DJI's bounty problems and video surveillance programs | Salted Hash Ep 13
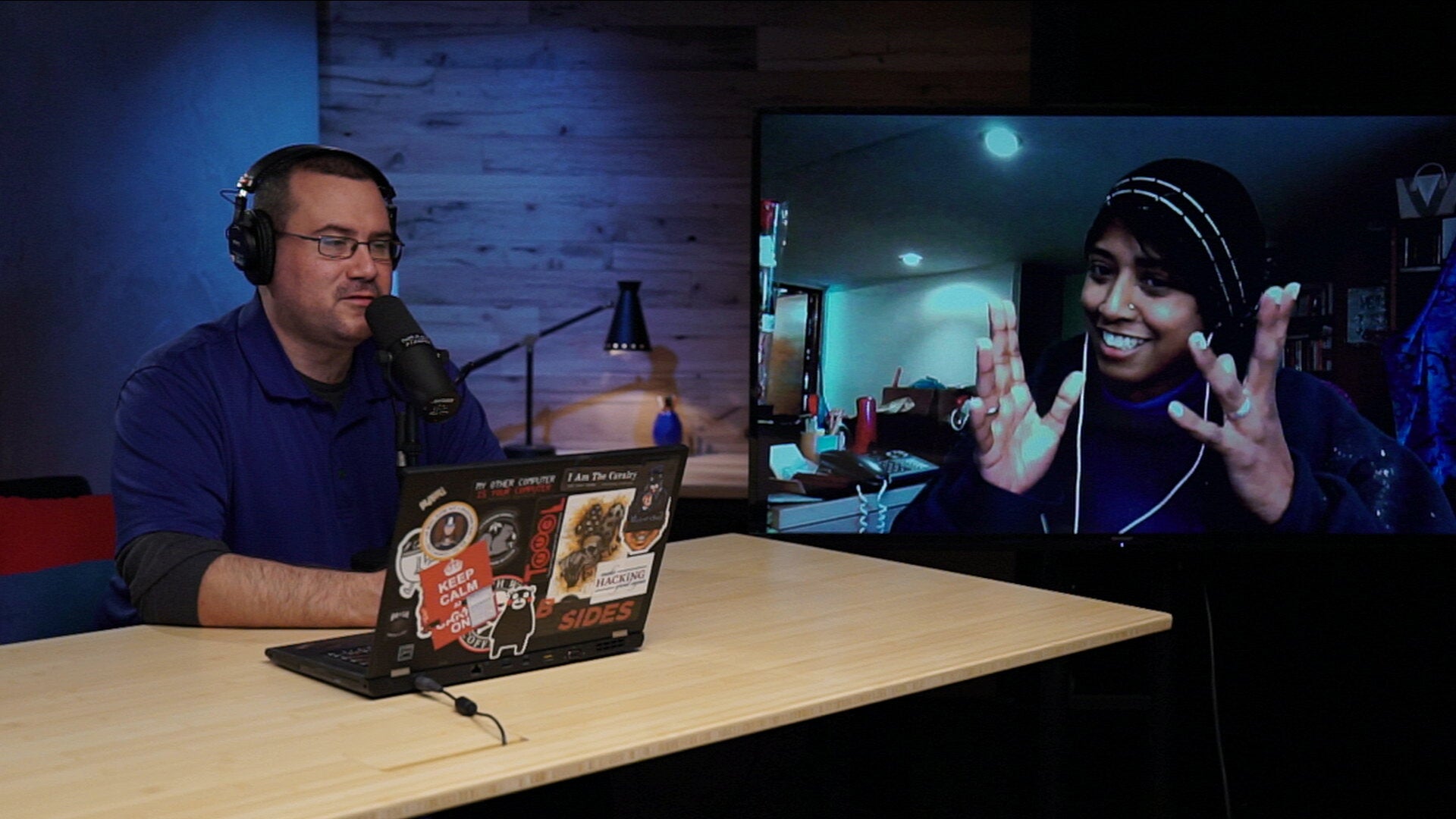
Host Steve Ragan unpacks the latest news about Chinese company DJI's bug bounty program, plus new developments in video surveillance and more, with Fahmida Rashid.
RSS Reader for Computer Security Articles

Host Steve Ragan unpacks the latest news about Chinese company DJI's bug bounty program, plus new developments in video surveillance and more, with Fahmida Rashid.

