U.K. Man Avoids Jail Time in vDOS Case
Credit to Author: BrianKrebs| Date: Thu, 21 Dec 2017 13:56:01 +0000
A U.K. man who pleaded guilty to launching more than 2,000 cyberattacks against some of the world’s largest companies has avoided jail time for his role in the attacks. The judge in the case reportedly was moved by pleas for leniency that cited the man’s youth at the time of the attacks and a diagnosis of autism.
In early July 2017, the West Midlands Police in the U.K. arrested 19-year-old Stockport resident Jack Chappell and charged him with using a now-defunct attack-for-hire service called vDOS to launch attacks against the Web sites of Amazon, BBC, BT, Netflix, T-Mobile, Virgin Media, and Vodafone, between May 1, 2015 and April 30, 2016.
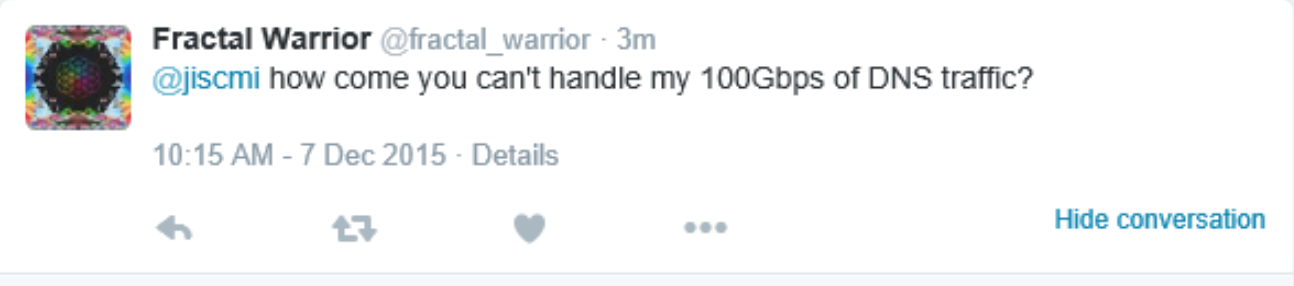
One of several taunting tweets Chappell sent to his DDoS victims.
Chappell also helped launder money for vDOS, which until its demise in September 2016 was by far the most popular and powerful attack-for-hire service — allowing even completely unskilled Internet users to launch crippling assaults capable of knocking most Web sites offline.
Using the Twitter handle @fractal_warrior, Chappell would taunt his victims while launching attacks against them. The tweet below was among several sent to the Jisc Janet educational support network and Manchester College, where Chappell was a student. In total, Chappell attacked his school at least 21 times, prosecutors showed.
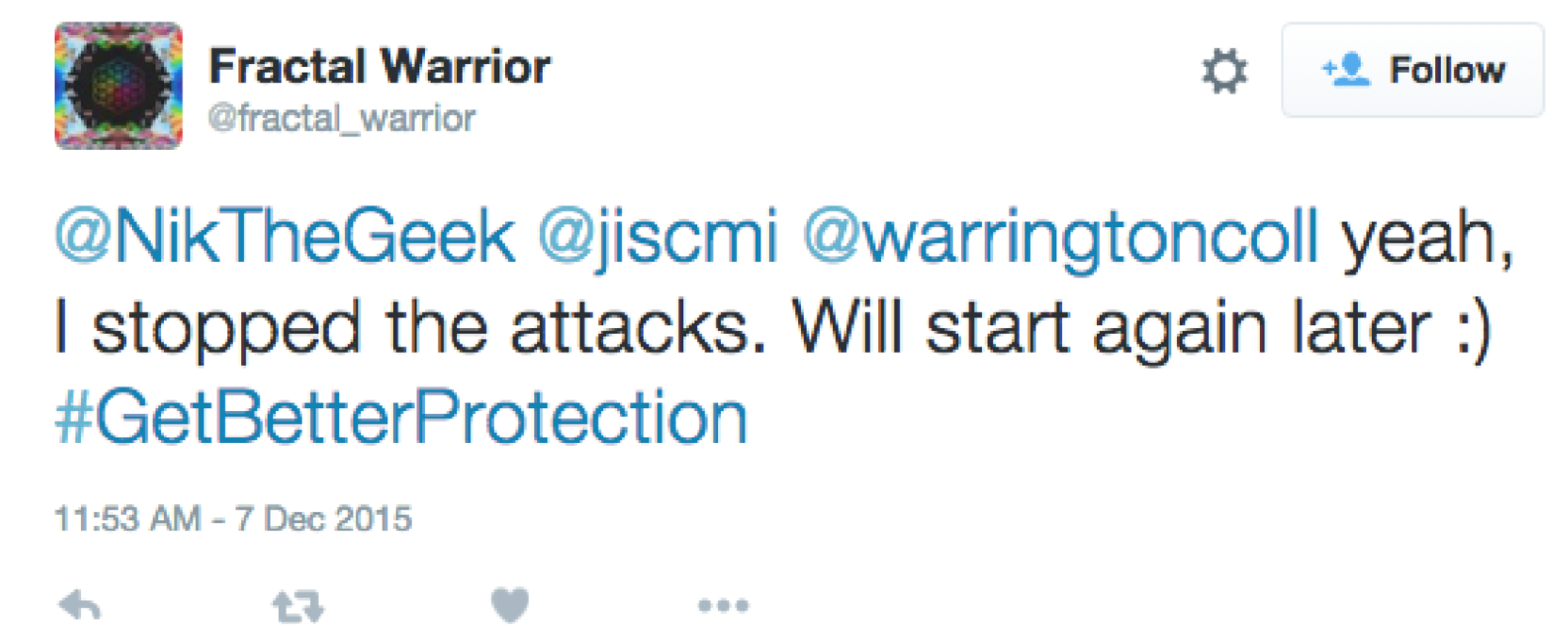
Another taunting Chappell tweet.
