Notifications from FB and theft of business account passwords
Credit to Author: Andrey Kovtun| Date: Tue, 11 Jun 2024 10:29:47 +0000
Cybercriminals in the password theft business are constantly coming up with new ways to deliver phishing emails. Now they’ve learned to use a legitimate Facebook mechanism to send fake notifications threatening to block Facebook business accounts. We explore how the scheme works, what to pay attention to, and what measures to take to protect business accounts on social networks.
Anatomy of the phishing attack on Facebook business accounts
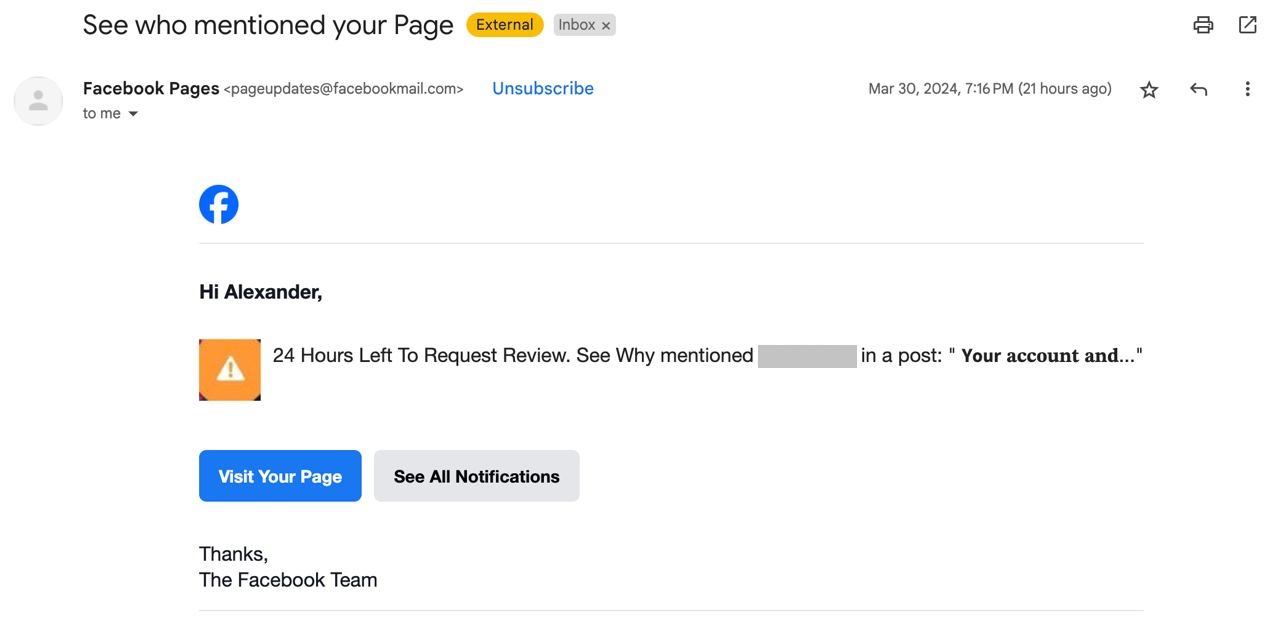
It all starts with a message sent by the social network itself to the email address linked to the victim’s Facebook business account. Inside is a menacing icon with an exclamation mark, and an even more menacing text: “24 Hours Left To Request Review. See Why.”
Added to this are other words which, combined with the above text, look odd. But a manager responsible for Facebook may, in haste or in panic, fail to spot these irregularities and follow the link by clicking the button in the email or manually open Facebook in a browser and check for the notifications.
Either way, they’ll end up on Facebook. After all, the email is real, so the buttons really do point to the social network’s site. A notification is waiting there — with the now familiar orange icon and same threatening words: “24 Hours Left To Request Review. See Why.”
