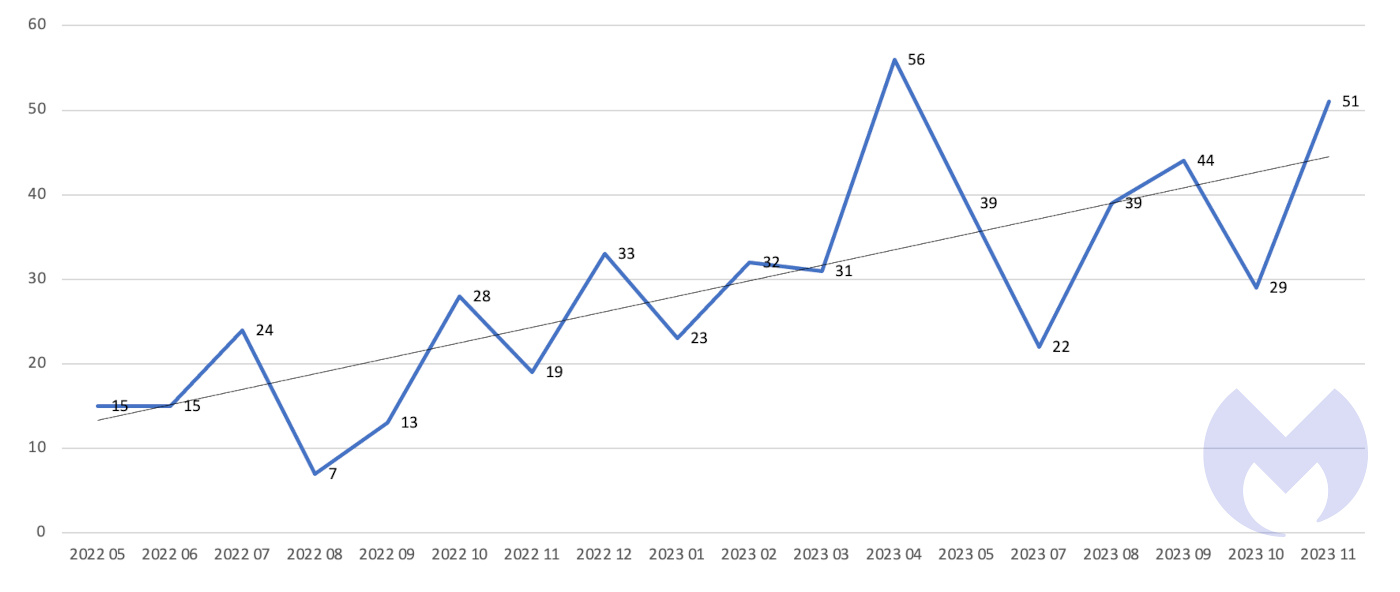
The number of known monthly attacks by the group has increased steadily over the last 18 months, too.
Even if another ransomware gang isn’t behind ALPHV’s woes, one of them is certainly looking to profit from it.
Bleeping Computer reports that LockBit has been attempting to recruit affiliates from ALPHV. The gang is reportedly offering the use of its data leak site and negotiation panel to ALPHV affiliates so they can resume negotiations with victims that have been disrupted. At least one victim previously listed on the ALPHV site is now listed on the LockBit site.
Whether ALPHV’s troubles are caused by tight-lipped law enforcement, an ironic lack of disaster recovery planning, or some other sleight of hand, any disruption to the ransomware ecosystem is a welcome early Christmas present in our book.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Our business solutions remove all remnants of ransomware and prevent you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.