Chappell was arrested in April 2016 after investigators traced his Internet address to his home in the U.K. For more on the clues that likely led to his arrest, check out this story.
Nevertheless, the judge in the case was moved by pleas from Chappell’s lawyer, who argued that his client was just an impressionable youth at the time who has autism, a range of conditions characterized by challenges with social skills, repetitive behaviors, speech and nonverbal communication.
The defense called on an expert who reportedly testified that Chappell was “one of the most talented people with a computer he had ever seen.”
“He is in some ways as much of a victim, he has been exploited and used,” Chappell’s attorney Stuart Kaufman told the court, according to the Manchester Evening News. “He is not malicious, he is mischievous.”
The same publication quoted Judge Maurice Greene at Chappell’s sentencing this week, saying to the young man: “You were undoubtedly taken advantage of by those more criminally sophisticated than yourself. You would be extremely vulnerable in a custodial element.”
Judge Greene decided to suspend a sentence of 16 months at a young offenders institution; Chappell will instead “undertake 20 days rehabilitation activity,” although it’s unclear exactly what that will entail.
ANALYSIS/RANT
It’s remarkable when someone so willingly and gleefully involved in a crime spree such as this can emerge from it looking like the victim. “Autistic Hacker Had Been Exploited,” declared a headline about the sentence in the U.K. newspaper The Times.
After reading the coverage of this case in the press, I half expected to see another story saying someone had pinned a medal on Chappell or offered him a job.

Jack Chappell, outside of a court hearing in the U.K. earlier this year.
Yes, Chappell will have the stain of a criminal conviction on his record, and yes autism can be a very serious and often debilitating illness. Let me be clear: I am not suggesting that offenders like this young man should be tossed in jail with violent criminals.
But courts around the world continue to send a clear message that young men essentially can do whatever they like when it comes to DDoS attacks and that there will be no serious consequences as a result.
Chappell launched his attacks via vDOS, which provided a simple, point-and-click service that allowed even completely unskilled Internet users to launch massive DDoS attacks. vDOS made more than $600,000 in just two of the four years it was in operation, launching more than 150,000 attacks against thousands of victims (including this site).
In September 2016, vDOS was taken offline and its alleged co-creators — two Israeli man who created the business when they were 14 and 15 years old — were arrested and briefly detained by Israeli authorities. But despite assurances that the men (now adults) would be tried for their crimes, neither has been prosecuted.
In July 2017, a court in Germany issued a suspended sentence for Daniel Kaye, a 29-year-old man who allegedly launched extortionist DDoS attacks against several bank Web sites.
After the source code for the Mirai botnet malware was released in September 2016, Kaye built his own Mirai botnet and used it in several high-profile attacks, including a fumbled assault that knocked out Internet service to more than 900,000 Deutsche Telekom customers.
In his trial, Kaye admitted that a customer of his paid him $10,000 to attack the Liberian ISP Lonestar. He’s also thought to have launched DDoS attacks on Lloyds Banking Group and Barclays banks in January 2017. Kaye is now facing related cybercrime charges in the U.K.
Last week, the U.S. Justice Department unsealed the cases of two young men in the United States who have pleaded guilty to co-authoring Mirai, an “Internet of Things” (IoT) malware strain that has been used to create dozens of copycat Mirai botnets responsible for countless DDoS attacks over the past 15 months. Jha and his co-defendants in that case launched highly disruptive and extortionist attacks against a number of Web sites and used their creation to conduct lucrative click fraud schemes.
Like Chappell, the core author of Mirai — 21-year-old Fanwood, N.J. resident Paras Jha — launched countless DDoS attacks against his school, costing Rutgers University between $3.5 million and $9 million to defend against and clean up after the assaults (the actual damages will be decided at Jha’s sentencing in March 2018).
Time will tell if Kaye or Jha and his co-defendants receive any real punishment for their crimes. But I would submit that if we don’t have the stomach to put these “talented young hackers” in jail when they’re ultimately found guilty, perhaps we should consider harnessing their skills in less draconian but still meaningfully punitive ways, such as requiring them to serve several years participating in programs designed to keep other kids from following in their footsteps.
Doing anything less smacks of a disservice to justice, glorifies DDoS as an essentially victimless crime, and serves little deterrent that might otherwise make it less likely that we will see fewer such cases going forward.