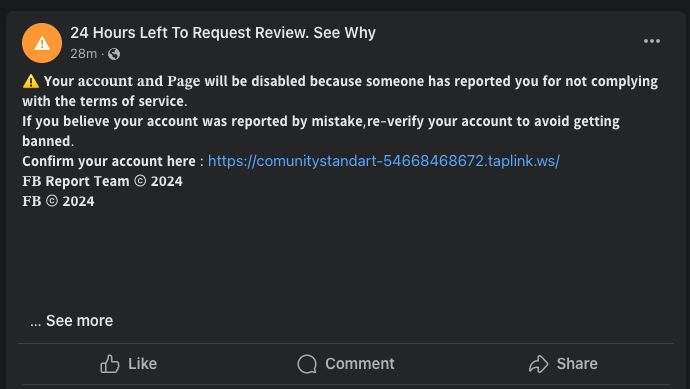
Phishing notification informing the victim their account will be blocked for non-compliance with the terms of service
The notification contains more details, alleging that the account and page are to be blocked because someone complained about their non-compliance with the terms of service. The victim is then prompted to follow a link to dispute the decision to block their account.
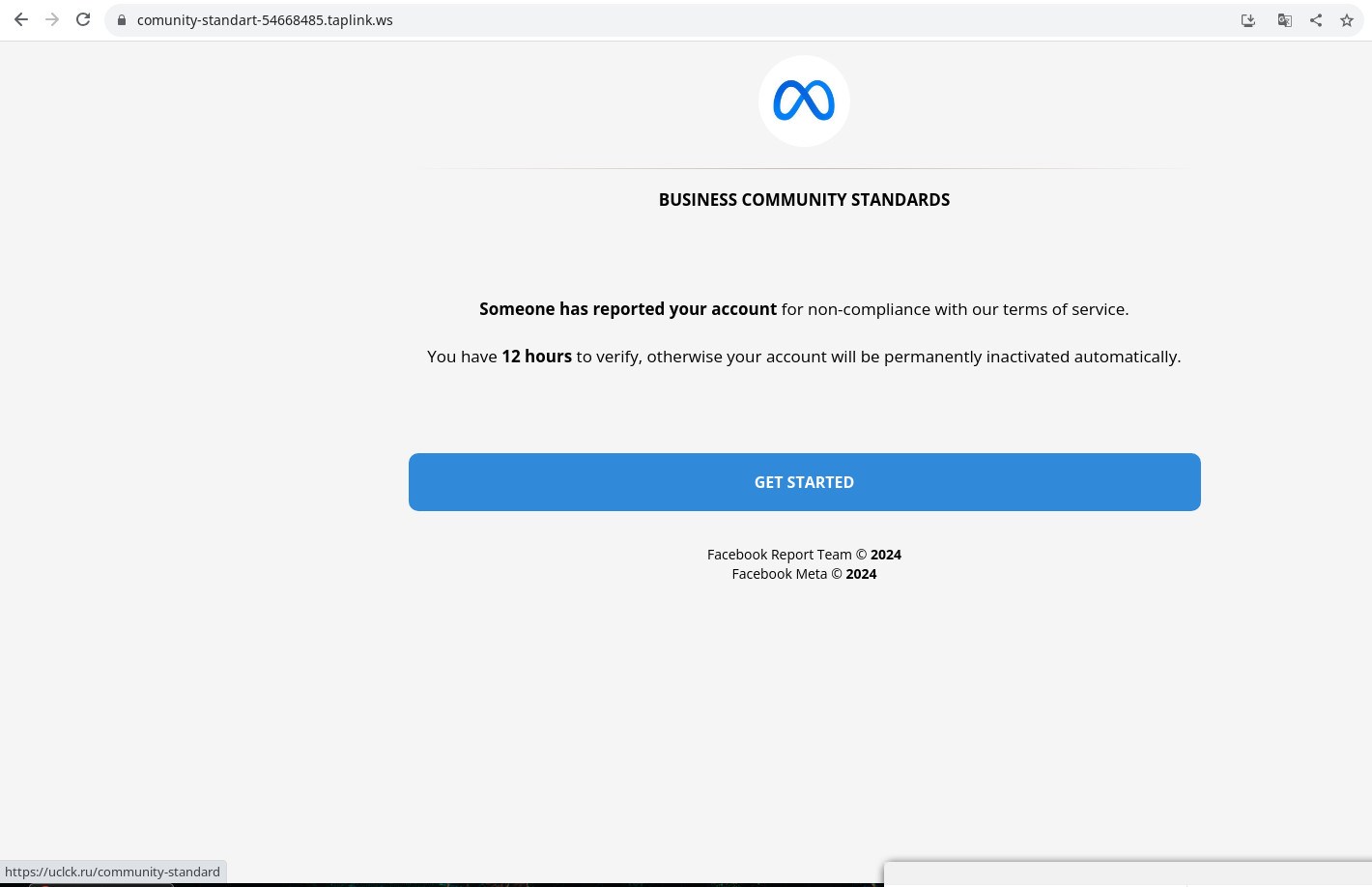
If they do, a website opens (this time, bearing the Meta logo, not Facebook) with roughly the same message as in the notification, but the time granted to resolve the issue has been halved to 12 hours. We suspect that scammers use the Meta logo this time because they try similar schemes on other Meta platforms — we found at least one “location” on Instagram with the same name: “24 Hours Left To Request Review. See Why.”