Credit to Author: Woody Leonhard| Date: Mon, 08 Jan 2018 05:28:00 -0800
Microsoft’s hasty Meltdown/Spectre patches, released late on Jan. 4, have started baring their fangs. Complaints about Win10 Fall Creators Update cumulative update KB 4056892 and Win7 Monthly Rollup KB 4056894 resulting in blue screens — particularly on AMD Athlon, Sempron, Opteron and Turion processors — started appearing shortly after the patches were released.

Credit to Author: SSD / Maor Schwartz| Date: Sun, 07 Jan 2018 06:28:24 +0000
漏洞概要 以下安全公告描述了在D-Link DSL-6850U BZ_1.00.01 – BZ_1.00.09中的发现的两个漏洞。 D-Link DSL-6850U是一款“以色列Bezeq制造的路由器”,在这款路由器中发现的漏洞是: 默认凭证 远程命令执行 漏洞提交者 一位独立的安全研究人员向 Beyond Security 的 SSD 报告了该漏洞 厂商响应 Bezeq在6月9日被告知了这个漏洞,并且发布了补丁来解决这些漏洞。 漏洞详细信息 该设备定制的固件存在以下问题: 默认启用远程Web管理 不能禁用默认帐户 默认凭证 默认帐户用户名是:support 密码是:support 远程命令执行 shell界面只允许执行一组内置命令,但是你可以通过’&’ ‘||’ 插入命令到shell: [crayon-5a529cda84c8f912287642/] 上述命令执行后返回一个BusyBox shell
Read More
Credit to Author: Andy Greenberg| Date: Sun, 07 Jan 2018 19:23:27 +0000
The uncanny coincidences among the Meltdown and Spectre discoveries raise questions about “bug collisions”—and the safety of the NSA’s hidden vulnerability collection.
Read More
Credit to Author: Gregg Keizer| Date: Sat, 06 Jan 2018 12:58:00 -0800
Amid the panicked response this week to the news of significant, though not-yet-exploited, vulnerabilities in the vast bulk of the world’s microprocessors, it went almost unnoticed that most browser makers responded by updating their wares in the hope of fending off possible web-based attacks.
The Google-driven revelations – it was members of the search firm’s Project Zero security team who identified the multiple flaws in processors designed by Intel, AMD and ARM – were to go public next week, on Jan. 9, this month’s Patch Tuesday. At that time, a coordinated effort by multiple vendors, from OS developers to silicon makers, was to debut with patches to protect, as best could be done without replacing the CPU itself, systems against flaws grouped under the umbrella terms of Meltdown and Spectre. That plan went out the window when leaks started to circulate earlier this week.
Credit to Author: Kevin Brown| Date: Fri, 05 Jan 2018 20:10:49 +0000
If you know what coach won back-to-back Super Bowls or that a cassowary is a giant flightless bird and not a kitchen utensil then you could be a winner at… Read more »
The post When Lag Time Interferes with your Favorite Live app, it’s not Trivial appeared first on Schneider Electric Blog.
Read More
Credit to Author: Lily Hay Newman| Date: Sat, 06 Jan 2018 16:30:41 +0000
Meltdown and Spectre Fixes Arrive—But Don’t Solve Everything
Read More
Credit to Author: Brian Barrett| Date: Sat, 06 Jan 2018 14:00:00 +0000
Meltdown and Spectre, dossier drama, and more of the week’s top security news.
Read More