New ransomware group demands Change Healthcare ransom
The Change Healthcare ransomware attack has taken a third cruel twist. A new ransomware group, RansomHub, has listed the organisation as a victim on its dark web leak site, saying it has 4 TB of “highly selective data,” which relates to “all Change Health clients that have sensitive data being processed by the company.”
The announcement follows a series of events that require some unpacking.
Change Healthcare is one of the largest healthcare technology companies in the USA, responsible for the flow of payments between payers, providers, and patients. It was attacked on Wednesday February 21, 2024, by a criminal “affiliate” working with the ALPHV ransomware group, which led to huge disruptions in healthcare payments. Patients were left facing enormous pharmacy bills, small medical providers teetered on the edge of insolvency, and the government scrambled to keep the money flowing and the lights on.
American Hospital Association (AHA) President and CEO Rick Pollack described the attack as “the most significant and consequential incident of its kind against the US health care system in history.”
The notorious ALPHV ransomware group claimed responsibility, chalking up Change Healthcare as one of a raft of healthcare victims in what looked like a deliberate campaign against the sector at the start of 2024.
ALPHV used the ransomware-as-a-service (RaaS) business model, selling the software and infrastructure used to carry out ransomware attacks to criminal gangs known as affiliates, in return for a share of the ransoms they extorted.
On March 3, a user on the RAMP dark web forum claimed they were the affiliate behind the attack, and that ALPHV had stolen the entirety of a $22 million ransom paid by Change Healthcare. Shortly after, the ALPHV group disappeared in an unconvincing exit scam designed to make it look as if the group’s website had been seized by the FBI.
ALPHV’s exit left Change Healthcare with nothing to show for its $22 million payment, a disgruntled affiliate looking for a ransom, and very possibly two different criminal gangs—ALPHV and its affiliate—in possession of a huge trove of stolen data.
Now, a month later, a newcomer ransomware group, RansomHub has listed Change Healthcare as a victim on its website.
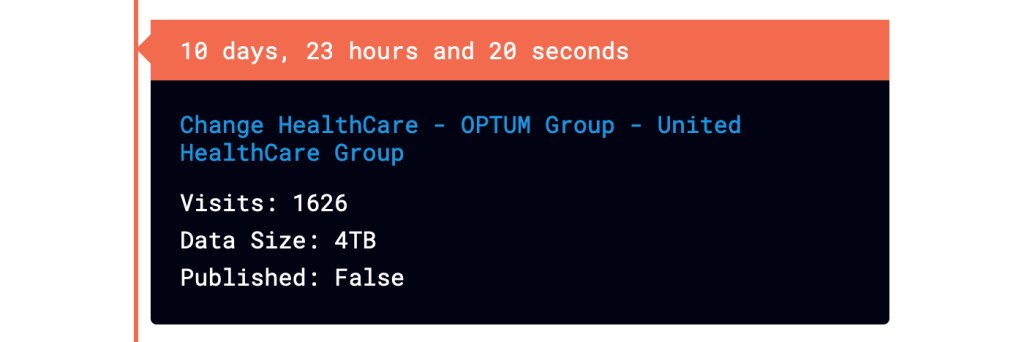
While some have speculated that Change Healthcare has suffered a second attack, the RansomHub site itself makes the connection to the events surrounding February 21 quite clear:
As an introduction we will give everyone a fast update on what happened previously and on the current situation.
ALPHV stole the ransom payment (22 Million USD) that Change Healthcare and United Health payed in order to restore their systems and prevent the data leak.
HOWEVER we have the data and not ALPHV.
RansomHub first appeared in late February and its arrival dovetails neatly with ALPHV’s disappearance in very early March, leading some to think they are the same group under two different names.
The statement also pours water on the idea that RansomHub is a rebrand of the ALPHV group with its suggestion that “we have the data and not ALPHV.” However, any public statement like this has to be tempered by the fact that ransomware groups are prolific liars.
It’s not uncommon for affiliates to work with multiple RaaS providers, so the most likely explanation is that having lost its money to ALPHV, the affiliate that ransacked Change Healthcare has paired up with a different ransomware group.
Whatever the reason, there is no comfort in it for Change Healthcare. Having apparently already paid a ransom thirty times greater than the average demand, it now has to decide whether it’s going to pay out again.
For everyone else, it’s a lesson in how devastating ransomware can be, and how badly things can go even when you pay a ransom.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Our business solutions remove all remnants of ransomware and prevent you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.