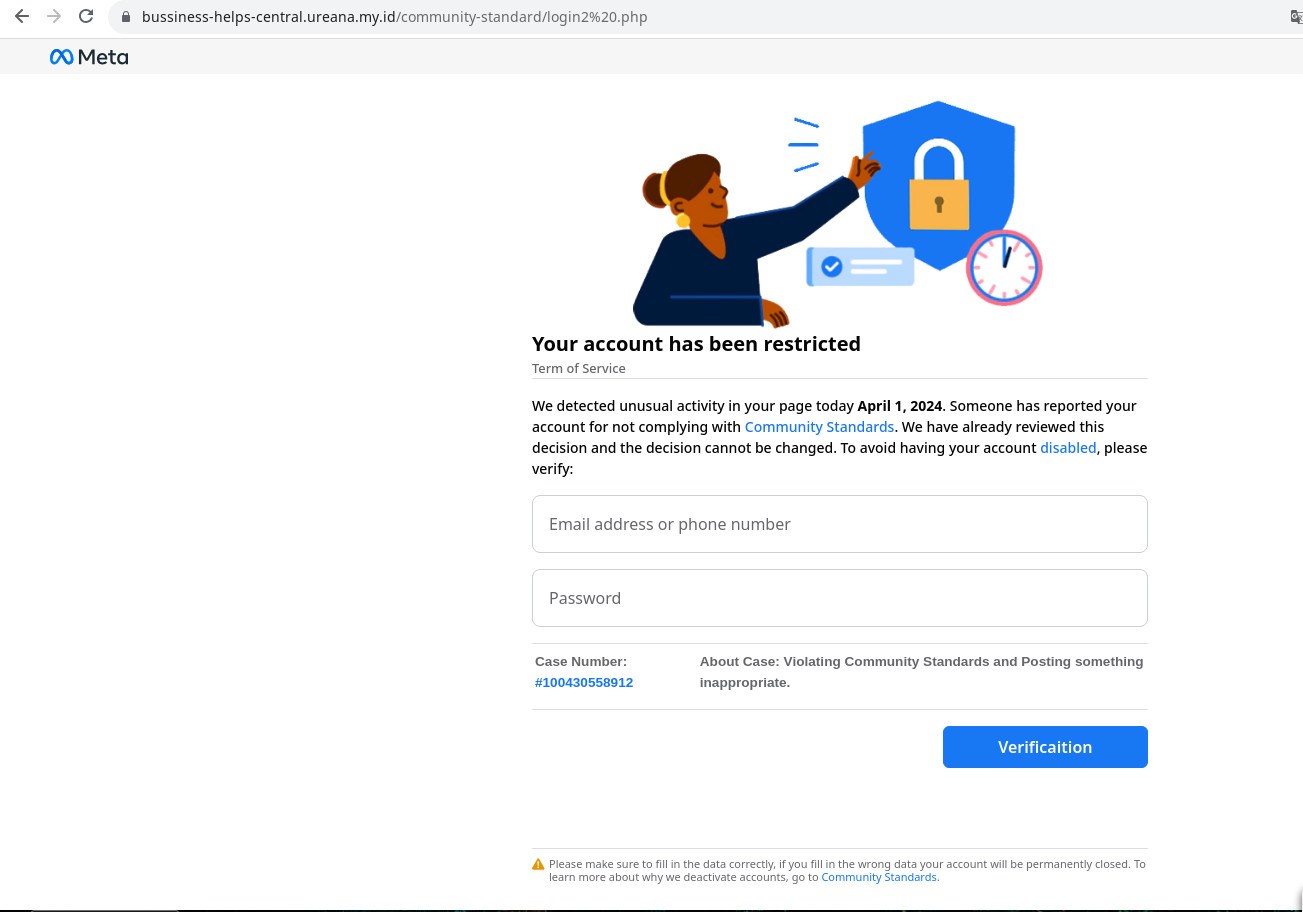
After clicking the Start button, through a series of redirects the visitor lands on a page with a form asking initially for relatively innocent data: page name, first and last names, phone number, date of birth.
