By virtualizing the Android OS, Cog Systems says it adds more security to smartphones
Credit to Author: Peter Sayer| Date: Mon, 27 Feb 2017 10:31:00 -0800
It sounds like a smartphone user’s worst fear: Software that starts up before the phone’s operating system, intercepting and encrypting every byte sent to or from the flash memory or the network interface.
This is not some new kind of ransomware, though. This is the D4 Secure Platform from Cog Systems.
The product grew out of custom security software the company developed for governments, and which it saw could also be put to use in the enterprise as a way to make smartphones more productive while still maintaining a high level of security.
It includes a Type 1 hypervisor, a virtualized VPN and additional storage encryption that wrap the standard Android OS in additional layers of protection largely invisible to the end user.
“We run the VPN and firewall completely outside the OS. A lot of people love the idea of a non-bypassable VPN,” said Cog Systems CEO Dan Potts.
Cog Systems has modified a version of HTC’s A9 smartphone to run the D4 software, although it can add it to almost any Android phone with an ARM processor. The only signs it is there are an extra splash screen that appears after the hardware manufacturer’s, and a request for a PIN to decrypt the file store before Android will even boot.
“If you get it wrong, it’s right back to factory settings,” said Cog Systems’ chief marketing officer Carl Nerup.
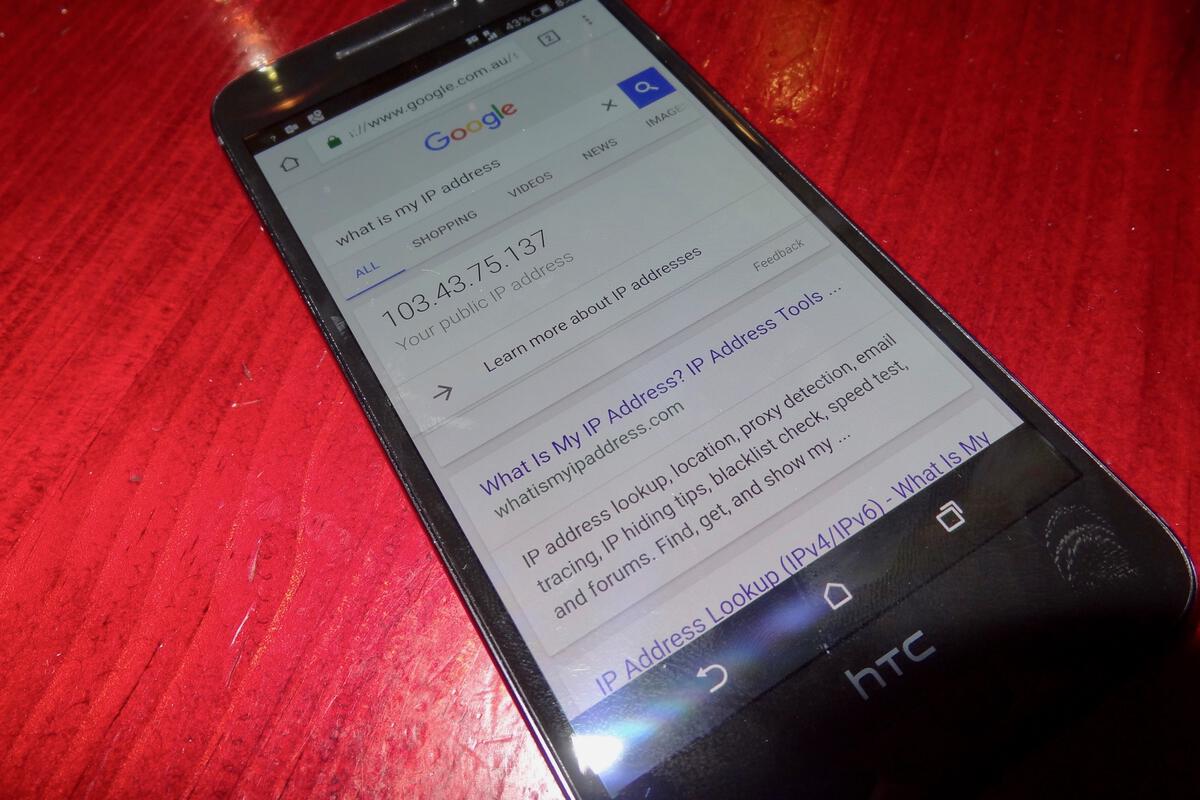
Once the phone has booted, the only way to tell it’s not a stock Android device is to use a service that displays its public IP address — asking Google “What’s my IP?” is one such. That will display the address of the far end of the VPN rather than an address attributed by the cellular carrier.
Another element of the phone that’s virtualized by D4 is the key store, an essential protection since someone hacked the TrustZone in Qualcomm’s chips last year, breaking Android’s Full Disk Encryption in the process.
With D4, said Potts, “Every time Android accesses the TrustZone it has to go through the hypervisor so we can intercept that.”
All that’s achieved with minimal overhead, Potts said, because most ARM processors have hardware support for encryption these days. As for the effect on battery life, while there is a “small degradation” today, but Potts thinks D4 may ultimately even improve battery life as virtualization of operating system elements makes it easier to suspend unneeded functions.
Enterprises can use D4 with their existing mobile device management tools. The control that the VPN gives them means they can give smartphone users access to a greater range of applications within their existing whitelisting or blacklisting policies, potentially allowing them to be more productive.
Cog Systems touts a stack of government certifications for its modified A9, including FIPS-140-2, NIAP VPN PP and FDE PP, and says it is under evaluation for the U.S. National Security Agency’s Commercial Solutions for Classified (CSfC) program.
The company didn’t just produce D4 out of nowhere: The developers have a solid history of mobile virtualization work, with many of them having worked on Open Kernel Labs’ OKL4 microvisor, found in billions of mobile devices, before forming Cog Systems.
Potts and Nerup are in Barcelona, the venue for Mobile World Congress, this week to promote their modified A9, which they claim is the world’s most secure smartphone.
“We’re ready to announce commercial availability this week,” Nerup said.
They don’t have a booth at the show, but if you can find them, maybe you can hire them to modify a phone for you.