What Is Application Shielding?
![]()
Credit to Author: Lily Hay Newman| Date: Sun, 05 May 2019 11:00:00 +0000
Security firms are increasingly touting application shielding as an important layer of defense. But it may be better suited to DRM.
Read MoreRSS Reader for Computer Security Articles
![]()
Credit to Author: Lily Hay Newman| Date: Sun, 05 May 2019 11:00:00 +0000
Security firms are increasingly touting application shielding as an important layer of defense. But it may be better suited to DRM.
Read More
Credit to Author: Emily Dreyfuss| Date: Sat, 04 May 2019 13:00:00 +0000
Hacking big companies, building a better voting machine, and more security news this week.
Read More
Credit to Author: Alex Baker-Whitcomb| Date: Fri, 03 May 2019 23:10:03 +0000
Catch up on the most important news today in 2 minutes or less.
Read More
Credit to Author: Andrew Brandt| Date: Fri, 03 May 2019 19:45:43 +0000
By Andrew Brandt A new ransomware that calls itself MegaCortex got a jolt of life on Wednesday as we detected a spike in the number of attacks against Sophos customers around the world, including in Italy, the United States, Canada, the Netherlands, Ireland, and France. The attackers delivering this new malware campaign employed sophisticated techiques […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/pFdm0BTbxug” height=”1″ width=”1″ alt=””/>
Read More
Credit to Author: Andy Greenberg| Date: Fri, 03 May 2019 11:00:00 +0000
A group of likely Chinese hackers has poisoned the software of at least six companies in just the last three years.
Read More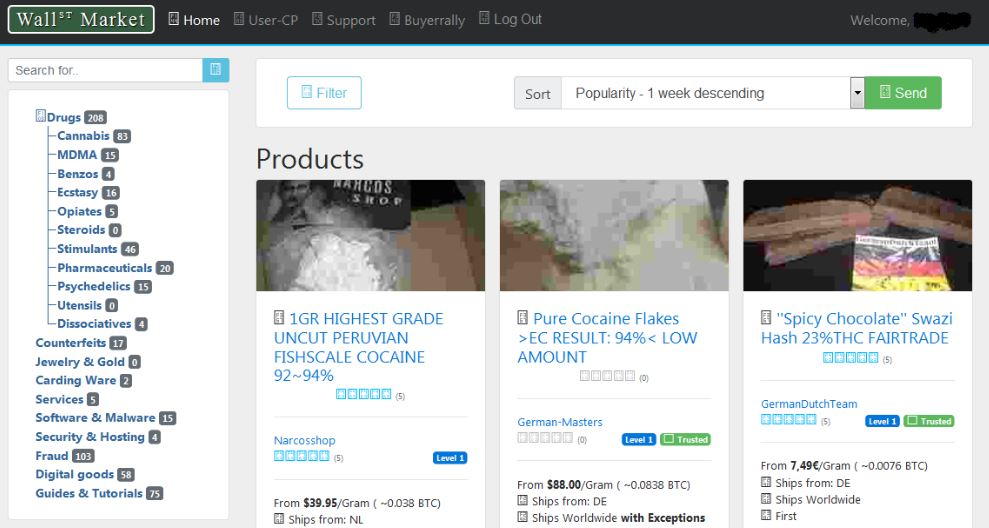
Credit to Author: BrianKrebs| Date: Fri, 03 May 2019 16:48:36 +0000
Federal investigators in the United States, Germany and the Netherlands announced today the arrest and charging of three German nationals and a Brazilian man as the alleged masterminds behind the Wall Street Market (WSM), one of the world’s largest dark web bazaars that allowed vendors to sell illegal drugs, counterfeit goods and malware. Now, at least one former WSM administrator is reportedly trying to extort money from WSM vendors and buyers (supposedly including Yours Truly) — in exchange for not publishing details of the transactions.
Read MoreCredit to Author: Trend Micro| Date: Fri, 03 May 2019 16:20:58 +0000

Online passwords are sensitive data. When they end up in the wrong hands, your private information is at risk. Since cybercriminals are always searching out new ways to break into those online accounts, you need to watch over the passwords to your accounts as if they were your children. Since we typically access our accounts…
The post Are Your Passwords Secure Enough? appeared first on .
Read MoreCredit to Author: David Ruiz| Date: Fri, 03 May 2019 15:00:00 +0000
 | |
| Here are Labs’ top six takeaways from our data privacy and cybersecurity law series on corporate data privacy compliance. From emerging startups to burgeoning enterprises, these rules help not just with legal liability, but also user trust. Categories: Tags: AppleCalifornia Online Privacy Protection Actcybersecurity lawcybersecurity lawsdata breach notificationdata breach notification lawData privacydata privacy compliancedata privacy lawdata privacy lawsdata privacy legislationgdprGeneral Data Protection RegulationHelix DNAmozillaonline privacypersonal datapersonal informationpersonally identifiable informationprivacy policyprotonmailsignalUberuser privacywhatsapp |
The post The top six takeaways for corporate data privacy compliance appeared first on Malwarebytes Labs.
Read More