It’s the next screen where things get juicy: here you need to enter the email address or phone number linked to your Facebook account and your password. As you might guess, it’s this data that the attackers are after.
How the phishing scheme exploits real Facebook infrastructure
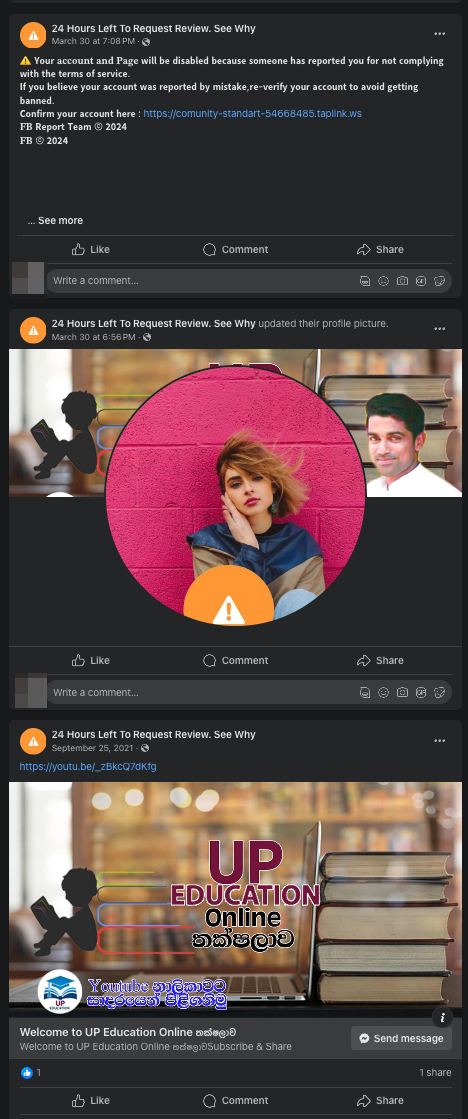
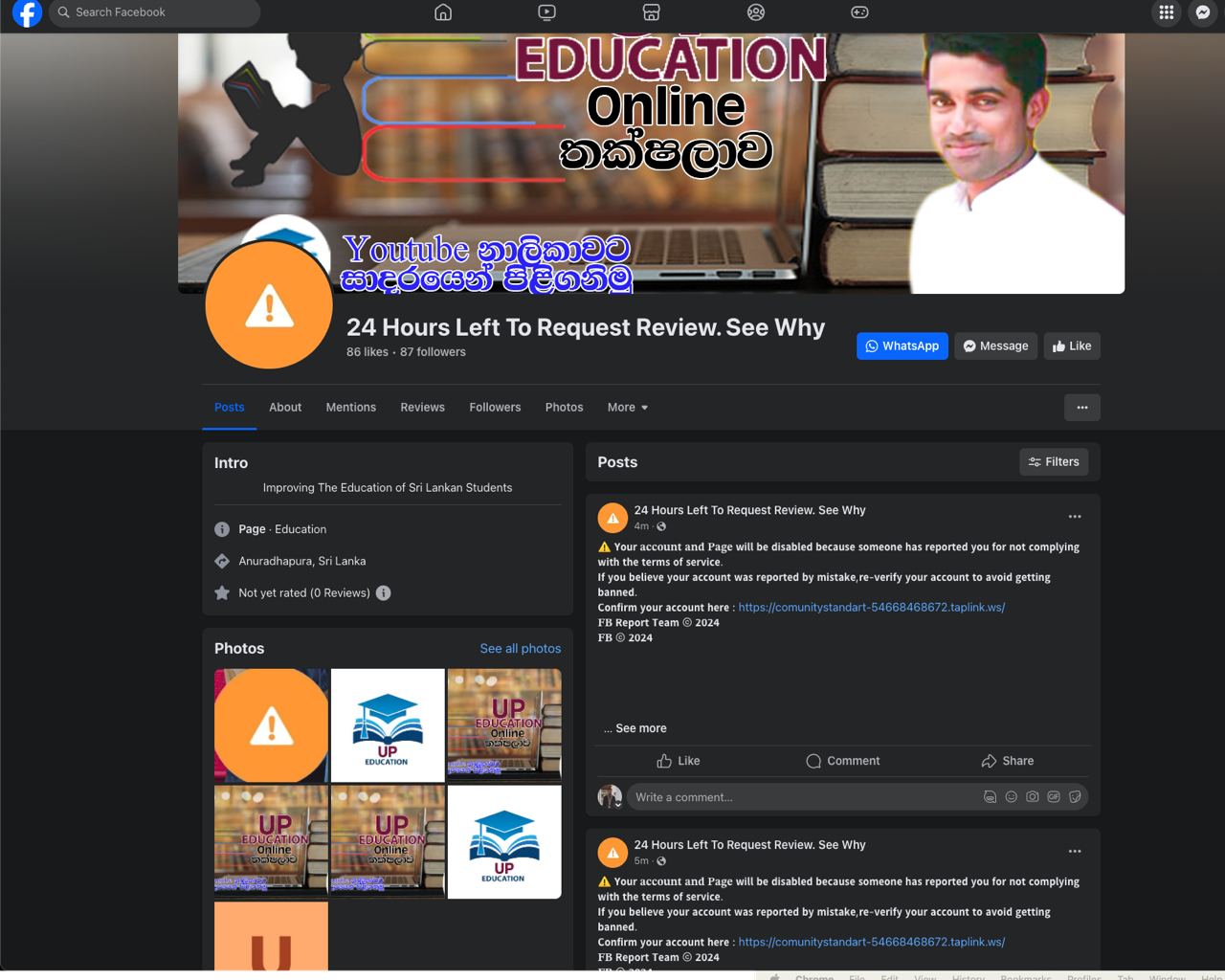
Now let’s see how threat actors get Facebook to send phishing notifications on their behalf. They do so by using hijacked Facebook accounts. The account name is changed straight away to the most troubling title: “24 Hours Left To Request Review. See Why.” They also change the profile pic so that the preview shows an orange icon with the exclamation mark already familiar to us from the email and notification.
That done, the message about the account block is posted from the account. At the bottom of this message, a mention of the victim’s page appears after a few dozen empty lines. By default it’s hidden, but on clicking the “See more” link in the phishing post, the mention becomes visible.
