Petya expands its scope: A global ransomware threat
Credit to Author: Trend Micro| Date: Tue, 29 Aug 2017 18:47:44 +0000

Ransomware remains a formidable threat for individual users and businesses alike, particularly as new sample families continue to be discovered by security researchers. What makes ransomware so dangerous is the fact that victims are denied access to their most important files and data – a problem that could potentially topple an enterprise if not dealt with quickly.
Making matters worse, even if attackers are paid the ransom, there's no guarantee that decryption will be lifted and access restored – in some cases, files simply remain locked away as hackers make off with their payment. In other instances, hackers will ask for a second, higher ransom after victims pay the first.
One of the first steps in guarding against ransomware infections is remaining in-the-know about emerging threats and attack styles. Recently, WannaCry or WannaCrypt grabbed headlines as the next big thing in ransomware attacks. Now, a new threat has come to the surface: Petya.
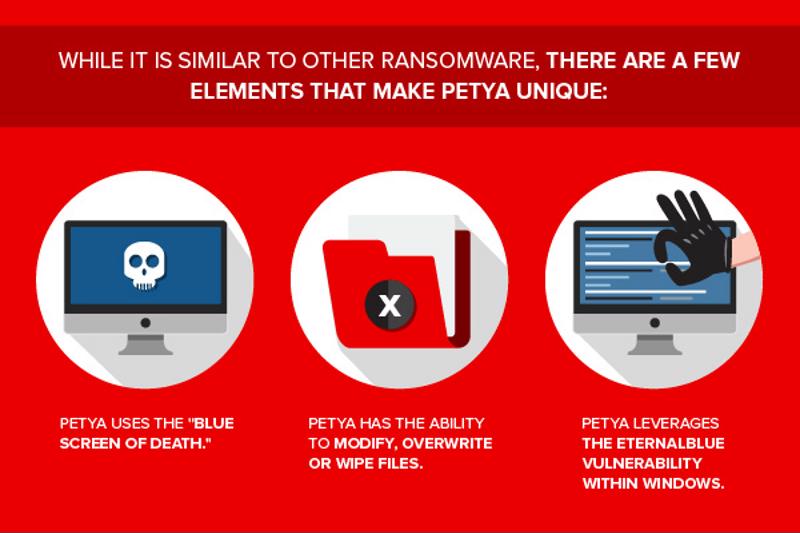
What makes Petya different?
Like most traditional ransomware samples, Petya provides hackers with the ability to encrypt victims' system files, preventing access until a ransom amount is paid. Trend Micro detects Petya as RANSOM_PETYA.SMA, and researchers noted that while it is similar to other ransomware infections, there are a few elements that make Petya unique:
- Ransomware with wiping capabilities: In addition to locking away files on victims' infected systems, Petya also has the ability to modify files. In other words, the sample can overwrite or even completely wipe system hard disks.
- The dreaded blue screen: Where most ransomware samples display a notification to users of the infection as well as the ransom demands, Petya does this with the blue screen of death (BSoD), which is a signal to victims of the seriousness of the attack.
- Not a new threat: Trend Micro noted that while Petya has been capturing considerable attention in 2017, it was actually discovered the year previous. Since then, the sample has seen a number of changes, including joining another ransomware family, Mischa. This provided the double-whammy infection with dual capabilities – file modification as well as encryption.
- Exploiting EternalBlue – and then some: Like WannaCry, Petya also leverages the EternalBlue vulnerability within Windows' Server Message Block to support initial infection. Petya, however, has other independent attack vectors in addition to this exploit to ensure a successful infection. If ransomware cannot be installed via Petya's modified version of PsExec, the sample will abuse the Windows Management Instrumentation Command-line for execution.
Petya attacks in Ukraine
Petya first garnered more recent attention in June 2017 when security researchers and investigators discovered that it was responsible for several large-scale attacks in Ukraine. According to New York Times contributors Nicole Perlroth, Mark Scott and Sheera Frenkel, the incident has been dubbed "an international cyberattack," and impacted a number of organizations in the country and elsewhere. There seemed to be little connection between infection victims, and the scope of the attack was considerably worrisome.
