WannaCry: Sometimes you can blame the victims
Credit to Author: Ira Winkler| Date: Tue, 16 May 2017 05:46:00 -0700
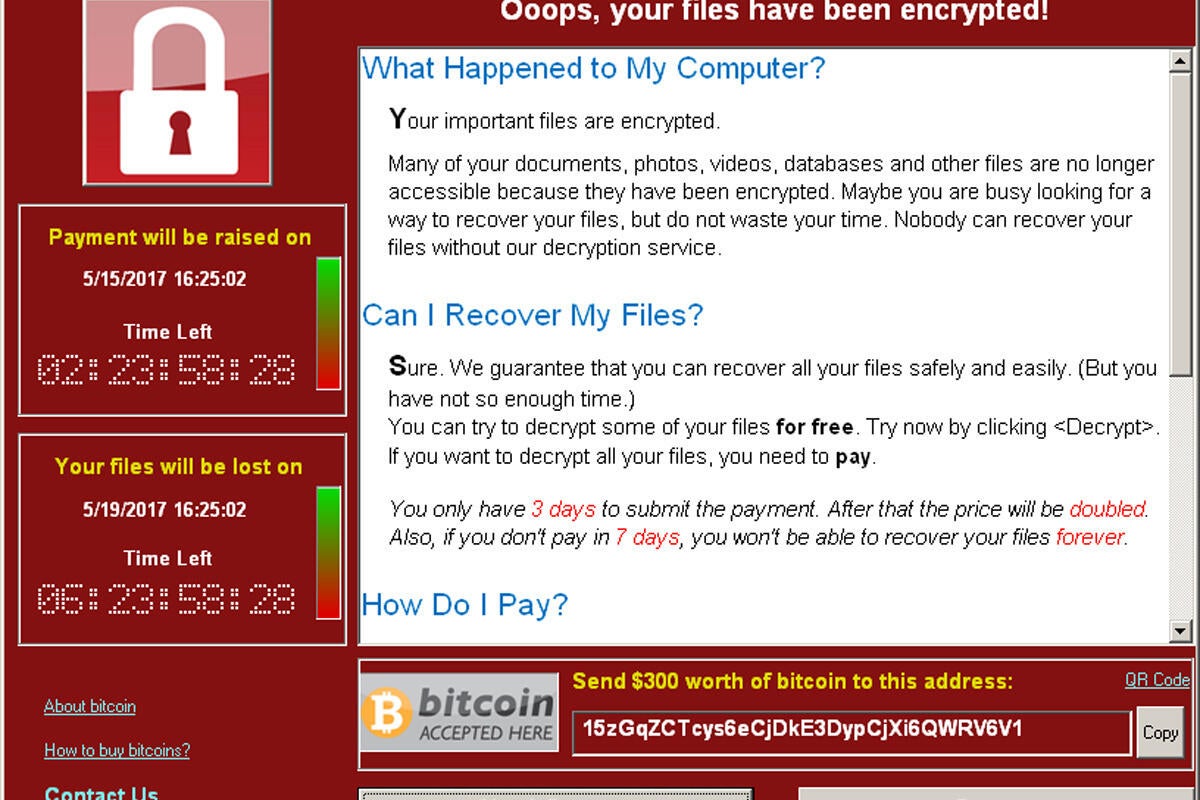
The WannaCry ransomware attack has created at least tens of millions of dollars of damage, taken down hospitals, and as of the time of this writing, another round of attacks is considered imminent as people show up to work after the weekend. Of course, the perpetrators of the malware are to blame for all the damage and suffering that has resulted. It’s not right to blame the victims of a crime, right?
Well, actually, there are cases when victims have to shoulder a portion of the blame. They may not be criminally liable as accomplices in their own victimhood, but ask any insurance adjuster whether a person or institution has a responsibility to take adequate precautions against actions that are fairly predictable. A bank that leaves bags of cash on the sidewalk overnight instead of in a vault is going to have a hard time getting indemnified if those bags go missing.
To read this article in full or to leave a comment, please click here


 IDG
IDG

