Oops: DanaBot Malware Devs Infected Their Own PCs

Credit to Author: BrianKrebs| Date: Thu, 22 May 2025 21:53:21 +0000
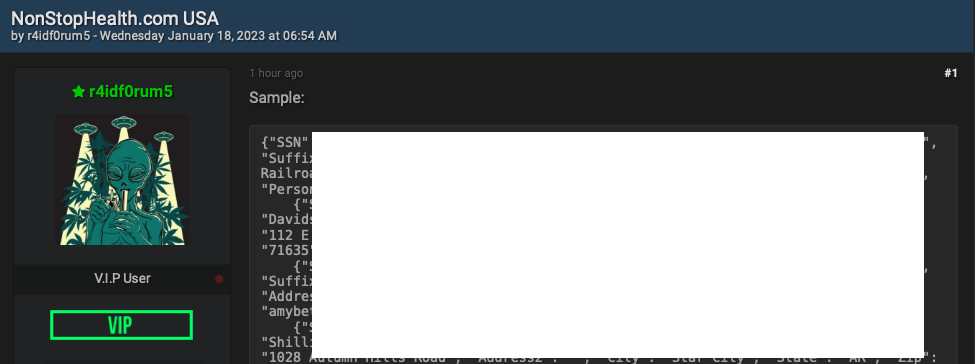
The U.S. government today unsealed criminal charges against 16 individuals accused of operating and selling DanaBot, a prolific strain of information-stealing malware that has been sold on Russian cybercrime forums since 2018. The FBI says a newer version of DanaBot was used for espionage, and that many of the defendants exposed their real-life identities after accidentally infecting their own systems with the malware.
Read More