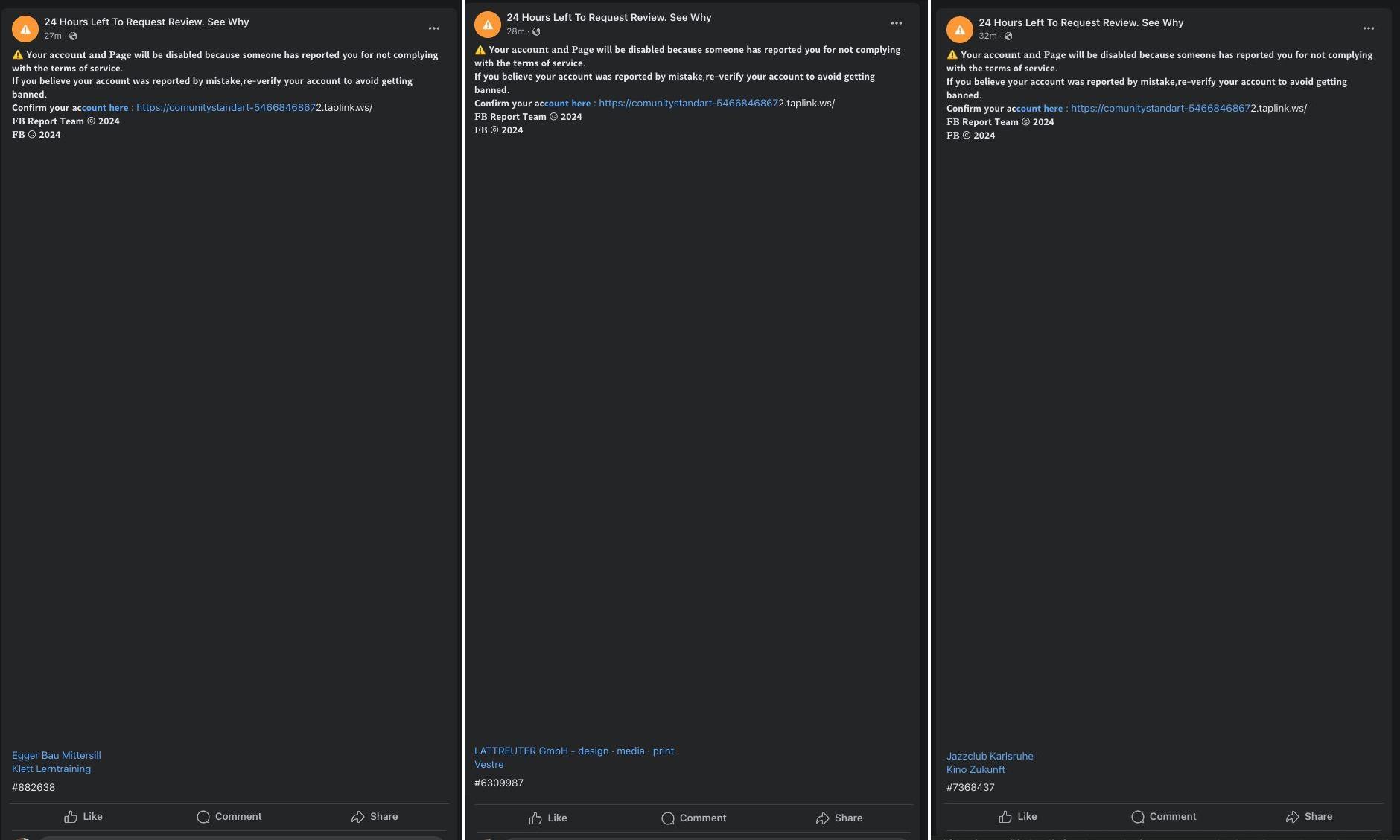
The trick is the hard-to-spot mention of the targeted Facebook business account at the bottom of the post
Threat actors post such messages from the hijacked account in bulk all at once, each of which mentions one of the target Facebook business accounts.
Hijacked accounts generate a slew of posts, each of which mentions the account of a targeted organization
As a result, Facebook diligently sends notifications to all accounts mentioned in these posts, both within the social network itself and to the email addresses linked to these accounts. And because delivery is via the actual Facebook infrastructure, these notifications are guaranteed to reach their intended recipients.
How to protect business social media accounts from hijacking
We should note that phishing isn’t the only threat to business accounts. There exists an entire class of malware specially created for password theft; such programs are known as password stealers. For this same purpose, attackers can also use browser extensions — see our recent post about their use in hijacking Facebook business accounts.
Here’s what we recommend for protecting the social media accounts of your business:
- Always use two-factor authentication wherever possible.
- Pay close attention to notifications about suspicious login attempts.
- Make sure all your passwords are both strong and unique. To generate and store them, it’s best to use a password manager.
- Carefully check the addresses of pages asking for account credentials: if there’s even the slightest suspicion that a site is fake, do not enter your password.
- Equip all work devices with reliable protection that will warn of danger ahead of time and block the actions of both malware and browser extensions.