"In Kiev, the capital of Ukraine, A.T.M.s stopped working. About 80 miles away, workers were forced to manually monitor radiation at the old Chernobyl nuclear plant when their computers failed," Perlroth, Scott and Frenkel wrote. "And tech managers at companies around the world — from Maersk, the Danish shipping conglomerate, to Merck, the drug giant in the United States — were scrambling to respond. Even an Australian factory for the chocolate giant Cadbury was affected."
From there, the attack continued to spread to other businesses and and government agencies in Ukraine, and then to organizations in other countries. As ZDNet contributor Zack Whittaker noted, it's still unclear who perpetrated the attack, and while some are quick to point to "nation state" attackers, it's wise to hold off on these suspicions until there is evidence to support them.
"It's easy to want to assume that this could be a nation state attack, given that blame is usually pointed at Russia for major cyberattacks or political meddling," Whittaker wrote. "But there's no evidence at this time to suggest a government is behind the attack."
Petya's reach: Who was affected?
While investigators are still searching for those responsible, this pursuit could be difficult – but not impossible – due to the sheer size and number of victims involved in the rash of Petya infections. The New York Times noted that after initial attacks against organizations in Ukraine, other institutions outside of that country reported infections, including a Russian oil company, global shipping container company A.P. Moller-Maersk, French construction materials company Saint-Gobain, British marketing firm WWP and German railway company Deutsche Bahn.
Petya also affected organizations based in the U.S., or with American locations, including:
- Pharmaceutical company Merck.
- Pennsylvania health care provider Heritage Valley Health Systems, and its connected hospitals in Beaver and Sewickley, Pennsylvania.
- U.S. locations of multinational law firm DLA Piper.
DLA Piper, in particular, warned its clients from its Australian offices that it was dealing with a "serious global cyber incident," and was shutting down its email as a precaution.
According to Microsoft, before the end of June, Petya had spread to 65 countries total, including in Belgium and Brazil, impacting more than 12,500 machines.
Provider blocks ransom email
The case of Petya continues to get more interesting, as ZDNet reported that the email included in the sample's ransom message had been blocked by the provider supporting it. This means that victims don't actually have a place to send the $300 bitcoin ransom even if they wanted to – and those that did "wasted their money," according to Whittaker.
Posteo, the email provider in question, noted that the account tied to Petya's ransom message was blocked about two hours after initial attacks began. The company noted that it would "not tolerate the misuse of our platform."
"The immediate blocking of misused email accounts is the necessary approach by providers in such cases," Posteo said in a statement.
Guarding against Petya
While Petya is surely a powerful threat, there are best practices users and enterprises can take to protect against it, including:
- Ensuring patches are up-to-date: As Whittaker pointed out, a single point of entry is all Petya needs to infiltrate the network, and while a patch was released earlier this year for EternalBlue, recent attack incidents show that not everyone has installed the update yet. If an organization has 100 computers and all of them lack this patch, Petya can spread across the entire network. Security patches should be installed as quickly as possible, and on every machine within an organization's infrastructure.
- Avoid and restrict access to PsExec: As Trend Micro pointed out, this and other sys admin tools like PowerShell have provided the pivot point for Petya infections. Restricting use of these platforms can help reduce the chances of infection.
- Ensure regular backups: Ransomware attacks like Petya lose their impact when victims have a backup version of data to fall back on.
- Continually monitor for suspicious activity: Pinpointing unusual activity within the network can help IT admins take a more proactive stance on security, as well as provide the opportunity to stop unauthorized individuals from carrying out the necessary processes to execute an attack.
- Leverage more advanced security techniques: Trend Micro recommended utilizing behavior monitoring mechanisms to spot modifications like encryption, as well as deploying network segmentation and data categorization to prevent damage connected to an attack.
To find out more about Petya and how you can guard against advanced ransomware within your organization, contact the experts at Trend Micro today.