Infrastructure for the ‘Bad Rabbit’ Ransomware Appears to Have Shut Down
Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Wed, 25 Oct 2017 19:51:23 +0000
Looks like the bad bunny is already back in the box.
The new ransomware that infected hundreds of computers in Russia and eastern Europe Tuesday, appears to have already shut down operations, according to multiple security firms that were monitoring the malware. The ransomware, codenamed Bad Rabbit, spread quickly on Tuesday morning, propagating via booby-trapped Russian news sites to lock victims’ files and demand Bitcoin in return.
Read more: Kidnappers Around the World Want Their Ransoms Paid in Bitcoin
The hackers behind Bad Rabbit—who at this point are unknown—compromised a series of media and news websites to push a prompt to install a fake Adobe Flash update. Once the victim fell for the trick, the malware was served from servers under the control of the hackers. Some of these servers were called, for instance, 1dnscontrol[.]com and 185.149.120[.]3 (the brackets are so you don’t accidentally click on these links).
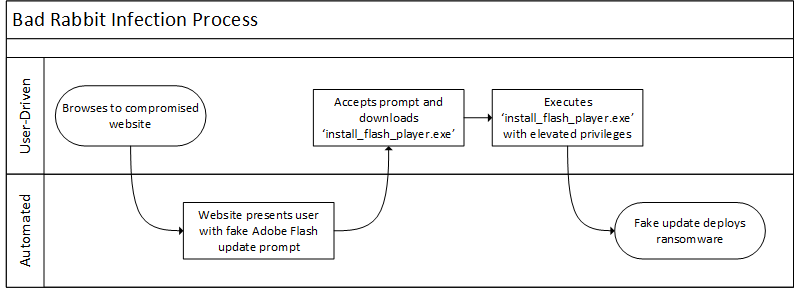
Those servers are now down, according to researchers at the security firms FireEye, ESET, McAfee, Avira, and Kaspersky Lab.
Nick Carr, a researcher at FireEye, told Motherboard in an email that his company blocked infections until around 15:00:00 UTC (or 11 a.m. EDT) Tuesday, “when the infection attempts ceased and attacker infrastructure—both 1dnscontrol[.]com and monitored sites containing the rogue code—were taken offline.”
“The use of strategic web compromises and profilers provide guardrails that allow attackers to select targets carefully and halt operations quickly,” he added.
Got a tip? You can contact this reporter securely on Signal at +1 917 257 1382, OTR chat at lorenzo@jabber.ccc.de, or email lorenzo@motherboard.tv
ESET’s researcher Marc-Etienne M.Lévei told me in a Twitter direct message that another server (185.149.120[.]3) used in the attack to send the fake Flash popup “stopped responding and was active only for a few hours,” on Tuesday.
Avira’s head of protection services Alexander Vukcevic confirmed in an email that the command and control servers are “not reachable anymore.” According to a Kaspersky Lab spokesperson, the Bad Rabbit infections stopped on Tuesday. Symantec also reported that “the vast majority of infection attempts” occurred in the first two hours after Bad Rabbit appeared.
McAfee researchers said through a spokesperson that they believe the hackers themselves took the infrastructure down, but it’s hard to know exactly what happened at this point. Perhaps the hackers got spooked when the malware got too much attention, or perhaps their hosting providers shut them down.
Unlike other ransomware outbreaks such as NotPetya, which some believe was launched by the same hackers as Bad Rabbit, this one appears to have had limited impact. Contrary to what other researchers believe, Craig Williams, a research manager at Talos, says Bad Rabbit might still be spreading slowly.
Williams said that him and other Talos researchers are seeing victim machines look up the command and control domain (1dnscontrol[.]com), so “it’s likely the malware is still out there attempting to propagate from other infected sites.”
As of Wednesday morning, according to ESET’s M.Lévei, some of the compromised sites that were pointing to the hackers’ infrastructure, such as argumentiru[.]com, had not cleaned up the compromise yet.
“[The hackers] can reactive [the servers] anytime and start spreading again,” M.Lévei told me.
Correction: a previous version of this story stated that the dark web site set up by the hackers for victims to pay the ransom and get the decryption key was down, based on our own tests. The site, however, appears to be back up.
Get six of our favorite Motherboard stories every day by signing up for our newsletter.